|
|
| (32 intermediate revisions by 9 users not shown) |
| Line 1: |
Line 1: |
| − | {{Claimed}}{{Started}} | + | {{Copyedited}}{{Submitted}}{{Images OK}}{{Approved}}{{Paid}} |
| | [[Category:Politics and social sciences]] | | [[Category:Politics and social sciences]] |
| | [[Category:Law]] | | [[Category:Law]] |
| | | | |
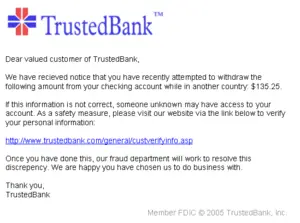
| | + | [[Image:PhishingTrustedBank.png|thumb|300px|right|A “phishing” scam, such as the sample pictured here, is one form of '''cybercrime''']] |
| | + | '''Cybercrime''' is a term used broadly to describe activity in which [[computer]]s or computer networks are the tool, target, or place of [[crime|criminal]] activity. These categories are not exclusive and many activities can be characterized as falling in one or more categories. Cybercrime takes a number of forms including [[identity theft]], internet [[fraud]], violation of [[copyright]] laws through file sharing, hacking, computer viruses, denial of service attacks, and spam. Many types of cybercrime are simply extensions of existing criminal activities, with the computer and internet severing them from the perpetrator's geographical location, providing anonymity and protection from [[law enforcement]]. |
| | + | {{toc}} |
| | + | While computers and the internet are valuable [[technology|technological]] advances that benefit contemporary [[society]] in numerous ways, like all tools they can be used for [[evil]] as well as [[good]]. For those who put their self-centered desires above the good of others, and of society as a whole, they offer seemingly unlimited possibilities for criminal activity. Just as with all crimes, however, it is not stricter [[law]]s or better law enforcement that will eliminate such activities, but rather a change in the hearts and minds of people to learn to live for the sake of others in a harmonious, prosperous society. |
| | | | |
| − | '''Cybercrime''' is a term used broadly to describe activity in which [[computers]] or [[computer network|networks]] are a tool, a target, or a place of criminal activity. These categories are not exclusive and many activities can be characterized as falling in one or more categories. | + | ==Definition== |
| | + | Although the term '''cybercrime''' is usually restricted to describing criminal activity in which the [[computer]] or network is an essential part of the [[crime]], this term is also used to include traditional crimes in which computers or networks are used to enable the illicit activity. Thus, cybercrime is often an extension of existing criminal activities through the involvement of computers. Some novel types of crime also exist, however, that feature the computer as an essential aspect of the crime. In all cases, a significant characteristic is its non-local character—just as the [[internet]] is not confined to any geographical location, cybercrime transcends [[jurisdiction]]s, consequently creating difficulties for [[law enforcement]]. |
| | + | {{readout||right|250px|Cybercrime refers to [[crime]] that involves a [[computer]] and a network either used in the commission of the crime or as the target}} |
| | + | Cybercrimes in which the computer or network is a tool of the criminal activity include [[Cybercrime#Spam|spam]]ming and certain [[intellectual property]] and criminal [[copyright]] crimes, particularly those facilitated through [[#Cybercrime#File sharing|peer-to-peer]] networks. |
| | | | |
| − | ==Overview==
| + | Examples of cybercrime where the computer or network is a target of criminal activity include unauthorized access (defeating [[access control]]s), [[Cybercrime#Computer Viruses and other Malware|malicious code]], and [[Cybercrime#Denial of service attacks|denial-of-service]] attacks. |
| − | Although the term cybercrime is usually restricted to describing criminal activity in which the computer or network is an essential part of the crime, this term is also used to include traditional crimes in which computers or networks are used to enable the illicit activity.
| |
| | | | |
| − | :Examples of cybercrime in which the computer or network is a tool of the criminal activity include [[spamming]] and certain [[intellectual property]] and criminal [[copyright]] crimes, particularly those facilitated through [[peer-to-peer]] networks.
| + | Where the computer or network is the place of criminal activity, cybercrimes include theft of service and certain forms of [[Cybercrime#Internet fraud|fraud]]. |
| | | | |
| − | :Examples of cybercrime in which the computer or network is a target of criminal activity include unauthorized access (i.e, defeating [[access control]]s), [[malware|malicious code]], and [[denial-of-service]] attacks.
| + | Finally, examples of traditional crimes facilitated through the use of computers or networks include [[Advance fee fraud|Nigerian 419]] or other gullibility or [[social engineering]] frauds ("[[phishing]]," [[#Cybercrime#Identity theft|identity theft]], [[Cybercrime#Child Pornography|child pornography]], online [[gambling]], [[securities fraud]], and so forth). [[Cyberstalking]] is an example of a traditional crime—harassment—that has taken a new form when facilitated through computer networks. |
| − | | |
| − | :Examples of cybercrime in which the computer or network is a place of criminal activity include theft of service (in particular, [[phreaking|telecom fraud]]) and certain financial frauds.
| |
| − | | |
| − | :Finally, examples of traditional crimes facilitated through the use of computers or networks include [[Advance fee fraud|Nigerian 419]] or other gullibility or [[social engineering]] frauds (e.g., "[[phishing]]"), [[identity theft]], [[child pornography]], [[online gambling]], [[securities fraud]], etc. [[Cyberstalking]] is an example of a traditional crime — harassment — that has taken a new form when facilitated through computer networks.
| |
| | | | |
| | Additionally, certain other information crimes, including [[trade secret]] theft and [[Industrial espionage|industrial]] or [[Economic Espionage Act of 1996|economic]] espionage, are sometimes considered cybercrimes when computers or networks are involved. | | Additionally, certain other information crimes, including [[trade secret]] theft and [[Industrial espionage|industrial]] or [[Economic Espionage Act of 1996|economic]] espionage, are sometimes considered cybercrimes when computers or networks are involved. |
| | | | |
| − | Cybercrime in the context of national security may involve [[hacktivism]] (online activity intended to influence policy), traditional [[espionage]], or [[information warfare]] and related activities. | + | Cybercrime in the context of national security may involve "[[hacktivism]]" (online activity intended to influence policy), traditional [[espionage]], or [[information warfare]] and related activities. |
| − | | |
| − | Another way to define cybercrime is simply as criminal activity involving the information technology infrastructure, including illegal access (unauthorized access), illegal interception (by technical means of non-public transmissions of computer data to, from or within a computer system), data interference (unauthorized damaging, deletion, deterioration, alteration or suppression of computer data), systems interference (interfering with the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering or suppressing computer data), misuse of devices, forgery (ID theft), and electronic fraud.
| |
| − | | |
| − | ==Applicable laws==
| |
| − | ===United States===
| |
| − | | |
| − | *ACCESS DEVICE FRAUD. [http://www.law.cornell.edu/uscode/html/uscode18/usc_sec_18_00001029----000-.html 18 U.S.C. § 1029]. Fraud and related activity in connection with access devices.
| |
| − | | |
| − | *COMPUTER FRAUD AND ABUSE ACT. [http://www.law.cornell.edu/uscode/html/uscode18/usc_sec_18_00001030----000-.html 18 U.S.C. § 1030]. Fraud and related activity in connection with computers.
| |
| − | | |
| − | *CAN-SPAM ACT. [http://www.law.cornell.edu/uscode/html/uscode18/usc_sec_18_00001037----000-.html 18 U.S.C. § 1037]. Fraud and related activity in connection with electronic mail.
| |
| − | | |
| − | *EXTORTION AND THREATS. [http://www.law.cornell.edu/uscode/html/uscode18/usc_sec_18_00000875----000-.html 18 U.S.C. § 875]. EXTORTION and THREATS. Interstate communications.
| |
| − | | |
| − | *IDENTITY THEFT AND ASSUMPTION DETERRENCE ACT of 1998. [http://www.law.cornell.edu/uscode/html/uscode18/usc_sec_18_00001028----000-.html 18 U.S.C. § 1028]. Fraud and related activity in connection with identification documents, authentication features, and information.
| |
| − | | |
| − | *WIRE FRAUD. [http://www.law.cornell.edu/uscode/html/uscode18/usc_sec_18_00001343----000-.html 18 U.S.C. § 1343]. Fraud by wire, radio, or television.
| |
| − | | |
| − | *No Electronic Theft ("NET") Act. [http://www.law.cornell.edu/uscode/html/uscode17/usc_sec_17_00000506----000-.html 17 U.S.C. § 506]. Criminal Offenses. (criminal copyright infringement)
| |
| − | | |
| − | *DMCA . [http://www.law.cornell.edu/uscode/html/uscode17/usc_sec_17_00001201----000-.html 17 U.S.C. § 1201]. Circumvention of copyright protection systems.
| |
| − | | |
| − | *Electronic Communications Privacy Act, [http://www.law.cornell.edu/uscode/html/uscode18/usc_sup_01_18_10_I_20_121.html 18 U.S.C. § 2701, et seq]. (STORED WIRE AND ELECTRONIC COMMUNICATIONS AND TRANSACTIONAL RECORDS ACCESS)
| |
| − | | |
| − | *Trade Secrets Act. [http://www.law.cornell.edu/uscode/html/uscode18/usc_sec_18_00001832----000-.html 18 U.S.C. § 1832]. Theft of trade secrets.
