Difference between revisions of "Cybercrime" - New World Encyclopedia
Rosie Tanabe (talk | contribs) |
|||
| (24 intermediate revisions by 7 users not shown) | |||
| Line 1: | Line 1: | ||
| − | {{ | + | {{Copyedited}}{{Submitted}}{{Images OK}}{{Approved}}{{Paid}} |
[[Category:Politics and social sciences]] | [[Category:Politics and social sciences]] | ||
[[Category:Law]] | [[Category:Law]] | ||
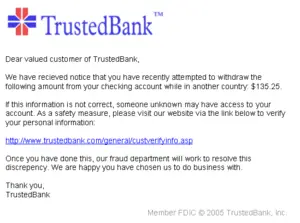
| − | '''Cybercrime''' is a term used broadly to describe activity in which [[ | + | [[Image:PhishingTrustedBank.png|thumb|300px|right|A “phishing” scam, such as the sample pictured here, is one form of '''cybercrime''']] |
| + | '''Cybercrime''' is a term used broadly to describe activity in which [[computer]]s or computer networks are the tool, target, or place of [[crime|criminal]] activity. These categories are not exclusive and many activities can be characterized as falling in one or more categories. Cybercrime takes a number of forms including [[identity theft]], internet [[fraud]], violation of [[copyright]] laws through file sharing, hacking, computer viruses, denial of service attacks, and spam. Many types of cybercrime are simply extensions of existing criminal activities, with the computer and internet severing them from the perpetrator's geographical location, providing anonymity and protection from [[law enforcement]]. | ||
| + | {{toc}} | ||
| + | While computers and the internet are valuable [[technology|technological]] advances that benefit contemporary [[society]] in numerous ways, like all tools they can be used for [[evil]] as well as [[good]]. For those who put their self-centered desires above the good of others, and of society as a whole, they offer seemingly unlimited possibilities for criminal activity. Just as with all crimes, however, it is not stricter [[law]]s or better law enforcement that will eliminate such activities, but rather a change in the hearts and minds of people to learn to live for the sake of others in a harmonious, prosperous society. | ||
| − | == | + | ==Definition== |
| − | Although the term cybercrime is usually restricted to describing criminal activity in which the computer or network is an essential part of the crime, this term is also used to include traditional crimes in which computers or networks are used to enable the illicit activity. | + | Although the term '''cybercrime''' is usually restricted to describing criminal activity in which the [[computer]] or network is an essential part of the [[crime]], this term is also used to include traditional crimes in which computers or networks are used to enable the illicit activity. Thus, cybercrime is often an extension of existing criminal activities through the involvement of computers. Some novel types of crime also exist, however, that feature the computer as an essential aspect of the crime. In all cases, a significant characteristic is its non-local character—just as the [[internet]] is not confined to any geographical location, cybercrime transcends [[jurisdiction]]s, consequently creating difficulties for [[law enforcement]]. |
| + | {{readout||right|250px|Cybercrime refers to [[crime]] that involves a [[computer]] and a network either used in the commission of the crime or as the target}} | ||
| + | Cybercrimes in which the computer or network is a tool of the criminal activity include [[Cybercrime#Spam|spam]]ming and certain [[intellectual property]] and criminal [[copyright]] crimes, particularly those facilitated through [[#Cybercrime#File sharing|peer-to-peer]] networks. | ||
| − | Examples of cybercrime | + | Examples of cybercrime where the computer or network is a target of criminal activity include unauthorized access (defeating [[access control]]s), [[Cybercrime#Computer Viruses and other Malware|malicious code]], and [[Cybercrime#Denial of service attacks|denial-of-service]] attacks. |
| − | + | Where the computer or network is the place of criminal activity, cybercrimes include theft of service and certain forms of [[Cybercrime#Internet fraud|fraud]]. | |
| − | + | Finally, examples of traditional crimes facilitated through the use of computers or networks include [[Advance fee fraud|Nigerian 419]] or other gullibility or [[social engineering]] frauds ("[[phishing]]," [[#Cybercrime#Identity theft|identity theft]], [[Cybercrime#Child Pornography|child pornography]], online [[gambling]], [[securities fraud]], and so forth). [[Cyberstalking]] is an example of a traditional crime—harassment—that has taken a new form when facilitated through computer networks. | |
| − | |||
| − | Finally, examples of traditional crimes facilitated through the use of computers or networks include [[Advance fee fraud|Nigerian 419]] or other gullibility or [[social engineering]] frauds ( | ||
Additionally, certain other information crimes, including [[trade secret]] theft and [[Industrial espionage|industrial]] or [[Economic Espionage Act of 1996|economic]] espionage, are sometimes considered cybercrimes when computers or networks are involved. | Additionally, certain other information crimes, including [[trade secret]] theft and [[Industrial espionage|industrial]] or [[Economic Espionage Act of 1996|economic]] espionage, are sometimes considered cybercrimes when computers or networks are involved. | ||
| − | Cybercrime in the context of national security may involve [[hacktivism]] (online activity intended to influence policy), traditional [[espionage]], or [[information warfare]] and related activities. | + | Cybercrime in the context of national security may involve "[[hacktivism]]" (online activity intended to influence policy), traditional [[espionage]], or [[information warfare]] and related activities. |