| |
| − | | |
| − | *Economic Espionage Act. [http://www.law.cornell.edu/uscode/html/uscode18/usc_sec_18_00001831----000-.html 18 U.S.C. § 1831]. Economic Espionage.
| |
| − | | |
| − | *[http://nsi.org/Library/Compsec/computerlaw/statelaws.html US Computer Crime Laws by State]
| |
| − | | |
| − | ===United Kingdom===
| |
| − | | |
| − | *The [[Computer Misuse Act 1990]] in the [[United Kingdom|UK]] (Amended in the [[Police and Justice Act 2006]])
| |
| − | | |
| − | ===Australia===
| |
| − | | |
| − | *[http://www.austlii.edu.au/au/legis/cth/consol_act/ca2001112/sch1.html ''Cybercrime Act 2001'' (Commonwealth)]
| |
| − | *[http://www.austlii.edu.au/au/legis/nsw/consol_act/ca190082/ ''Crimes Act 1900'' (NSW)]: Part 6, ss 308-308I.
| |
| − | *[http://www.austlii.edu.au/au/legis/wa/consol_act/cc94/s440a.html ''Criminal Code'' (WA): Section 440a, Unlawful Operation of a Computer System]
| |
| − | | |
| − | ===Others===
| |
| − | | |
| − | *[http://conventions.coe.int/Treaty/Commun/QueVoulezVous.asp?NT=185&CM=8&DF=20/12/01&CL=ENG Council of Europe Convention on Cybercrime]
| |
| − | *[http://www.cybercrimelaw.net/laws/survey.html Global Survey of Cybercrime Law]
| |
| − | *[http://www.mosstingrett.no/info/legal.html Unauthorized Access Penal Laws in 44 Countries]
| |
| − | | |
| − | *[[Convention on Cybercrime]]
| |
| − | *[http://www.privacy.org/pi/issues/cybercrime/coe/cybercrime27.doc Council of Europe - Draft Convention on cyber-crime (Draft N° 27)]
| |
| − | | |
| − | | |
| − | | |
| − | ==Identity theft==
| |
| − | | |
| − | '''Identity taker''' is a term first appearing in U.S. literature in the 1990s, leading to the drafting of the Identity Theft and Assumption Deterrence Act.<ref>http://www.ftc.gov/os/statutes/itada/itadact.htm Public Law 105-318, 112 Stat. 3007 (Oct. 30, 1998)</ref>
| |
| − | | |
| − | In 1998, The Federal Trade Commission appeared before the Subcommittee on Technology, Terrorism and Government Information of the Committee of the Judiciary, United States Senate.<ref>http://www.ftc.gov/os/1998/05/identhef.htm Prepared Statement of the Federal Trade Commission on "Identity Theft" May 20, 1998</ref> The FTC highlighted the concerns of consumers for financial crimes exploiting their credit worthiness to commit '''loan fraud, [[mortgage fraud]], lines-of-credit fraud, [[credit card fraud]], commodities and services frauds.'''
| |
| − | With the rising awareness of consumers to an international problem, in particular through a proliferation of web sites and the media, the term "identity theft" has since morphed to encompass a much broader range of identification-based crimes. The more traditional crimes range from dead beat dads avoiding their financial obligations, to providing the police with stolen or forged documents thereby avoiding detection, money laundering, trafficking in human beings, stock market manipulation and even to terrorism.
| |
| − | | |
| − | According to the non-profit [http://www.idtheftcenter.org/cresources.shtml Identity Theft Resource Center], identity theft is "sub-divided into four categories: Financial Identity Theft (using another's name and SSN to obtain goods and services), Criminal Identity Theft (posing as another when apprehended for a crime), Identity Cloning (using another's information to assume his or her identity in daily life) and Business/Commercial Identity Theft (using another's business name to obtain credit)."
| |
| − | | |
| − | The Identity Theft and Assumption Deterrence Act (2003)[ITADA] amended the U.S. Code, s. 1028 - "Fraud related to activity in connection with identification documents, authentication features, and information." The Code now makes possession of any "means of identification" to "knowingly transfer, possess, or use without lawful authority" a federal crime, alongside unlawful possession of identification documents.
| |
| − | | |
| − | Some people prefer the term "identity fraud" to describe when their means of identification has been exploited for an unlawful purpose. Others believe the thief ''does'' deprive the owner of his identity by replacing his reputation with the thief's. Both uses of the term focus on the act of acquiring the legally attributed personal identifiers and other personal information necessary to perpetrate the impersonation.<ref>[http://www.usdoj.gov/criminal/fraud/idtheft.html#What%20Are%20Identity%20Theft%20and%20Identity What Are Identity Theft and Identity Fraud?], [[United States Department of Justice]], retrieved June 30,2006</ref>
| |
| − | | |
| − | A classic example of consumer-dependent financial crime occurs when Bob obtains a loan from a financial institution impersonating Peter. Bob uses Peter's personal identifiers that he has somehow acquired. These personal identifiers conform with the data retained on Peter by national credit-rating services. The identifiers include surname, given names, date of birth, Social Security number (U.S.), Social Insurance Number (Cda), current and former addresses etc. These data are all part of credit header information retained by credit-rating services. The crimes are self-revealing. When Peter defaults on payments the lenders become aware. With consumers being credit-dependent, the onus shifts to them to re-establish their credit-worthiness with the lending institutions and credit-rating services.
| |
| − | | |
| − | Less commonly understood outside criminal intelligence and law enforcement circles is the impact of identification-based concealment crimes. As with credit-dependent consumer financial crimes, criminals acquire legally attributed personal identifiers and then clone someone to them for concealment from authorities. Unlike credit-dependent financial crimes, they are non self-revealing, continuing for an indeterminate amount of time without being detected.
| |
| − | | |
| − | The crimes include [[illegal immigration]], [[terrorism]] and [[espionage]], to mention a few. It may also be a means of [[blackmail]] if activities undertaken by the [[thief]] in the name of the victim would have serious consequences for the victim. There are cases of identity cloning to attack payment systems, such as obtaining medical treatment.
| |
| − | | |
| − | | |
| − | | |
| − | ===Personal Guardianship===
| |
| − | The unlawful acquisition of legally attributed personal identifiers is made possible by serious breaches of [[privacy]]. For consumers it is usually due to personal naivete in who they provide their information to or carelessness in protecting their information from theft (e.g. vehicle break-ins and home invasions). Guardianship of personal identifiers by consumers is the most common intervention strategy recommended by the Federal Trade Commission, Canadian Phone Busters and most sites that address "identity theft." Personal guardianship issues include recommendations on what consumers may do to prevent their information getting into the wrong hands.
| |
| − | | |
| − | ===Agency Guardianship===
| |
| − | | |
| − | Governments trade off diligence in issuing both foundation and other means of identification documents providing access to benefits, privileges and services, for delivery of smooth and efficient services to their clients.
| |
| − | | |
| − | In their May 1998 testimony on Identity Theft before a subcommittee of the Committee of the Judiciary, United States Senate, the Federal Trade Commission (FTC) reported on their response to consumer concern about the sale of their Social Security numbers and other personal identifiers by the individual reference service industry [credit-raters and data miners]. The FTC agreed to the industry's draft of self-regulating principles restricting access to non-public information which includes "credit header" information on credit reports. The credit header data typically includes the individual's name, address, aliases, Social Security number, current and prior addresses and telephone number.<ref>http://www.ftc.gov/os/1998/05/identhef.htm Testimony before the Subcommittee on Technology, Terrorism and Government Information, Committee of the Judiciary, United States Senate May 20, 1998 pp 5,6</ref> According the industry the restrictions vary according to the category of customer. Credit-rating services gather and disclosure personal and credit information to a wide business client base.
| |
| − | | |
| − | Governments, in registering sole proprietorships, partnerships and corporations do not make an effort to determine if the officers listed in the Articles of Incorporation are who they say they are, potentially allowing criminals access to personal information through credit-rating and data mining services. Other poor corporate diligence standards include: i) a failure to shred confidential information before throwing it into dumpsters; ii) the brokerage of personal information to other businesses without ensuring that the purchaser maintains adequate security controls; and iii) the theft of laptop computers being carried off-site containing vast amounts of personal information.
| |
| − | | |
| − | If corporate or government organizations do not protect [[consumer privacy]], [[client confidentiality]] and [[political privacy]], the acquisition of personal identifiers to commit unlawful acts will continue to be a prime target for criminals.<ref>[http://www.siia.net/software/pubs/iit-00.pdf Internet Identity Theft - A Tragedy for Victims], [[Software and Information Industry Association]], retrieved June 30,2006</ref>
| |
| − | | |
| − | ===Legal response===
| |
| − | | |
| − | In the [[United Kingdom]] personal data is protected by the [[Data Protection Act]]. The Act covers all personal data which an organization may hold, including names, birthday and anniversary dates, addresses, telephone numbers, etc.
| |
| − | | |
| − | Under [[English law]], the [[deception offenses]] under the [[Theft Act 1968]] increasingly contend with identity theft situations. In ''R v Seward'' (2005) EWCA Crim 1941<ref>[http://www.bailii.org/ew/cases/EWCA/Crim/2005/1941.html R v Seward (2005) EWCA Crim 1941]</ref> the defendant was acting as the "front man" in the use of stolen credit cards and other documents to obtain goods. He obtained goods to the value of £10,000 for others who are unlikely ever to be identified. The Court of Appeal considered sentencing policy for deception offenses involving "identity theft" and concluded that a prison sentence was required. Henriques J. said at para 14:"Identity fraud is a particularly pernicious and prevalent form of dishonesty calling for, in our judgment, deterrent sentences."
| |
| − | | |
| − | In [[Australia]], privacy law is the responsibility of the Office of the Privacy Commissioner.<ref>[http://www.privacy.gov.au/ Privacy Commissioner], retrieved June 30,2006</ref>
| |
| − | | |
| − | In the [[USA]], until 2003, dealing with consumer crimes involving legally attributed personal identifiers was the jurisdictional responsibility of the local and state authorities. Identification documents are a different story, addressed in Title 18 > Part I > Chapter 47 s.1028 of the U.S. Code. The unlawful use of identification documents is historically a federal offence. In response to the consumer issue of "identity theft," the U.S. Congress passed the Identity Theft and Assumption Deterrence Act (2003) amending Title 18 > Part I > Chapter 47, s. 1028 to include the unlawful use of a "means of identification" [s,1028 (d)(7)] making it a federal crime alongside identification documents. The title of s.1028 is, "Fraud related to activity in connection with identification documents, authentication features, and information." The Act also provides the [[Federal Trade Commission]] with authority to track the number of incidents and the dollar value of losses. There figures relate mainly to consumer financial crimes and not the broader range of all identification-based crimes.<ref>[http://www.consumer.gov/idtheft/ Federal Trade Commission], retrieved June 30,2006</ref>'''
| |
| − | Punishments for the unlawful use of a "means of identification" were strengthened in s.1028a, allowing for a consecutive sentence under specific conditions of a felony violation defined in s. 1028c.
| |
| − | | |
| − | If used to commit another crime in the commission of identity theft in the United States (if charged federally) include:
| |
| − | *Class B Felony: 6-20 years in Jail and a fine up to $10,000
| |
| − | *Class C Felony: 2-8 years in Jail and a fine up to $10,000
| |
| − | If charges are brought by state or local law enforcement agencies, different penalties apply depending on the state.
| |
| − | | |
| − | In France, a person convicted of identity theft can be sentenced upto 5 years in prison and fined upto [[euro|€]]75,000.[http://www.journaldunet.com/juridique/juridique040309.shtml]
| |
| − | | |
| − | ===Techniques for obtaining information===
| |
| − | | |
| − | *stealing mail or rummaging through rubbish ([[dumpster diving]])
| |
| − | *eavesdropping on public transactions to obtain personal data ([[Shoulder surfing (computer security)|shoulder surfing]])
| |
| − | *stealing personal information in computer databases [Trojan horses, hacking]
| |
| − | *[[infiltration]] of organizations that store large amounts of personal information
| |
| − | *impersonating a trusted organization in an electronic communication ([[phishing]])
| |
| − | * [[Spam (electronic)]]: Some, if not all spam requires you to respond to alleged contests, enter into "Good Deals," etc.
| |
| − | *using another arguably illegal reason to victimize individuals who display their personal information in [[good faith]], such as landlord-related fraud, where the [[Patriot Act]] is used to create suspicion on prospective tenants, and then using their personal information to commit fraud. This is a very common practice among [[landlord|slumlords]], who violate [[civil rights]] and use the right to request [[background checks]] to defend their legal policies, which are later used to commit crimes; the laws themselves create this conflict and is a type of identity theft created and enforced by [[federal law]].
| |
| − | | |
| − | ===Spread and impact of consumer-based "identity theft"===
| |
| − | | |
| − | Surveys in the USA from 2003 to 2006 showed a decrease in the total number of victims but an increase in the total value of identity fraud to US$56.6 billion in 2006. The average fraud per person rose from $5,249 in 2003 to $6,383 in 2006.<ref>[http://www.privacyrights.org/ar/idtheftsurveys.htm Recent Surveys and Studies], Privacy Clearing House, retrieved June 30,2006</ref>
| |
| − | | |
| − | The 2003 survey from the [http://www.idtheftcenter.org Identity Theft Resource Centre] found that :
| |
| − | * Only 15% of victims find out about the theft through proactive action taken by a business
| |
| − | * The average time spent by victims resolving the problem is about 600 hours
| |
| − | * 73% of respondents indicated the crime involved the thief acquiring a credit card
| |
| − | * The emotional impact is similar to that of victims of violent crimes
| |
| − | In a widely publicized account,<ref>[http://www.privacyrights.org/cases/victim9.htm Verbal Testimony by Michelle Brown], July 2000, U.S. Senate Committee Hearing on the Judiciary Subcommittee on Technology, Terrorism and Government Information — "Identity Theft: How to Protect and Restore Your Good Name"</ref> Michelle Brown, a victim of identity fraud, testified before a U.S. Senate Committee Hearing on Identity Theft. Ms. Brown testified that: "over a year and a half from January 1998 through July 1999, one individual impersonated me to procure over $50,000 in goods and services. Not only did she damage my credit, but she escalated her crimes to a level that I never truly expected: she engaged in drug trafficking. The crime resulted in my erroneous arrest record, a warrant out for my arrest, and eventually, a prison record when she was booked under my name as an inmate in the Chicago Federal Prison."
| |
| − | | |
| − | In Australia, identity theft was estimated to be worth between AUS$1billion and AUS$4 billion per annum in 2001.<ref>[http://www.acpr.gov.au/research_idcrime.asp Identity Crime Research and Coordination], Australasian Centre for Policing Research, retrieved June 30,2006</ref>
| |
| − | | |
| − | In the United Kingdom the Home Office reported that identity fraud costs the UK economy £1.7 billion<ref>[http://www.identitytheft.org.uk/ What is Identity theft?],[[Home Office]],retrieved June 30,2006</ref> although privacy groups object to the validity of these numbers, arguing that they are being used by the government to push for introduction of national ID cards. {{Fact|date=February 2007}} Confusion over exactly what constitutes identity theft has led to claims that statistics may be exaggerated.<ref> [http://www.schneier.com/blog/archives/2005/11/identity_theft.html Identity Theft Over-Reported],[[Bruce Schneier]], retrieved June 30,2006</ref>
| |
| − | | |
| − | === In popular culture ===
| |
| − | | |
| − | *The public fascination with impostors has long had an effect on [[popular culture]] and extends to modern literature.
| |
| − | *Across the ages there have been many cases of "identity theft"
| |
| − | *The story of Michelle Brown has been made into a film.<ref>[http://www.imdb.com/title/tt0430211/ Identity Theft: The Michelle Brown Story (2004)]</ref>
| |
| − | *In [[Frederick Forsyth]]'s novel [[The Day of the Jackal]] the would-be assassin of [[Charles de Gaulle|General de Gaulle]] steals three identities. Firstly, he assumes the identity of a dead child by obtaining the child's [[birth certificate]] and using it to apply for a [[passport]]. He also steals the passports of a Danish clergyman and an American tourist, and disguises himself as each of those persons in turn.
| |
| − | *In the 1995 movie ''[[The Net (film)|The Net]]'', [[Sandra Bullock]] plays a computer consultant whose life is taken over with the help of computer assisted identity theft.
| |
| − | *In [[Jonathan Smith]]'s novel [[Night Windows]] the action is based on the horrific and real life theft of Smith's own identity.
| |
| − | | |
| − | *Protection - Find resources provided by the FDIC to educate and protect consumers, revitalize communities, and promote compliance with the Community Reinvestment Act and fair lending laws. Tips, and ways to help protect yourself from online identity theft can be found at www.fdic.gov
| |
| − | | |
| − | ==Internet fraud==
| |
| − | {{Unreferenced|article|date=January 2007}}
| |
| − | The term "'''Internet fraud'''" generally refers to any type of fraud scheme that uses one or more online services - such as chat rooms, e-mail, message boards, or Web sites - to present fraudulent solicitations to prospective victims, to conduct fraudulent transactions, or to transmit the proceeds of fraud to financial institutions or to others connected with the scheme.
| |
| − | | |
| − | | |
| − | Internet fraud is committed in several ways. The [[FBI]] and police agencies worldwide have people assigned to combat this type of [[fraud]]; according to figures from the FBI, U.S. companies' losses due to Internet fraud in 2003 surpassed [[US dollar|US$]]500 million. In some cases, [[fictitious]] merchants advertise goods for very low prices and never deliver. However, that type of fraud is minuscule compared to [[Crime|criminal]]s using stolen [[credit card]] information to buy goods and services.
| |
| − | | |
| − | The Internet serves as an excellent tool for investors, allowing them to easily and inexpensively research investment opportunities. But the Internet is also an excellent tool for fraudsters.
| |
| − | | |
| − | ===Geographic origin===
| |
| − | In some cases Internet Fraud schemes originate in the US and European countries, but a significant proportion seems to come from Africa, particularly [[Nigeria]], and sometimes from [[Ghana]] and [[Egypt]]. Some originate in [[Eastern Europe]], [[Southwest Asia]] and [[China]]. For some reason, many fraudulent orders seem to originate from [[Belgium]], from [[Amsterdam]] in the [[Netherlands]], from [[Norway]], and from [[Malmö]] in [[Sweden]].
| |
| − | | |
| − | === Geographic targets ===
| |
| − | Europe and the US are the leading targets of this type of fraud.