| − | Another way to define cybercrime is simply as criminal activity involving the information technology infrastructure, including illegal access (unauthorized access), illegal interception (by technical means of non-public transmissions of computer data to, from or within a computer system), data interference (unauthorized damaging, deletion, deterioration, alteration or suppression of computer data), systems interference (interfering with the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering or suppressing computer data), misuse of devices, forgery ( | + | Another way to define cybercrime is simply as criminal activity involving the information technology infrastructure, including illegal access (unauthorized access), illegal interception (by technical means of non-public transmissions of computer data to, from or within a computer system), data interference (unauthorized damaging, deletion, deterioration, alteration, or suppression of computer data), systems interference (interfering with the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering, or suppressing computer data), misuse of devices, [[forgery]] (identity theft), and electronic fraud. |
==Types== | ==Types== | ||
| + | Cybercrime ranges from the fundamental invasion of [[privacy]], both personal and private, to crimes where the perpetrator hides in the anonymity of the internet, to attacks on the internet or computer network itself. | ||
| + | |||
===Child Pornography=== | ===Child Pornography=== | ||
| − | The issue of child pornography has become more important due to its widespread distribution and availability on the internet. Child pornography is widely seen as a form of child abuse and its production, distribution, and possession is outlawed in most countries. Prohibition may include images or videos of children engaged in sexual acts or of nude children. Many American states have made efforts to pass legislation outlawing its transmission via the internet. | + | The issue of child [[pornography]] has become more important due to its widespread distribution and availability on the [[internet]]. Child pornography is widely seen as a form of [[child abuse]] and its production, distribution, and possession is outlawed in most countries. Prohibition may include images or videos of children engaged in [[human sexuality|sexual acts]] or of nude children. Many American states have made efforts to pass legislation outlawing its transmission via the internet. |
| − | Of the 184 members of The International Criminal Police Organization (Interpol), 95 do not have comprehensive laws covering child pornography.<ref>[http://www.icmec.org/missingkids/servlet/NewsEventServlet?LanguageCountry=en_X1&PageId=2338 | + | Of the 184 members of The International Criminal Police Organization (Interpol), 95 do not have comprehensive laws covering child pornography.<ref>[http://www.icmec.org/missingkids/servlet/NewsEventServlet?LanguageCountry=en_X1&PageId=2338 "New Study Reveals Child Pornography not a Crime in Most Countries,"] ''International Centre for Missing and Exploited Children.'' Retrieved August 2, 2007.</ref> This can be seen as simply a lack of awareness in those countries or also as a reflection of the varying [[norm]]s of sexuality around the world, where in some countries child brides are still seen as ideal. The lack of laws against child pornography in such countries has led to the use of internet hosts there for such material, safe from prosecution. |
===Computer Viruses and other Malware=== | ===Computer Viruses and other Malware=== | ||
| − | '''Malware''' is software designed to infiltrate or damage a computer system without the owner's [[informed consent]]. It is a [[portmanteau]] of the words "[[Malice (legal term)|malicious]]" and "[[Computer software|software]]." The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code. | + | '''Malware''' is software designed to infiltrate or damage a computer system without the owner's [[informed consent]]. It is a [[portmanteau]] of the words "[[Malice (legal term)|malicious]]" and "[[Computer software|software]]." The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code. The more specific term "[[computer virus]]" is however used in common parlance, and often in the [[mass media|media]], to describe all kinds of malware. |
| − | + | Software is considered malware based on the perceived intent of the creator rather than any particular features. It includes computer viruses, [[Computer worm|worms]], [[Trojan horse (computing)|trojan horse]]s, [[spyware]], dishonest [[adware]], and other malicious and unwanted software. In [[law]], malware may also be referred to as a "computer contaminant."<ref>[http://www.ncsl.org/programs/lis/cip/viruslaws.htm Virus/Contaminant/Destructive Transmission Statutes,] National Conference of State Legislatures. Retrieved August 2, 2007.</ref> | |
| − | Another strictly for-profit category of malware has emerged in [[spyware]] | + | Many early infectious programs, including the [[internet worm]] and a number of [[MS-DOS]] viruses, were written as experiments or pranks generally intended to be harmless or merely annoying rather than to cause serious damage. Since the rise of widespread [[broadband]] [[internet]] access, more malicious software has been designed for a [[profit]] motive. For instance, since 2003, the majority of widespread viruses and worms have been designed to take control of users' computers for [[black market]] exploitation. Infected "[[zombie computer]]s" are used to send [[#Spam|e-mail spam]], to host contraband data such as [[#Child Pornography|child pornography]], or to engage in [[#Denial of service attacks|distributed denial-of-service]] attacks as a form of [[extortion]].<ref>Daniel Tynan, |
| + | “Zombie PCs: Silent, Growing Threat,” ''PC World'' (July 9, 2004).</ref> | ||
| + | |||
| + | Another strictly for-profit category of malware has emerged in [[spyware]]—programs designed to monitor users' web browsing, display unsolicited [[advertising|advertisements]], or redirect [[affiliate marketing]] revenues to the spyware creator. Spyware programs do not spread like viruses; they are generally installed by exploiting security holes or are packaged with user-installed software. | ||
===Denial of service attacks=== | ===Denial of service attacks=== | ||