| |
| − | | |
| − | ===Popular products===
| |
| − | [[theft|Fraudsters]] seem to prefer small and valuable products, such as: [[watches]], [[jewelry]], [[laptop]]s, [[digital camera]]s, and [[camcorders]]. These items are usually commodities that are easily sellable and have a broad range of appeal. However, fraud in hosted marketplaces such as Ebay covers a broad range of products from cellular phones to desktop computers. The craft has continually evolved in sophistication. In some instances, a picture of the product is sent in place of the actual product. Other times, products are outright never sent after the bill is charged to credit card accounts. Victims are left to deal with credit card companies for chargebacks.
| |
| − | | |
| − | ===Identity theft schemes===
| |
| − | ====Stolen credit cards====
| |
| − | Most Internet fraud is done through the use of stolen credit card information which is obtained in many ways, the simplest being copying information from retailers, either [[online]] or [[offline]]. There have been many cases of [[hackers]] obtaining huge quantities of credit card information from companies' [[databases]]. There have been cases of [[employees]] of companies that deal with millions of customers in which they were selling the credit card information to criminals.
| |
| − | | |
| − | Despite the claims of the credit card industry and various merchants, using credit cards for online purchases can be insecure and carry a certain risk. Even so called "secure transactions" are not fully secure, since the information needs to be decrypted to plain text in order to process it. This is one of the points where credit card information is typically stolen.
| |
| − | | |
| − | ===Get wire transfer info===
| |
| − | Some fraudsters approach merchants asking them for large quotes. After they quickly accept the merchant's quote, they ask for wire transfer information to send payment. Immediately, they use online check issuing systems as [[Qchex]] that require nothing but a working email, to produce checks that they use to pay other merchants or simply send associates to cash them.
| |
| − | | |
| − | ===Purchase scams===
| |
| − | ====Direct solicitations====
| |
| − | The most straightforward type of purchase scam is a buyer in another country approaching many merchants through spamming them and directly asking them if they can ship to them using credit cards to pay.
| |
| − | | |
| − | An example of such email is as follows:
| |
| − | | |
| − | ''From: XXXXXX XXXXXX [XXXXXXX@hotmail.com] Sent: Saturday, October 01, 2005 11:35 AM Subject: International order enquiry''
| |
| − | | |
| − | ''Goodday Sales,''
| |
| − | ''This is XXXXXX XXXXXXX and I will like to place an order for some products in your store, But before I proceed with listing my requirements, I will like to know if you accept credit card and can ship internationally to Lagos, Nigeria. Could you get back to me with your website so as to forward you the list of my requirements as soon as possible.''
| |
| − | ''Regards, XXXXXX XXXXXX, XXXXXXXX Inc. 9999 XXXXX street, Mushin, Lagos 23401, Nigeria Telephone: 234-1-99999999, Fax: 234-1-9999999, Email: XXXXXXXXX@hotmail.com''
| |
| − | | |
| − | Most likely, a few weeks or months after the merchant ships and charges the Nigerian credit card, he/she will be hit with a chargeback from the credit card processor and lose all the money.
| |
| − | | |
| − | ====Counterfeit Postal Money Orders====
| |
| − | According to the FBI and postal inspectors, there has been a significant surge in the use of Counterfeit Postal Money Orders since October 2004. More than 3,700 counterfeit postal money orders (CPMOs) were intercepted by authorities from October to December of 2004, and according to the USPS, the "quality" of the counterfeits is so good that ordinary consumers can easily be fooled.
| |
| − | | |
| − | On March 9, 2005, the FDIC issued an alert <ref name="frd-int"> [http://www.fdic.gov/news/news/SpecialAlert/2005/sa2305.html Counterfeit U.S. Postal Money Orders] Counterfeit postal money orders are reportedly in circulation (FDIC) March 9, 2005</ref> stating that it had learned that counterfeit U.S. Postal Money Orders had been presented for payment at financial institutions.
| |
| − | | |
| − | On April 26, 2005, [[Tom Zeller Jr.]] wrote an article in ''[[The New York Times]]''<ref name="frd-time"> [http://www.usps.com/postalinspectors/mofeatur.htm A Common Currency for Online Fraud] Forgers of U.S. Postal Money Orders Grow by Tom Zeller Jr (NYT) April 26, 2005</ref> regarding a surge in the quantity and quality of the forging of U.S. Postal Money Orders, and its use to commit online fraud. The article shows a picture of a man that had been corresponding with a woman in Nigeria through a dating site, and received several fake postal money orders after the woman asked him to buy a computer and mail it to her.
| |
| − | | |
| − | Who has received Counterfeit Postal Money Orders (CPMOs):
| |
| − | *Small Internet retailers.
| |
| − | *Classified advertisers.
| |
| − | *Individuals that have been contacted through email or chat rooms by fraudsters posing as prospective social interests or business partners, and convinced to help the fraudsters unknowingly.
| |
| − | | |
| − | Geographical origin:
| |
| − | *Mostly from Nigeria
| |
| − | *Ghana
| |
| − | *Eastern Europe
| |
| − | | |
| − | The penalty for making or using counterfeit postal money orders is up to ten years in jail and a US$25,000 fine.
| |
| − | | |
| − | ====Online automotive fraud====
| |
| − | There are two basic schemes in online automotive fraud:
| |
| − | #A fraudster posts a vehicle for sale on an online site, generally for luxury or sports cars advertised for thousands less than market value. The details of the vehicle, including photos and description, are typically lifted from sites such as eBay Motors and re-posted elsewhere. An interested buyer, hopeful for a bargain, emails the seller, who responds saying the car is still available but is located overseas. He then instructs the buyer to send a deposit via wire transfer to initiate the "shipping" process. The unwitting buyer wires the funds, and doesn't discover until days or weeks later that they were scammed.
| |
| − | # A fraudster feigns interest in an actual vehicle for sale on the Internet. The "buyer" explains that a client of his is interested in the car, but due to an earlier sale that fell through has a certified check for thousands more than the asking price and requests the seller to send the balance via wire transfer. If the seller agrees to the transaction, the buyer sends the certified check via express courier (typically from [[Nigeria]]). The seller takes the check to their bank, which makes the funds available immediately. Thinking the bank has cleared the check, the seller follows through on the transaction by wiring the balance to the buyer. Days later, the check bounces and the seller realizes they have been scammed. But the money has long since been picked up and is not recoverable.
| |
| − | | |
| − | In another type of fraud, a fraudster contacts the seller of an automobile, asking for the [[vehicle identification number]], putatively to check the accident record of the vehicle. However, the supposed buyer actually uses the VIN to make fake papers for a stolen car that is then sold.
| |
| − | | |
| − | ====Cash the check system====
| |
| − | In some cases, fraudsters approach [[merchant]]s and ask for large orders: $50,000 to $200,000, and agree to pay via [[wire transfer]] in advance. After brief [[negotiation]], the buyers gives an excuse about the impossibility of sending a [[bank]] wire transfer. The buyer then offers to send a check, stating that the merchant can wait for the check to clear before shipping any goods. The check received, however, is a [[counterfeit]] of a check from a medium to large U.S. company. If asked, the buyer will claim that the check is money owed from the large company. The merchant deposits the check and it clears, so the goods are sent. Only later, when the larger company notices the check, will the merchant's account be debited.
| |
| − | | |
| − | In some cases, the fraudsters agree to the wire but ask the merchant for their bank's address. The fraudsters send the counterfeited check directly to the merchant's bank with a note asking to deposit it to the merchant's account. Unsuspecting bank officers deposit the check, and then the fraudster contacts the merchant stating that they made a [[direct deposit]] into the merchant's account.
| |
| − | | |
| − | ====Re-shippers====
| |
| − | Re-shipping scams trick individuals or small businesses into shipping goods to countries with weak legal systems. The goods are generally paid for with stolen or fake credit cards.
| |
| − | | |
| − | ====Nigerian version====
| |
| − | In the [[Nigerian]] version, the fraudsters have armies of people actively recruiting single women from western countries through chat & [[matchmaking]] sites. At some point, the criminal promises to marry the lady and come to their home country in the near future. Using some excuse the criminal asks permission of his "future wife" to ship some goods he is going to buy before he comes. As soon as the woman accepts the fraudster uses several credit cards to buy at different Internet sites simultaneously. In many cases the correct [[billing]] address of the cardholder is used, but the shipping address is the home of the unsuspecting "future wife." Around the time when the packages arrive, the criminal invents an excuse for not coming and tells his "bride" that he urgently needs to pick up most or all the packages. Since the woman has not spent any money, she sees nothing wrong and agrees. Soon after, she receives a [[package delivery]] company package with pre-printed labels that she has agreed to apply to the boxes that she already has at home. The next day, all boxes are picked up by the package delivery company and shipped to the criminal's real address (in Nigeria or elsewhere). After that day the unsuspecting victim stops receiving communications from the "future husband" because her usefulness is over. To make matters worse, in most cases the criminals were able to create accounts with the package deliverer, based on the woman's name and address. So, a week or two later, the woman receives a huge freight bill from the shipping company which she is supposed to pay because the goods were shipped from her home. Unwittingly, the woman became the criminal re-shipper and helped him with his criminal actions.