| − | + | A denial-of-service attack (DoS attack) is an attempt to make a computer resource unavailable to its intended users. Although the means to, motives for, and targets of a DoS attack may vary, it generally comprises the concerted, malevolent efforts of a person or persons to prevent an [[Internet]] [[Website|site]] or [[Web service|service]] from functioning efficiently or at all, temporarily or indefinitely. Perpetrators of DoS attacks typically—but not exclusively—target sites or services hosted on high-profile web servers. Denial of service attacks are one form of computer [[sabotage]] whereby people can effectively ruin their target's operations for what could be a lengthy period of time. | |
| − | + | ===File sharing=== | |
| − | + | File sharing is the practice of making [[computer file|file]]s available for other users to download over the [[internet]] and smaller [[computer network|networks]]. The duplication of [[copyright]]ed material, such as [[music]] and [[movie]]s, is well understood as illegal. However, the status of sharing computer files containing such data has been less clear. The Recording Industry Association of America (RIAA) was able to force Napster to close its music file sharing operation based on the fact that the shared files were stored on a central Napster computer. Subsequently, Napster and others have set up subscription based legal file sharing for music files. | |
| − | |||
| − | + | More controversial file sharing follows the [[peer-to-peer]] (P2P) model, where the files are stored on and served by personal computers of the users. Most people who engage in file sharing are also downloading files that other users share. Sometimes these two activities are linked together. P2P file sharing is distinct from file trading in that downloading files from a P2P network does not require uploading, although some networks either provide incentives for uploading such as credits or force the sharing of files being currently downloaded. | |
| − | + | Under U.S. [[law]], "the Betamax decision" ''([[Sony Corp. of America v. Universal City Studios, Inc.]])'', case holds that copying "technologies" are not "inherently" illegal, if substantial non-infringing use can be made of them. This decision, predating the widespread use of the [[internet]] applies to most data networks, including peer-to-peer networks, since distribution of correctly licensed files can be performed. These non-infringing uses include sending open source software, public domain files, and out of [[copyright]] works. Other [[jurisdiction]]s tend to view the situation in somewhat similar ways. | |
| − | + | In practice, many of the files shared on peer-to-peer networks are copies of copyrighted popular [[music]] and [[movie]]s. Sharing of these copies among strangers is illegal in most jurisdictions. This has led many observers, including most media companies and some peer-to-peer critics, to conclude that the networks themselves pose grave threats to the established distribution model. The research that attempts to measure actual monetary loss has been somewhat equivocal. Whilst on paper the existence of these networks results in large losses, the actual income does not seem to have changed much since these networks started up. Whether the threat is real or not, both the Recording Industry Association of America (RIAA) and the Motion Picture Association of America (MPAA) have spent large amounts of money attempting to [[lobbying|lobby]] lawmakers for the creation of new laws, and some copyright owners pay companies to help legally challenge users engaging in illegal sharing of their material. | |
| − | |||
| − | + | Countries outside of the United States have served as havens for the hosting of file sharing software as the U.S. copyright laws are often difficult to enforce in these countries.<ref>Thomas Mennecke, [http://www.slyck.com/news.php?story=838 “Supreme Court Rules Against P2P Companies,”] ''Slyck News.'' (2005). Retrieved August 2, 2007.</ref> For example, the program Kazaa is owned by the Australian company Sharman Holdings, incorporated in [[Vanuatu]], and developed by two Dutch software engineers. The online index of bit torrents The Pirate Bay is hosted in [[Sweden]] with backup servers in [[Russia]].<ref>Ann Harrison, [http://www.wired.com/science/discoveries/news/2006/03/70358 “The Pirate Bay: Here to Stay?”] ''Wired'' (March 13, 2006). Retrieved August 2, 2007.</ref> | |
| − | |||
| − | |||
| − | |||
| − | Countries outside of the United States have served as havens for the hosting of file sharing software as | ||
===Hacking=== | ===Hacking=== | ||
| − | A | + | A "hacker" is someone who gains illegal access to computers. This action can be done maliciously or with the intent of pointing out possible security risks. Microsoft Corporation, the American [[multinational corporation|multi-national]] computer technology corporation, and the [[Department of Defense]] are among those large organizations that have been the target of hackers. Hacking poses a risk to society as hackers can gain access to sensitive financial, personal, or security information that can then be used for [[extortion]] or exploited for an attack. Hacking can be understood as the cyber-version of [[industrial espionage]]. |
| − | |||
| − | |||
===Identity theft=== | ===Identity theft=== | ||
| − | + | The term "[[identity theft]]" encompasses a broad range of identification-based crimes. It can be sub-divided into four categories: financial identity theft (using another's name and Social Security number to obtain goods and services), criminal identity theft (posing as another when apprehended for a crime), identity cloning (using another's information to assume his or her identity in daily life), and business/commercial identity theft (using another's [[business]] name to obtain credit).<ref>[http://www.idtheftcenter.org/ Identity Theft Resource Center.] Retrieved July 3, 2007.</ref> | |
| − | + | There are a number of methods used by identity thieves including stealing [[mail]] or rummaging through trash, eavesdropping on public transactions to obtain personal data, stealing personal information in computer databases (Trojan horses, hacking), [[infiltration]] of organizations that store large amounts of personal information, impersonating a trusted organization in an electronic communication ("[[phishing]]"), and the use of [[#Spam|spam]]. | |