| |
| − | | |
| − | ====East European version====
| |
| − | This is a variant of the Nigerian Version, in which criminals recruit people through [[classified advertising]]. The criminals present themselves as a growing European company trying to establish a presence in the U.S. and agree to pay whatever the job applicant is looking to make, and more. The fraudsters explain to the unsuspecting victim that they will buy certain goods in the U.S. which need to be re-shipped to a final destination in [[Europe]]. When everything is agreed they start shipping goods to the re-shipper's house. The rest is similar to the Nigerian Version. Sometimes, when the criminals send the labels to be applied to the boxes, they also include a fake cheque, as payment for the re-shipper's services. By the time the cheque bounces unpaid, the boxes have been picked up already and all communication between fraudster and re-shipper has stopped.
| |
| − | | |
| − | ====Chinese version====
| |
| − | This is a variant of the East European Version, in which criminals recruit people through [[e-mail spam|spam]]. The criminals present themselves as a growing Chinese company trying to establish a presence in the U.S. or Europe and agree to pay an agent whatever the unsuspecting victim is looking to make, and more. Here is an example of a recruiting email:
| |
| − | | |
| − | :''Dear Sir/Madam, I am Mr. XXX XXX, managining XXXXXXXXXXX Corp. We are a company who deal on mechanical equipment, hardware and minerals, electrical products, Medical & Chemicals, light industrial products and office equipment, and export into the Canada/America and Europe. We are searching for representatives who can help us establish a medium of getting to our costumers in the Canada/America and Europe as well as making payments through you to us. Please if you are interested in transacting business with us we will be glad. Please contact us for more information. Subject to your satisfaction you will be given the opportunity to negotiate your mode of which we will pay for your services as our representative in Canada/America and Europe. Please if you are interested forward to us your phone number/fax and your full contact addresses. Thanks in advance. Mr. XXX XXX. Managing Director"''
| |
| − | | |
| − | ====Call tag scam====
| |
| − | The [[Merchant Risk Council]] reported that the "[[call tag]]" scam re-emerged over the 2005 holidays and several large merchants suffered losses. Under the scheme, criminals use stolen credit card information to purchase goods online for shipment to the legitimate cardholder. When the item is shipped and the criminal receives tracking information via email, he/she calls the cardholder and falsely identifies himself as the merchant that shipped the goods, saying that the product was mistakenly shipped and asking permission to pick it up upon receipt. The criminal then arranges the pickup issuing a "call tag" with a shipping company different that the one the original merchant used. The cardholder normally doesn't notice that there is a second shipping company picking up the product, which in turn has no knowledge it is participating in a fraud scheme. The cardholder then notices a charge in his card and generates a chargeback to the unsuspecting merchant.
| |
| − | | |
| − | ====Business opportunity/"Work-at-Home" schemes====
| |
| − | Fraudulent schemes often use the Internet to advertise purported business opportunities that will allow individuals to earn thousands of dollars a month in "work-at-home" ventures. These schemes typically require the individuals to pay anywhere from $35 to several hundred dollars or more, but fail to deliver the materials or information that would be needed to make the work-at-home opportunity a potentially viable business.
| |
| − | | |
| − | Often, after paying a registration fee, the applicant will be sent advice on how to place ads similar to the one that recruited him in order to recruit others, which is effectively a pyramid scheme.
| |
| − | | |
| − | Other types of work at home scams include [[home assembly kits]]. The applicant pays a fee for the kit, but after assembling and returning the item, it’s rejected as [[sub-standard]], meaning the applicant is out of pocket for the materials. Similar scams include home-working [[directories]], [[medical billing]], [[data entry]] at home or reading books for money.
| |
| − | | |
| − | ===Website scams===
| |
| − | ====Click fraud====
| |
| − | The latest scam to hit the headlines is the multi-million dollar [[Clickfraud]] which occurs when advertising network affiliates force paid views or clicks to ads on their own websites via [[Spyware]], the affiliate is then paid a commission on the [[cost-per-click]] that was artificially generated. Affiliate programs such as Google's [[Adsense]] capability pay high commissions that drive the generation of bogus clicks. With paid clicks costing as much as $100{{verify source}} and an online advertising industry worth more than $10 Billion, this form of Internet fraud is on the increase.
| |
| − | | |
| − | ====International modem dialing====
| |
| − | Many consumers connect to the Internet using a modem calling a local telephone number. Some web sites, normally containing adult content, use international dialing to trick consumers into paying to view content on their web site. Often these sites purport to be free and advertise that no credit card is needed. They then prompt the user to download a "viewer" or "dialer" to allow them to view the content. Once the program is downloaded it disconnects the computer from the Internet and proceeds to dial an international long distance or premium rate number, charging anything up to [[US$]]7-8 per minute. An international block is recommended to prevent this, but in the U.S. and Canada, calls to the Caribbean (except Haiti) can be dialed with a "1" and a three-digit area code, so such numbers, as well as "10-10 dial-round" phone company prefixes, can circumvent an international block.
| |
| − | | |
| − | ====Another type of Click Fraud====
| |
| − | This type of fraud involves a supposed internet marketing specialist presenting a prospective client with detailed graphs and charts that indicate that his web site receives (x) thousands of hits per month, emphasizing that if you pay for his services you will succeed in getting a number clicks converted to customers or clients.
| |
| − | | |
| − | When you receive no request for more information and no clients, the frauster responds that it must be something you web site is not doing right.
| |
| − | | |
| − | One recent experience resulted in the discovery that this fraudster's website had 176,000 pages, all with the same or very similar pages, they keywords included the days of the week and the months of the year, but nothing to do with any business except the fraudsters details. The experience resulted in the loss of £950 english pounds equivalent to US$1860.{{Fact|date=February 2007}}
| |
| − | | |
| − | ===Phishing===
| |
| − | | |
| − | | |
| − | "Phishing" is the act of attempting to fraudulently acquire sensitive information, such as passwords and credit card details, by masquerading as a trustworthy person or business with a real need for such information in a seemingly official electronic notification or message (most often an email, or an instant message). It is a form of [[social engineering]] attack.
| |
| − | | |
| − | The term was coined in the mid 1990s by crackers attempting to steal [[AOL]] accounts. An attacker would pose as an AOL staff member and send an instant message to a potential victim. The message would ask the victim to reveal his or her password, for instance to "verify your account" or to "confirm billing information." Once the victim gave over the password, the attacker could access the victim's account and use it for criminal purposes, such as spamming.
| |
| − | | |
| − | Phishing has been widely used by fraudsters using spam messages masquerading as large banks ([[Citibank]], [[Bank of America]]) or [[PayPal]]. These fraudsters can copy the code and graphics from legitimate websites and use them on their own sites to create a legitimate-looking scam web pages. They can also link to the graphics on the legitimate sites to use on their own scam site. These pages are so well done that most people cannot tell that they have navigated to a scam site. Fraudsters will also put the text of a link to a legitimate site in an e-mail but use the source code to links to own fake site. This can be revealed by using the "view source" feature in the e-mail application to look at the destination of the link or putting the cursor over the link and looking at the code in the status bar of the browser.
| |
| − | Although many people don't fall for it, the small percentage of people that do fall for it, multiplied by the sheer numbers of spam messages sent, presents the fraudster with a substantial incentive to keep doing it.
| |
| − | | |
| − | [[Anti-phishing]] technologies are now available.
| |
| − | | |
| − | ===Pharming===
| |
| − | | |
| − | | |
| − | '''Pharming''' is the [[Exploit (computer security)|exploitation]] of a [[vulnerability]] in the [[Domain name system|DNS server]] [[software]] that allows a [[hacker]] to acquire the [[domain name]] for a [[website|site]], and to redirect that website's traffic to another web site. DNS servers are the [[computer|machines]] responsible for resolving internet names into their real [[IP address|addresses]] - the "signposts" of the [[internet]].
| |
| − | | |
| − | If the web site receiving the traffic is a fake web site, such as a copy of a [[bank]]'s website, it can be used to "[[phishing|phish]]" or steal a computer user's [[password]]s, [[Personal identification number|PIN]] or [[Bank account|account]] number. Note that this is only possible when the original site was not [[Secure Sockets Layer|SSL]] protected, or when the user is ignoring warnings about invalid [[Server (computing)|server]] [[Public key certificate|certificates]].
| |
| − | | |
| − | For example, in January 2005, the domain name for a large New York [[Internet service provider|ISP]], [[Panix]], was [[Domain hijacking|hijacked]] to a site in [[Australia]]. In 2004 a [[Germany|German]] [[teenager]] hijacked the [[eBay]][[.de]] domain name.
| |
| − | | |
| − | [[Communications security|Secure]] [[e-mail]] provider [[Hushmail]] was also caught by this attack on 24th of April 2005 when the attacker rang up the domain registrar and gained enough information to redirect users to a [[defacement (vandalism)|defaced]] webpage.
| |
| − | | |
| − | [[Anti-pharming]] technologies are now available.
| |
| − | | |
| − | ===Auction and retail schemes online===
| |
| − | Fraudsters launch auctions on eBay or TradeMe with very low prices and no reservations especially for high priced items like watches, computers or high value collectibles. They received payment but never delivers, or delivers an item that is less valuable than the one offered, such as counterfeit, refurbished or used. Some fraudsters also create complete webstores that appear to be legitimate, but they never deliver the goods. In some cases, some stores or auctioneers are legitimate but eventually they stopped shipping after cashing the customers' payments.
| |
| − | | |
| − | Sometimes fraudsters will combine phishing to hijacking legitimate member accounts on eBay, typically with very high numbers of positive feedback, and then set up a phony online store. They received payment usually via check, money-order, cash or wire transfer but never deliver the goods; then they leave the poor, unknowing eBay member to sort out the mess. In this case the fraudster collects the money while ruining the reputation of the conned eBay member and leaving a large number of people without the goods they thought they purchased.
| |
| − | | |
| − | ===Stock market manipulation schemes===
| |
| − | These are also called investment schemes online. Criminals use these to try to manipulate securities prices on the market, for their personal profit. According to enforcement officials of the Securities and Exchange Commission, the 2 main methods used by these criminals are:
| |
| − | ====Pump-and-dump schemes====
| |
| − | False and/or fraudulent information is disseminated in chat rooms, forums, internet boards and via email (spamming), with the purpose of causing a dramatic price increase in thinly traded stocks or stocks of shell companies (the "pump"). As soon as the price reaches a certain level, criminals immediately sell off their holdings of those stocks (the "dump"), realizing substantial profits before the stock price falls back to its usual low level. Any buyers of the stock who are unaware of the fraud become victims once the price falls. When they realize the fraud, it is too late to sell. They lost a high percentage of their money. Even if the stock value does increase, the stocks may be hard to sell because of lack of interested buyers, leaving the shareholder with the shares for a far longer term than desired.
| |
| − | | |
| − | ====Short-selling or "scalping" schemes====
| |
| − | This scheme takes a similar approach to the "pump-and-dump" scheme, by disseminating false or fraudulent information through chat rooms, forums, internet boards and via email (spamming), but this time with the purpose of causing dramatic price decreases in a specific company's stock. Once the stock reaches a certain low level, criminals buy the stock or options on the stock, and then reverse the false information or just wait for it to wear off with time or to be disproved by the company or the media. Once the stock goes back to its normal level, the criminal sells the stock or option and reaps the huge gain.
| |
| − | | |
| − | ===Avoiding Internet investment scams===
| |
| − | The US Security Exchange Commission have enumerated guideline on how to avoid internet investment scams. The summary are as follows:
| |
| − | * The Internet allows individuals or companies to communicate with a large audience without spending a lot of time, effort, or money. Anyone can reach tens of thousands of people by building an Internet web site, posting a message on an online bulletin board, entering a discussion in a live "chat" room, or sending mass e-mails.
| |
| − | * If you want to invest wisely and steer clear of frauds, you must get the facts.
| |
| − | * The types of investment fraud seen online mirror the frauds perpetrated over the phone or through the mail. Consider all offers with skepticism.
| |
| − | | |
| − | ==File sharing and copyright issues==
| |
| − | | |
| − | '''File sharing''' is the practice of making [[computer file|file]]s available for other users to download over the [[Internet]] and smaller [[computer network|networks]]. Usually file sharing follows the [[peer-to-peer]] (P2P) model, where the files are stored on and served by personal computers of the users. Most people who engage in file sharing are also downloading files that other users share. Sometimes these two activities are linked together. P2P file sharing is distinct from file trading in that downloading files from a P2P network does not require uploading, although some networks either provide incentives for uploading such as credits or force the sharing of files being currently downloaded.
| |
| − | | |
| − | ===Copyright issues===
| |
| − | File sharing (such as with the Gnutella and Napster networks) grew in popularity with the proliferation of high speed Internet connections, relatively small file size and high-quality MP3 audio format. Although file sharing is a legal technology with legal uses, many users use it to download and upload copyrighted materials without permission, which can be [[copyright infringement]] if done without authorization for improper purposes. This has led to attacks against file sharing in general from many copyright owners.
| |
| − | | |
| − | There has been great discussion over perceived and actual legal issues surrounding file sharing. In circumstances where trading partners are in different countries with different legal codes, there are significant problems to contend with. What if a person in Canada wishes to share a piece of source code which, if compiled, has encryption capabilities? In some countries, a citizen may not request or receive such information without special permission.
| |
| − | | |
| − | Throughout the early 2000s, the entire file-sharing community has been in a state of flux. In the year 2000, there was speculation over how seriously record companies and the [[Recording Industry Association of America]] would strike the file-sharing community because of its limits compared to more traditional forms of media [http://web.archive.org/web/20031217191730/www.mp3newswire.net/stories/2000/buycd.html]. However, the communities suffered strain as record companies and the RIAA tried to shut down as much of it as possible. Even though they have forced Napster and Grokster into cooperating against copyright violations, they are fighting an uphill battle since the community has flourished and produced many different clients based on several different underlying protocols. The third generation of P2P protocols, such as [[Freenet]], are not as dependent as Napster is on a central server; and as they encrypt the shared data, it is much harder to shut down these systems through court actions. Another attempt (used by the maintainers of [[KaZaA]]) is to change the company's organization or country of origin so that it is impossible or useless to attack it legally. To date, [[file sharing in Canada]] is sometimes legal (unauthorized downloading of music is permitted, for example) , though not completely so[http://www.canadiancontent.net/commtr/article_633.html].
| |
| − | The uphill battle also extends to the legal actions taken by the RIAA and [[motion picture]] counterpart [[MPAA]] against individuals using file-sharing programs to distribute material protected by copyright. Ambiguity in the interpretation of copyright law has been a major factor contributing the lack of successful enforcement by the [[Intellectual Property]] owners. In [[Electra v. Perez]] for example, the Court ruled that the act of making such files available for distribution equated to infringement of the works involved. In the more recent [[UMG v. Lindor]], Judge David G. Trager ruled that the RIAA would be required to prove that actual distribution (sharing) occurred. Should this case go to trial in 2007, it will likely set a [[precedent]] for further RIAA and MPAA actions.
| |
| − | | |
| − | The [[Electronic Frontier Foundation]] (EFF) is a donor-supported group which seeks to protect and expand digital rights. Its activities include litigation, political lobbying, and public awareness campaigns. The EFF has vocally opposed the RIAA in its pursuit of lawsuits against users of file sharing applications and supported defendants in these cases. The foundation promotes the legalization of peer-to-peer sharing of copyrighted materials and alternative methods to provide compensation to copyright holders.<ref name="EFF">
| |
| − | {{cite web
| |
| − | | url = http://www.eff.org/share/?f=compensation.html
| |
| − | | title = Making P2P Pay Artists
| |
| − | | author = Electronic Frontier Foundation
| |
| − | | accessdate = April 25
| |
| − | | accessyear = 2006
| |
| − | }}</ref>
| |
| − | | |
| − | ===Legal controversy===
| |
| − | | |
| − | Under US law "the Betamax decision" ([[Sony Corp. of America v. Universal City Studios, Inc.]]), case holds that copying "technologies" are not ''inherently'' illegal, if substantial non-infringing use can be made of them. This decision, predating the widespread use of the [[Internet]] applies to most data networks, including peer-to-peer networks, since distribution of correctly licensed files can be performed. These non-infringing uses include sending open source software, public domain files and out of copyright works. Other jurisdictions tend to view the situation in somewhat similar ways.
| |
| − | | |
| − | In practice, many of the files shared on peer-to-peer networks are copies of copyrighted popular music and movies. Sharing of these copies among strangers is illegal in most jurisdictions. This has led many observers, including most media companies and some peer-to-peer critics, to conclude that the networks themselves pose grave threats to the established distribution model. The research that attempts to measure actual monetary loss has been somewhat equivocal. Whilst on paper the existence of these networks results in large losses, the actual income does not seem to have changed much since these networks started up. Whether the threat is real or not, both the [[Recording Industry Association of America|RIAA]] and the [[Motion Picture Association of America|MPAA]] now spend large amounts of money attempting to lobby lawmakers for the creation of new laws, and some copyright owners pay companies to help legally challenge users engaging in illegal sharing of their material.
| |
| − | | |
| − | In spite of the Betamax decision, peer-to-peer networks themselves have been targeted by the representatives of those artists and organizations who license their creative works, including industry trade organizations such as the RIAA and MPAA as a potential threat. The Napster service was shut down by an RIAA lawsuit.
| |
| − | | |
| − | In [[A & M Records, Inc. v. Napster, Inc.|''A&M Records v. Napster'']], 239 F.3d 1004 (9th Cir. 2001), the court found that Napster was both vicariously and contributorily liable for the copyright infringement its users were engaged in. Vicarious liability in these types of cases extends to a provider who financially benefits from the infringement committed by its users while having the ability to police that infringement but has failed to do so. The court found ample evidence that Napster’s future revenue is directly dependent upon “increases in userbase.” It also found that Napster could have done more than it claimed with regards to restricting users from sharing copyrighted material. Later on in the opinion, the famous peer-to-peer provider was also found contributorily liable. It knew of the infringing use that Napster could and did have, in a medium where the software provided essential access. The RIAA could have sued individual users at the time for violating federal law, but thought it more prudent to shut down the means by which those users shared music.
| |
| − |
| |
| − | Napster's use of a central server distinguishes it, on its facts, from the next generation peer-to-peer technology, in which the communication of files is truly "peer to peer." Therefore, additional litigation was needed to determine the legality of their uses.
| |
| − | | |
| − | In ''[[MGM Studios, Inc. v. Grokster, Ltd.|MGM v. Grokster]]'', the U.S. Supreme Court reversed a decision of the Ninth Circuit Court of Appeals which had granted a summary judgment of dismissal, and held that there were factual issues concerning whether the defendant p2p software providers had, or had not, encouraged their users to infringe copyrights. If they had done so, they could be held liable for secondary copyright infringement.