| − | The unlawful acquisition of legally attributed personal identifiers is made possible by serious breaches of [[privacy]]. For consumers it is usually due to personal | + | The unlawful acquisition of legally attributed personal identifiers is made possible by serious breaches of [[privacy]]. For consumers it is usually due to personal naiveté in who they provide their information to or carelessness in protecting their information from theft (such as vehicle break-ins and home invasions). Surveys in the United States from 2003 to 2006 showed a decrease in the total number of victims but an increase in the total value of identity fraud to US$56.6 billion in 2006. The average fraud per person rose from $5,249 in 2003 to $6,383 in 2006.<ref>[http://www.privacyrights.org/ar/idtheftsurveys.htm Recent Surveys and Studies,] Privacy Clearing House. Retrieved August 2, 2007.</ref> In the [[United Kingdom]], the Home Office Identity Fraud Steering Committee reported that identity fraud costs the UK economy £1.7 billion.<ref>[http://www.identitytheft.org.uk/ “What is Identity theft?”] Home Office Identity Fraud Steering Committee. Retrieved August 2, 2007.</ref> Confusion over exactly what constitutes identity theft has led to claims that statistics may be exaggerated.<ref>Bruce Schneier, [http://www.schneier.com/blog/archives/2005/11/identity_theft.html Identity Theft Over-Reported,] Schneier.com. Retrieved August 2, 2007.</ref> |
===Internet fraud=== | ===Internet fraud=== | ||
| − | The term " | + | The term "internet fraud" generally refers to any type of [[fraud]] scheme that uses one or more online services—such as chat rooms, e-mail, message boards, or websites—to present fraudulent solicitations to prospective victims, to conduct fraudulent transactions, or to transmit the proceeds of fraud to financial institutions or to others connected with the scheme. The [[Federal Bureau of Investigation]] and [[police]] agencies worldwide have people assigned to combat this type of fraud; according to figures from the FBI, U.S. companies' losses due to internet fraud in 2003 surpassed US$500 million. |
| − | Internet fraud is committed in several ways | + | Internet fraud is committed in several ways. In some cases, fictitious merchants advertise goods for very low prices and never deliver. However, that type of fraud is minuscule compared to [[Crime|criminal]]s using stolen [[credit card]] information to buy goods and services. |
| − | Some common types of internet fraud include identity theft, purchase scams, counterfeit money orders, | + | Some common types of internet fraud include identity theft, purchase scams, [[counterfeit]] money orders, "phishing" for sensitive information, and "clickfraud" whereby false hits are generated for websites in order to generate [[advertising]] money. |
| − | One famous category of internet fraud | + | One famous category of internet fraud consists of those offenses classified as "419 scams," named as such for the section of the [[Nigeria]]n penal code under which they fall. In these schemes, would be thieves e-mail people claiming to have a large sum of money they need to wire out of the country for some reason (large [[tax]] burden, political persecution, [[civil war]], and so forth). They request for their victims to send them the fees for transferring this fortune to the victim's account in exchange for a portion of the wealth. The victim, of course, never receives the money transfer and loses the fee money they have already sent.<ref>[http://www.419eater.com/html/419faq.htm What is the '419' Scam?] 419 Eater. Retrieved August 2, 2007.</ref> This type of scam originated with schemes in the early 1980s in Nigeria, hence the alternate name of Nigerian Money Transfer Fraud. |
===Spam=== | ===Spam=== | ||
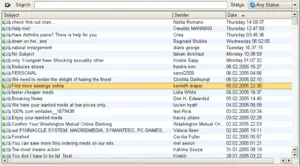
| − | [[Image:spammed-mail-folder.png|thumb|300px|A | + | [[Image:spammed-mail-folder.png|thumb|300px|A KMail folder of "spam" messages]] |
| − | + | "Spamming" is the abuse of electronic messaging systems to send unsolicited bulk messages, which are generally undesirable. While the most widely recognized form of spam is e-mail spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web [[search engine]] spam, spam in [[blog]]s, [[mobile phone]] messaging spam, internet forum spam, and junk [[fax machine|fax]] transmissions. Spam is also called junk mail. Some email clients or servers have spam filters, which try to delete or move the spam messages. | |
| + | |||
| + | Spamming is economically viable because [[advertising|advertisers]] have no operating costs beyond the management of their mailing lists, and it is difficult to hold senders accountable for their mass mailings. Because the [[barrier to entry]] is so low, spammers are numerous, and the volume of unsolicited mail has become very high. The costs, such as lost productivity and [[fraud]], are borne by the public and by [[Internet service provider]]s, which have been forced to add extra capacity to cope with the deluge. Spamming is widely reviled, and has been the subject of legislation in many jurisdictions. | ||
| − | + | E-mail and other forms of spamming have been used for purposes other than advertisements. Many early Usenet spams were [[religion|religious]] or [[politics|political]]. A number of [[evangelism|evangelists]] have spammed Usenet and e-mail media with preaching messages. A growing number of criminals are also using spam to perpetrate various sorts of fraud (see "[[Cybercrime#Internet fraud|internet fraud]]" above) and in some cases have used it to lure people to locations where they have been [[kidnapping|kidnapped]], held for ransom, and even [[murder]]ed.<ref>Beeld Philip de Bruin, [http://www.news24.com/News24/South_Africa/News/0,,2-7-1442_1641875,00.html “SA cops, Interpol probe murder,”] News24.com (2004). Retrieved August 2, 2007.</ref> | |
| − | E-mail | + | E-mail [[computer virus|worms or viruses]] may be spammed to set up an initial pool of infected machines, which resend the virus to other machines in a spam-like manner. The infected machines can often be used as remote-controlled [[zombie computers]], for more spamming, to [[phishing|phish]] for [[bank]] account details, or other attacks. |