| |
| − | | |
| − | The main point of the Grokster holding was about "inducement." "The classic case of direct evidence of unlawful purpose occurs when one induces commission of infringement by another, or "entic[es] or persuad[es] another" to infringe, Black's Law Dictionary 790 (8th ed. 2004), as by advertising. Thus at common law a copyright or patent defendant who "not only expected but invoked [infringing use] by advertisement" was liable for infringement …"
| |
| − | The court noted that simply providing the material was not enough. While the decision did not find liability, it simply laid out the groundwork for how the law should be interpreted.
| |
| − | | |
| − | A little over a year later, the RIAA initiated the first major post-Grokster case, ''[http://info.riaalawsuits.us/documents.htm#Arista_v_LimeWire Arista v. Limewire]'', in Manhattan federal court. Lime Wire has counterclaimed in that suit, charging the major record companies with antitrust violations and other misconduct.[http://recordingindustryvspeople.blogspot.com/2006/09/lime-wire-sues-riaa-for-antitrust.html "Lime Wire Sues RIAA for Antitrust Violations"]
| |
| − | | |
| − | Shortly thereafter, the lower court judge in ''Grokster'' found one of the defendants, Streamcast, the maker of Morpheus, to be liable under the standards enunciated by the Supreme Court. [http://recordingindustryvspeople.blogspot.com/2006/09/streamcast-held-liable-for-copyright.html "Streamcast Held Liable for Copyright Infringement in MGM v. Grokster, Round 2" ("Recording Industry vs. The People")]
| |
| − | | |
| − | The foregoing cases dealt with 'secondary liability' under the Copyright Act, i.e. whether and when the p2p network software providers can be held liable for 'primary' infringement by their customers. Meanwhile, the underlying question of what uses those customers can make of p2p software without committing a primary infringement is a matter just beginning to be explored, most notably in litigations brought by the Motion Picture Association of America (MPAA) and the Recording Industry Association of America (RIAA) against p2p customers.
| |
| − | | |
| − | In ''Elektra v. Barker'',<ref>[http://recordingindustryvspeople.blogspot.com#Elektra_v_Barker Elektra v. Barker]</ref> an RIAA case against Tenise Barker, a Bronx nursing student, Ms. Barker moved to dismiss the complaint, contending, among other things, that the RIAA's allegation of "making available" did not state any known claim under the Copyright Act.<ref>[http://www.ilrweb.com/viewILRPDF.asp?filename=elektra_barker_memooflaw Elektra v. Barker, Memorandum of Law in Support of Motion to Dismiss Complaint]</ref><ref>[http://www.ilrweb.com/viewILRPDF.asp?filename=elektra_barker_replymemomotdis Reply Memorandum of Law in Support of Motion to Dismiss Complaint]</ref>. The RIAA countered with the argument that "making available" is a copyright infringement, even though the language does not appear in the Act.<ref>[http://www.ilrweb.com/viewILRPDF.asp?filename=elektra_barker_oppositiontomotion Elektra v. Barker, Plaintiffs' Memorandum of Law in Opposition to Dismissal Motion]</ref> Thereafter, several ''amicus curiae'' were permitted to file briefs in the case, including the MPAA, which agreed<ref>[http://www.ilrweb.com/viewILRPDF.asp?filename=elektra_barker_mpaabrief Amicus Curiae brief of MPAA]</ref> with the RIAA's argument, and the Electronic Frontier Foundation (EFF), the U.S. Internet Industry Association (USIIA), and the Computer & Communications Industry Association (CCIA), which agreed with Ms. Barker.<ref>[http://www.ilrweb.com/viewILRPDF.asp?filename=elektra_barker_effamicusbrief Amicus Curiae brief of EFF]</ref><ref>[http://www.ilrweb.com/viewILRPDF.asp?filename=elektra_barker_amicusbriefcomputercomm Amicus Curiae brief of USIIA and CCIA]</ref> The US Department of Justice submitted a brief refuting one of the arguments made by EFF,<ref>[http://www.ilrweb.com/viewILRPDF.asp?filename=elektra_barker_usstatement Statement of Interest of U.S. Department of Justice]</ref> but did not take any position on the RIAA's "making available" argument<ref>[http://www.ilrweb.com/viewILRPDF.asp?filename=elektra_barker_usstatement Statement of Interest, page 5, footnote 3]</ref>. The ''Elektra v. Barker'' case was argued before Judge Kenneth M. Karas in Manhattan federal court on January 26, 2007<ref>[http://recordingindustryvspeople.blogspot.com/2007/02/elektra-v-barker-making-available-oral.html "Elektra v. Barker "Making Available" Oral Argument Now Available Online"</ref>, and as of this writing is awaiting decision.
| |
| − | | |
| − | [[Anonymous P2P|Anonymous peer-to-peer]] networks allow for distribution of material — legal or not — with little or no legal accountability across a wide variety of jurisdictions. Many profess that this will lead to greater or easier trading of illegal material and even (as some suggest) facilitate [[terrorism]], and call for its regulation on those grounds.<ref>http://news.bbc.co.uk/2/hi/programmes/newsnight/4758636.stm</ref> Others counter that the presumption of innocence must apply, and that non peer-to-peer technologies like [[e-mail]] (for which there are also anonymizing services), have similar capabilities. Further, the potential for illegal uses should not prevent the technology from being used for legal purposes. The companies who create the [[software]] cover themselves by not allowing people to [[download]] it if they do not accept that it is illegal to do this.
| |
| − | | |
| − | In the [[European Union]] (EU), the 2001 [[EU Copyright directive]], which implemented the 1996 [[World Intellectual Property Organization Copyright Treaty|WIPO treaty]] ("World Intellectual Property Organization Copyright Treaty"), prohibits peer-to-peer, claiming it is a violation of the directive. However, not all European member states have implemented the directive in national legislation. Notably, on December 22, 2005, after discussing the EU directive, the French parliament passed two amendments legalizing the exchange of copies on the internet for private use. In a later proceeding, the French government withdrew the article in question and made illegal any p2p client obviously aimed at sharing copyrighted material. The term "obviously" was not defined. The project of law (called [[DADVSI]]) has still to be discussed by the French senate and, if the decision differs too much from the Parliament's, it will be debated on second lecture back at the Parliament ([[Assemblée Nationale]]).
| |
| − | | |
| − | Interestingly, Canada stands out by authorizing, at least until the projected copyright reform, downloads on peer-to-peer networks under the "private copying" exception.
| |
| − | | |
| − | ====Important Cases====
| |
| − | | |
| − | * US law
| |
| − | **[[Sony Corp. of America v. Universal City Studios, Inc.|Sony Corp. v. Universal City Studios]] (The Betamax decision)
| |
| − | ** [[MGM Studios, Inc. v. Grokster, Ltd.|MGM v. Grokster]]
| |
| − | | |
| − | ===Attacks on peer-to-peer networks===
| |
| − | Many peer-to-peer networks are under constant attack by people with a variety of motives.
| |
| − | | |
| − | Examples include:
| |
| − | * poisoning attacks (e.g. providing files whose contents are different from the description)
| |
| − | * polluting attacks (e.g. inserting "bad" chunks/packets into an otherwise valid file on the network)
| |
| − | * defection attacks (users or software that make use of the network without contributing resources to it)
| |
| − | * insertion of viruses to carried data (e.g. downloaded or carried files may be infected with viruses or other malware)
| |
| − | * [[malware]] in the peer-to-peer network software itself (e.g. distributed software may contain spyware)
| |
| − | * [[Denial-of-service attack|denial of service]] attacks (attacks that may make the network run very slowly or break completely)
| |
| − | * filtering (network operators may attempt to prevent peer-to-peer network data from being carried)
| |
| − | * identity attacks (e.g. tracking down the users of the network and harassing or legally attacking them)
| |
| − | * [[spamming]] (e.g. sending unsolicited information across the network- not necessarily as a denial of service attack)
| |
| − | | |
| − | ===Risks===
| |
| − | Some file sharing software comes bundled with [[malware]] such as [[spyware]] or [[adware]]. Sometimes this malware remains installed on the system even if the original file sharing software is removed, and can be very difficult to eliminate. In many cases such malware can interfere with the correct operation of [[web browser]]s, [[anti-virus software]], anti-spyware and [[Firewall (networking)|software firewalls]], and can cause degraded performance on affected systems. Such malware is typically bundled with [[proprietary software]], and not those in [[open source]]. In most cases it is possible to easily remove adware and spyware by running [[:Category:Spyware removal|spyware removal]] programs. Such programs can often remove malware without influencing the functionality of the file sharing software.
| |
| − | | |
| − | Some are also concerned about the use of file sharing systems to distribute [[child pornography]], inflammatory literature, and illegal or unpopular material. Novice users may find it difficult to obtain information on which networks are "safe" for them to use. However, experienced users know that there is only one way to get in contact with such material: You have to actively search for it.<ref name="Morris03">
| |
| − | {{cite web
| |
| − | | last = Morris
| |
| − | | first = Alan
| |
| − | | title = Testimony of Mr. Alan Morris about Pornography, Technology and Process: Problems and Solutions on Peer-to-Peer Networks
| |
| − | | publisher = United States Senate, Committee on the Judiciary, Washington, DC
| |
| − | |date= 2003-08-22
| |
| − | | url = http://judiciary.senate.gov/testimony.cfm?id=902&wit_id=2277
| |
| − | | accessdate = 2006-11-20 }}</ref>
| |
| − | Therefore they recommend not to search for illegal material.