| − | + | Spam's direct effects include the consumption of computer and network resources, and the cost in human time and attention of dismissing unwanted messages. In addition, spam has costs stemming from the kinds of spam messages sent, from the ways spammers send them, and from the "arms race" between spammers and those who try to stop or control spam. The [[European Union]]'s Internal Market Commission estimated in 2001 that "junk e-mail" cost internet users €10 billion per year worldwide.<ref>[http://europa.eu/rapid/pressReleasesAction.do?reference=IP/01/154&format=HTML&aged=0&language=EN&guiLanguage=en "Data protection: "Junk" e-mail costs internet users 10 billion a year worldwide - Commission study."] European Commission (February 2, 2001). Retrieved July 17, 2007.</ref> In addition to direct costs are the indirect costs borne by the victims—both those related to the spamming itself, and to other crimes that usually accompany it, such as financial [[theft]], [[identity theft]], data and [[intellectual property]] theft, virus and other malware infection, child pornography, fraud, and deceptive marketing. | |
| − | + | ==Prevalence of cybercrime== | |
| + | Cybercrime has become a particularly relevant problem to [[police]] around the world and to [[society]] at large. The growing presence of the [[internet]] and [[computer]]s in homes around the world means that more people are exposed to cybercrime each year. The rise in popularity of broadband internet access also means a greater risk. In an era where all data is being digitized and stored on computers, protecting computers is integral to personal and national security. | ||
| − | == | + | ==Preventing cybercrime== |
| − | + | In order to combat cybercrime a number of precautions and preventative measures may be taken. These include the use of anti-virus software on computers, [[encryption]] of data used in online and [[credit card]] sales, and increasing public awareness of the types of scams and other attacks on computers and networks. | |
==Notes== | ==Notes== | ||
| Line 95: | Line 98: | ||
== References == | == References == | ||
| − | * | + | * Dreyfus, Suelette. ''Underground: Tales of Hacking, Madness and Obsession on the Electronic Frontier.'' Mandarin, 1997. ISBN 1863305955 |
| − | * | + | * Graham, Paul. ''Hackers and Painters.'' 2004. ISBN 0596006624 |
| − | * | + | * Levy, Steven. ''Hackers: Heroes of the Computer Revolution.'' Doubleday, 1984. ISBN 0385191952 |
| − | * | + | * Slatalla, Michelle and Joshua Quittner. ''Masters of Deception: The Gang That Ruled Cyberspace.'' HarperCollins, 1995. ISBN 0060170301 |
| − | + | * Sterling, Bruce. [http://www.mit.edu/hacker/hacker.html ''The Hacker Crackdown.''] Bantam, 1992. ISBN 055308058X. Retrieved May 12, 2020. | |
| − | * | + | * Turkle, Sherry. ''The Second Self: Computers and the Human Spirit,'' new ed. Cambridge, MA: MIT Press, 1984. ISBN 0262701111 |
| − | + | * Verton, Dan. ''The Hacker Diaries : Confessions of Teenage Hackers.'' McGraw-Hill Osborne Media, 2002. ISBN 0072223642 | |
==External Links== | ==External Links== | ||
| − | + | All links retrieved January 12, 2024. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | * [https://www.justice.gov/criminal-ccips Computer Crime and Intellectual Property Section (CCIPS)] – U.S. Department of Justice | ||
| + | * [http://www.ftc.gov/bcp/edu/microsites/idtheft/ Identity Theft] – Federal Trade Commission | ||
| + | * [http://www.onguardonline.gov/ On Guard] – OnGuardOnline.gov provides practical tips from the federal government and the technology industry to help you be on guard against Internet fraud, secure your computer, and protect your personal information | ||
{{Credits|Cybercrime|131362470|Identity_theft|133371583|Internet_fraud|133383415|File_sharing|134479220|Hacker|134774806|Malware|133592383|Denial-of-service_attack|133240660|Spam_(electronic)|134818290|}} | {{Credits|Cybercrime|131362470|Identity_theft|133371583|Internet_fraud|133383415|File_sharing|134479220|Hacker|134774806|Malware|133592383|Denial-of-service_attack|133240660|Spam_(electronic)|134818290|}} | ||
Latest revision as of 06:50, 12 January 2024
Cybercrime is a term used broadly to describe activity in which computers or computer networks are the tool, target, or place of criminal activity. These categories are not exclusive and many activities can be characterized as falling in one or more categories. Cybercrime takes a number of forms including identity theft, internet fraud, violation of copyright laws through file sharing, hacking, computer viruses, denial of service attacks, and spam. Many types of cybercrime are simply extensions of existing criminal activities, with the computer and internet severing them from the perpetrator's geographical location, providing anonymity and protection from law enforcement.
While computers and the internet are valuable technological advances that benefit contemporary society in numerous ways, like all tools they can be used for evil as well as good. For those who put their self-centered desires above the good of others, and of society as a whole, they offer seemingly unlimited possibilities for criminal activity. Just as with all crimes, however, it is not stricter laws or better law enforcement that will eliminate such activities, but rather a change in the hearts and minds of people to learn to live for the sake of others in a harmonious, prosperous society.
Definition
Although the term cybercrime is usually restricted to describing criminal activity in which the computer or network is an essential part of the crime, this term is also used to include traditional crimes in which computers or networks are used to enable the illicit activity. Thus, cybercrime is often an extension of existing criminal activities through the involvement of computers. Some novel types of crime also exist, however, that feature the computer as an essential aspect of the crime. In all cases, a significant characteristic is its non-local character—just as the internet is not confined to any geographical location, cybercrime transcends jurisdictions, consequently creating difficulties for law enforcement.
Cybercrimes in which the computer or network is a tool of the criminal activity include spamming and certain intellectual property and criminal copyright crimes, particularly those facilitated through peer-to-peer networks.
Examples of cybercrime where the computer or network is a target of criminal activity include unauthorized access (defeating access controls), malicious code, and denial-of-service attacks.
Where the computer or network is the place of criminal activity, cybercrimes include theft of service and certain forms of fraud.
Finally, examples of traditional crimes facilitated through the use of computers or networks include Nigerian 419 or other gullibility or social engineering frauds ("phishing," identity theft, child pornography, online gambling, securities fraud, and so forth). Cyberstalking is an example of a traditional crime—harassment—that has taken a new form when facilitated through computer networks.
Additionally, certain other information crimes, including trade secret theft and industrial or economic espionage, are sometimes considered cybercrimes when computers or networks are involved.
Cybercrime in the context of national security may involve "hacktivism" (online activity intended to influence policy), traditional espionage, or information warfare and related activities.
Another way to define cybercrime is simply as criminal activity involving the information technology infrastructure, including illegal access (unauthorized access), illegal interception (by technical means of non-public transmissions of computer data to, from or within a computer system), data interference (unauthorized damaging, deletion, deterioration, alteration, or suppression of computer data), systems interference (interfering with the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering, or suppressing computer data), misuse of devices, forgery (identity theft), and electronic fraud.
Types
Cybercrime ranges from the fundamental invasion of privacy, both personal and private, to crimes where the perpetrator hides in the anonymity of the internet, to attacks on the internet or computer network itself.
Child Pornography
The issue of child pornography has become more important due to its widespread distribution and availability on the internet. Child pornography is widely seen as a form of child abuse and its production, distribution, and possession is outlawed in most countries. Prohibition may include images or videos of children engaged in sexual acts or of nude children. Many American states have made efforts to pass legislation outlawing its transmission via the internet.
Of the 184 members of The International Criminal Police Organization (Interpol), 95 do not have comprehensive laws covering child pornography.[1] This can be seen as simply a lack of awareness in those countries or also as a reflection of the varying norms of sexuality around the world, where in some countries child brides are still seen as ideal. The lack of laws against child pornography in such countries has led to the use of internet hosts there for such material, safe from prosecution.
Computer Viruses and other Malware
Malware is software designed to infiltrate or damage a computer system without the owner's informed consent. It is a portmanteau of the words "malicious" and "software." The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code. The more specific term "computer virus" is however used in common parlance, and often in the media, to describe all kinds of malware.
Software is considered malware based on the perceived intent of the creator rather than any particular features. It includes computer viruses, worms, trojan horses, spyware, dishonest adware, and other malicious and unwanted software. In law, malware may also be referred to as a "computer contaminant."[2]
Many early infectious programs, including the internet worm and a number of MS-DOS viruses, were written as experiments or pranks generally intended to be harmless or merely annoying rather than to cause serious damage. Since the rise of widespread broadband internet access, more malicious software has been designed for a profit motive. For instance, since 2003, the majority of widespread viruses and worms have been designed to take control of users' computers for black market exploitation. Infected "zombie computers" are used to send e-mail spam, to host contraband data such as child pornography, or to engage in distributed denial-of-service attacks as a form of extortion.[3]
Another strictly for-profit category of malware has emerged in spyware—programs designed to monitor users' web browsing, display unsolicited advertisements, or redirect affiliate marketing revenues to the spyware creator. Spyware programs do not spread like viruses; they are generally installed by exploiting security holes or are packaged with user-installed software.
Denial of service attacks
A denial-of-service attack (DoS attack) is an attempt to make a computer resource unavailable to its intended users. Although the means to, motives for, and targets of a DoS attack may vary, it generally comprises the concerted, malevolent efforts of a person or persons to prevent an Internet site or service from functioning efficiently or at all, temporarily or indefinitely. Perpetrators of DoS attacks typically—but not exclusively—target sites or services hosted on high-profile web servers. Denial of service attacks are one form of computer sabotage whereby people can effectively ruin their target's operations for what could be a lengthy period of time.
File sharing
File sharing is the practice of making files available for other users to download over the internet and smaller networks. The duplication of copyrighted material, such as music and movies, is well understood as illegal. However, the status of sharing computer files containing such data has been less clear. The Recording Industry Association of America (RIAA) was able to force Napster to close its music file sharing operation based on the fact that the shared files were stored on a central Napster computer. Subsequently, Napster and others have set up subscription based legal file sharing for music files.
More controversial file sharing follows the peer-to-peer (P2P) model, where the files are stored on and served by personal computers of the users. Most people who engage in file sharing are also downloading files that other users share. Sometimes these two activities are linked together. P2P file sharing is distinct from file trading in that downloading files from a P2P network does not require uploading, although some networks either provide incentives for uploading such as credits or force the sharing of files being currently downloaded.
Under U.S. law, "the Betamax decision" (Sony Corp. of America v. Universal City Studios, Inc.), case holds that copying "technologies" are not "inherently" illegal, if substantial non-infringing use can be made of them. This decision, predating the widespread use of the internet applies to most data networks, including peer-to-peer networks, since distribution of correctly licensed files can be performed. These non-infringing uses include sending open source software, public domain files, and out of copyright works. Other jurisdictions tend to view the situation in somewhat similar ways.
In practice, many of the files shared on peer-to-peer networks are copies of copyrighted popular music and movies. Sharing of these copies among strangers is illegal in most jurisdictions. This has led many observers, including most media companies and some peer-to-peer critics, to conclude that the networks themselves pose grave threats to the established distribution model. The research that attempts to measure actual monetary loss has been somewhat equivocal. Whilst on paper the existence of these networks results in large losses, the actual income does not seem to have changed much since these networks started up. Whether the threat is real or not, both the Recording Industry Association of America (RIAA) and the Motion Picture Association of America (MPAA) have spent large amounts of money attempting to lobby lawmakers for the creation of new laws, and some copyright owners pay companies to help legally challenge users engaging in illegal sharing of their material.
Countries outside of the United States have served as havens for the hosting of file sharing software as the U.S. copyright laws are often difficult to enforce in these countries.[4] For example, the program Kazaa is owned by the Australian company Sharman Holdings, incorporated in Vanuatu, and developed by two Dutch software engineers. The online index of bit torrents The Pirate Bay is hosted in Sweden with backup servers in Russia.[5]
Hacking
A "hacker" is someone who gains illegal access to computers. This action can be done maliciously or with the intent of pointing out possible security risks. Microsoft Corporation, the American multi-national computer technology corporation, and the Department of Defense are among those large organizations that have been the target of hackers. Hacking poses a risk to society as hackers can gain access to sensitive financial, personal, or security information that can then be used for extortion or exploited for an attack. Hacking can be understood as the cyber-version of industrial espionage.
Identity theft
The term "identity theft" encompasses a broad range of identification-based crimes. It can be sub-divided into four categories: financial identity theft (using another's name and Social Security number to obtain goods and services), criminal identity theft (posing as another when apprehended for a crime), identity cloning (using another's information to assume his or her identity in daily life), and business/commercial identity theft (using another's business name to obtain credit).[6]
There are a number of methods used by identity thieves including stealing mail or rummaging through trash, eavesdropping on public transactions to obtain personal data, stealing personal information in computer databases (Trojan horses, hacking), infiltration of organizations that store large amounts of personal information, impersonating a trusted organization in an electronic communication ("phishing"), and the use of spam.
The unlawful acquisition of legally attributed personal identifiers is made possible by serious breaches of privacy. For consumers it is usually due to personal naiveté in who they provide their information to or carelessness in protecting their information from theft (such as vehicle break-ins and home invasions). Surveys in the United States from 2003 to 2006 showed a decrease in the total number of victims but an increase in the total value of identity fraud to US$56.6 billion in 2006. The average fraud per person rose from $5,249 in 2003 to $6,383 in 2006.[7] In the United Kingdom, the Home Office Identity Fraud Steering Committee reported that identity fraud costs the UK economy £1.7 billion.[8] Confusion over exactly what constitutes identity theft has led to claims that statistics may be exaggerated.[9]
Internet fraud
The term "internet fraud" generally refers to any type of fraud scheme that uses one or more online services—such as chat rooms, e-mail, message boards, or websites—to present fraudulent solicitations to prospective victims, to conduct fraudulent transactions, or to transmit the proceeds of fraud to financial institutions or to others connected with the scheme. The Federal Bureau of Investigation and police agencies worldwide have people assigned to combat this type of fraud; according to figures from the FBI, U.S. companies' losses due to internet fraud in 2003 surpassed US$500 million.
Internet fraud is committed in several ways. In some cases, fictitious merchants advertise goods for very low prices and never deliver. However, that type of fraud is minuscule compared to criminals using stolen credit card information to buy goods and services.
Some common types of internet fraud include identity theft, purchase scams, counterfeit money orders, "phishing" for sensitive information, and "clickfraud" whereby false hits are generated for websites in order to generate advertising money.
One famous category of internet fraud consists of those offenses classified as "419 scams," named as such for the section of the Nigerian penal code under which they fall. In these schemes, would be thieves e-mail people claiming to have a large sum of money they need to wire out of the country for some reason (large tax burden, political persecution, civil war, and so forth). They request for their victims to send them the fees for transferring this fortune to the victim's account in exchange for a portion of the wealth. The victim, of course, never receives the money transfer and loses the fee money they have already sent.[10] This type of scam originated with schemes in the early 1980s in Nigeria, hence the alternate name of Nigerian Money Transfer Fraud.
Spam
"Spamming" is the abuse of electronic messaging systems to send unsolicited bulk messages, which are generally undesirable. While the most widely recognized form of spam is e-mail spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, mobile phone messaging spam, internet forum spam, and junk fax transmissions. Spam is also called junk mail. Some email clients or servers have spam filters, which try to delete or move the spam messages.
Spamming is economically viable because advertisers have no operating costs beyond the management of their mailing lists, and it is difficult to hold senders accountable for their mass mailings. Because the barrier to entry is so low, spammers are numerous, and the volume of unsolicited mail has become very high. The costs, such as lost productivity and fraud, are borne by the public and by Internet service providers, which have been forced to add extra capacity to cope with the deluge. Spamming is widely reviled, and has been the subject of legislation in many jurisdictions.
E-mail and other forms of spamming have been used for purposes other than advertisements. Many early Usenet spams were religious or political. A number of evangelists have spammed Usenet and e-mail media with preaching messages. A growing number of criminals are also using spam to perpetrate various sorts of fraud (see "internet fraud" above) and in some cases have used it to lure people to locations where they have been kidnapped, held for ransom, and even murdered.[11]
E-mail worms or viruses may be spammed to set up an initial pool of infected machines, which resend the virus to other machines in a spam-like manner. The infected machines can often be used as remote-controlled zombie computers, for more spamming, to phish for bank account details, or other attacks.
Spam's direct effects include the consumption of computer and network resources, and the cost in human time and attention of dismissing unwanted messages. In addition, spam has costs stemming from the kinds of spam messages sent, from the ways spammers send them, and from the "arms race" between spammers and those who try to stop or control spam. The European Union's Internal Market Commission estimated in 2001 that "junk e-mail" cost internet users €10 billion per year worldwide.[12] In addition to direct costs are the indirect costs borne by the victims—both those related to the spamming itself, and to other crimes that usually accompany it, such as financial theft, identity theft, data and intellectual property theft, virus and other malware infection, child pornography, fraud, and deceptive marketing.
Prevalence of cybercrime
Cybercrime has become a particularly relevant problem to police around the world and to society at large. The growing presence of the internet and computers in homes around the world means that more people are exposed to cybercrime each year. The rise in popularity of broadband internet access also means a greater risk. In an era where all data is being digitized and stored on computers, protecting computers is integral to personal and national security.
Preventing cybercrime
In order to combat cybercrime a number of precautions and preventative measures may be taken. These include the use of anti-virus software on computers, encryption of data used in online and credit card sales, and increasing public awareness of the types of scams and other attacks on computers and networks.
Notes
- ↑ "New Study Reveals Child Pornography not a Crime in Most Countries," International Centre for Missing and Exploited Children. Retrieved August 2, 2007.
- ↑ Virus/Contaminant/Destructive Transmission Statutes, National Conference of State Legislatures. Retrieved August 2, 2007.
- ↑ Daniel Tynan, “Zombie PCs: Silent, Growing Threat,” PC World (July 9, 2004).
- ↑ Thomas Mennecke, “Supreme Court Rules Against P2P Companies,” Slyck News. (2005). Retrieved August 2, 2007.
- ↑ Ann Harrison, “The Pirate Bay: Here to Stay?” Wired (March 13, 2006). Retrieved August 2, 2007.
- ↑ Identity Theft Resource Center. Retrieved July 3, 2007.
- ↑ Recent Surveys and Studies, Privacy Clearing House. Retrieved August 2, 2007.
- ↑ “What is Identity theft?” Home Office Identity Fraud Steering Committee. Retrieved August 2, 2007.
- ↑ Bruce Schneier, Identity Theft Over-Reported, Schneier.com. Retrieved August 2, 2007.
- ↑ What is the '419' Scam? 419 Eater. Retrieved August 2, 2007.
- ↑ Beeld Philip de Bruin, “SA cops, Interpol probe murder,” News24.com (2004). Retrieved August 2, 2007.
- ↑ "Data protection: "Junk" e-mail costs internet users 10 billion a year worldwide - Commission study." European Commission (February 2, 2001). Retrieved July 17, 2007.
ReferencesISBN links support NWE through referral fees
- Dreyfus, Suelette. Underground: Tales of Hacking, Madness and Obsession on the Electronic Frontier. Mandarin, 1997. ISBN 1863305955
- Graham, Paul. Hackers and Painters. 2004. ISBN 0596006624
- Levy, Steven. Hackers: Heroes of the Computer Revolution. Doubleday, 1984. ISBN 0385191952
- Slatalla, Michelle and Joshua Quittner. Masters of Deception: The Gang That Ruled Cyberspace. HarperCollins, 1995. ISBN 0060170301
- Sterling, Bruce. The Hacker Crackdown. Bantam, 1992. ISBN 055308058X. Retrieved May 12, 2020.
- Turkle, Sherry. The Second Self: Computers and the Human Spirit, new ed. Cambridge, MA: MIT Press, 1984. ISBN 0262701111
- Verton, Dan. The Hacker Diaries : Confessions of Teenage Hackers. McGraw-Hill Osborne Media, 2002. ISBN 0072223642
External Links
All links retrieved January 12, 2024.
- Computer Crime and Intellectual Property Section (CCIPS) – U.S. Department of Justice
- Identity Theft – Federal Trade Commission
- On Guard – OnGuardOnline.gov provides practical tips from the federal government and the technology industry to help you be on guard against Internet fraud, secure your computer, and protect your personal information
Credits
New World Encyclopedia writers and editors rewrote and completed the Wikipedia article in accordance with New World Encyclopedia standards. This article abides by terms of the Creative Commons CC-by-sa 3.0 License (CC-by-sa), which may be used and disseminated with proper attribution. Credit is due under the terms of this license that can reference both the New World Encyclopedia contributors and the selfless volunteer contributors of the Wikimedia Foundation. To cite this article click here for a list of acceptable citing formats.The history of earlier contributions by wikipedians is accessible to researchers here:
- Cybercrime history
- Identity_theft history
- Internet_fraud history
- File_sharing history
- Hacker history
- Malware history
- Denial-of-service_attack history
- Spam_(electronic) history
The history of this article since it was imported to New World Encyclopedia:
Note: Some restrictions may apply to use of individual images which are separately licensed.