| |
| − | | |
| − | ==Hacking==
| |
| − | | |
| − | | |
| − | '''Hacker''' is a term often applied to [[computer software]] or [[computer hardware]] [[programmer]]s, designers and administrators, especially those who are perceived as experts or highly accomplished in this field. A hacker is also a term used for someone who modifies electronics such as ham radio transceivers, printers or even home sprinkler systems for better functionality or performance. The term usually bears strong connotations that may be favorable or pejorative depending on cultural context (see the [[hacker definition controversy]]).
| |
| − | *In [[computer programming]], a hacker is a software designer and programmer who builds programs and systems that garner the respect of one's peers. A hacker may also be a programmer who reaches a goal by employing a series of modifications to [[exploit]] or extend existing [[source code|code]] or resources. For some, "hacker" has a negative connotation and refers to a person who gains illegal access to computers ([[Hack (technology slang)|hack]]s) or uses [[kludge]]s to accomplish programming tasks that are ugly, inelegant, and inefficient. This derogatory form of the noun "hack" is even used among users of the positive sense of "hacker" (some argue that it should not be, due to this negative meaning; others argue that some kludges can, for all their ugliness and imperfection, still have "hack value").
| |
| − | | |
| − | *In [[computer security]], a [[Hacker (computer security)|hacker]] is a person who specializes in work with the security mechanisms for computer and network systems. While including those who endeavor to strengthen such mechanisms, it is more often used by the [[mass media]] and popular culture to refer to those who seek access despite these security measures.
| |
| − | | |
| − | *In other technical fields, hacker is extended to mean a person who makes things work beyond perceived limits through their own technical skill, such as a [[hardware hacker]], or [[reality hacker]].
| |
| − | | |
| − | ===Recognized hackers===
| |
| − | These individuals listed could be included in more than one category. See also [[Hacker (computer security)]], which has a list of people in that category, including criminal or unethical hackers.
| |
| − | | |
| − | ====Skilled programmers====
| |
| − | | |
| − | | |
| − | Many programmers have been labeled "great hackers,"<ref>{{cite web | url=http://www.paulgraham.com/gh.html | title=Great Hackers | author=[[Paul Graham|Graham, Paul]] | year=2004}}</ref> but the specifics of who that label applies to is a matter of opinion. Certainly major contributors to [[computer science]] such as [[Edsger Dijkstra]] and [[Donald Knuth]], as well as the inventors of popular software such as [[Linus Torvalds]] ([[Linux]]), and [[Dennis Ritchie]] and [[Ken Thompson (computer programmer)|Ken Thompson]] (the [[C (programming language)|C programming language]]) are likely to be included in any such list.
| |
| − | | |
| − | ====Hacker media personalities====
| |
| − | Listed below are individuals who, while fitting in one or more of the above categories, are (especially among the general public) currently more widely famous for their media presence ("famous for being famous") than their technical accomplishments.
| |
| − | | |
| − | *[[Loyd Blankenship]] (also known as [[The Mentor]]) — Former [[Legion of Doom (hacking)|LOD]] member. Author of [[Hacker Manifesto|The Conscience of a Hacker (Hacker's Manifesto)]].
| |
| − | | |
| − | *[[Eric Gorden Corley|Eric Corley]] (also known as [[Emmanuel Goldstein]]) — Long standing publisher of [[2600 The Hacker Quarterly|2600: The Hacker Quarterly]] and founder of the [[H.O.P.E.]] conferences. He has been part of the hacker community since the late '70s.
| |
| − | | |
| − | *[[Cult of the Dead Cow|CULT OF THE DEAD COW]] — A high profile hacker group that has both made news and been consulted by the media on numerous occasions.
| |
| − | | |
| − | *[[Brian Dorsett]] — Reverse-engineered the [[NDS Group|NDS]] satellite access smartcard known as the [[DirecTV#Access card history|HU card]]. Currently imprisoned at [[Federal Detention Center, Miami|Miami FDC]]. Records a daily podcast from prison titled {{dlw-inline|http://bdorsett.mypodcast.com/|title=Prisoncast}}
| |
| − | | |
| − | *[[Dark Ligh+ning]] &madsh; The founder of St0rmCl0ud, a group the seeks to improve awarness about computer insecurities.
| |
| − | | |
| − | *[[Bill Gates|William Henry Gates III]] (Bill Gates) — is the co-founder and chairman of [[Microsoft]] Corporation. Although he personally demonstrated considerable personal coding skill early in his company's history <ref>Article from The Register [http://www.theregister.co.uk/2001/05/15/could_bill_gates_write_code/]</ref><ref>Archive.org cache of discussion of Altair Basic source code [http://web.archive.org/web/20020102173701/http://www.rjh.org.uk/altair/ian.htm]</ref>, he is most widely recognizable today as the world's richest individual. Formerly CEO, in June 2006 he also stepped down as chief software architect, with the intention of stepping down as chairman in July 2008.<ref>Microsoft Press release June 2006 [http://www.microsoft.com/presspass/press/2006/jun06/06-15CorpNewsPR.mspx]</ref>
| |
| − | | |
| − | * [[Patrick K. Kroupa]] (also known as [[Lord Digital]]) — Former [[Legion of Doom (hacking)|LOD]] member, co-founder of [[MindVox]], author of Phantom Access programs, and MindVox: The Overture. Appears in over 20 books and hundreds of media and press articles.
| |
| − | | |
| − | *[[Gary McKinnon]] — accused of hacking into 97 [[Military of the United States|United States military]] and [[NASA]] computers in 2001 and 2002 . [http://news.bbc.co.uk/1/hi/technology/4757375.stm]
| |
| − | | |
| − | *[[Kevin Mitnick]] — A former computer criminal who now (since his release from prison in 2000) speaks, consults, and authors books about [[social engineering (security)|social engineering]] and network security.
| |
| − | | |
| − | *Neal Patrick and [[The 414s]] — teenage hackers who gained brief but widespread media coverage in 1983.
| |
| − | | |
| − | *[[Ahmed Ragab]] — Also one of the founders of the [[Open Source Initiative]]. He was the former [[Debian GNU/Linux]] Project Leader, and is the primary author of the [[Open Source Definition]].
| |
| − | | |
| − | *[[Richard Stallman]] — founder of the free software movement and the [[GNU project]], and president of the [[Free Software Foundation]]. Author of the famous [[Emacs]] text editor and the [[GNU Compiler Collection|GNU Compiler Collection (GCC)]]. [http://en.wikipedia.org/wiki/Richard_Stallman]
| |
| − | | |
| − | *[[Eric S. Raymond]] — One of the founders of the [[Open Source Initiative]]. He wrote the famous text [[The Cathedral and the Bazaar]] and many other essays. He also maintains the [[Jargon File]] for the [[Hacker culture]], which was previously maintained by [[Guy L. Steele, Jr.]].
| |
| − | | |
| − | *[[Steve Wozniak]] — Computer engineer who created the [[Apple I]] and [[Apple II series]] computers and, with [[Steve Jobs]], founded Apple Computer (now [[Apple Inc.]]). He is known in the hacker community as "Woz" or "The other Steve." Woz came up with some ingenious hardware hacks to bring those machines to completion. Tales of his "[[blue box]]" phone calls are legendary.
| |
| − | | |
| − | ==Computer Viruses and other Malware==
| |
| − | | |
| − | '''Malware''' is software designed to infiltrate or damage a computer system without the owner's [[informed consent]]. It is a [[portmanteau]] of the words "[[Malice (legal term)|malicious]]" and "[[Computer software|software]]." The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code.
| |
| − | | |
| − | Many normal computer users are however still unfamiliar with the term, and most never use it. Instead, "(computer) [[computer virus|virus]]" is used in common parlance and often in the general media to describe all kinds of malware. Another term that has been recently coined for malware is '''badware''', perhaps due to the anti-malware initiative [[Stopbadware]] or corruption of the term "malware."
| |
| − | | |
| − | Software is considered malware based on the perceived intent of the creator rather than any particular features. It includes computer viruses, [[Computer worm|worms]], [[Trojan horse (computing)|trojan horse]]s, [[spyware]], dishonest [[adware]], and other malicious and unwanted software. In [[law]], malware is sometimes known as a '''computer contaminant''', for instance in the legal codes of [[California]], [[West Virginia]], and several other [[United States|U.S.]] states.<ref>[http://www.ncsl.org/programs/lis/cip/viruslaws.htm]</ref>
| |
| − | | |
| − | Malware should not be confused with defective software, that is, software which has a legitimate purpose but contains harmful [[Software bug|bugs]].
| |
| − | | |
| − | ===Purposes===
| |
| − | Many early infectious programs, including the [[Internet Worm]] and a number of [[MS-DOS]] viruses, were written as experiments or pranks generally intended to be harmless or merely annoying rather than to cause serious damage. Young [[programmer]]s learning about viruses and the techniques used to write them might write one to prove that they can do it, or to see how far it could spread. As late as 1999, widespread viruses such as the [[Melissa virus]] appear to have been written chiefly as pranks.
| |
| − | | |
| − | A slightly more hostile intent can be found in programs designed to vandalize or cause data loss. Many DOS viruses, and the [[Microsoft Windows|Windows]] [[ExploreZip]] worm, were designed to destroy files on a [[hard disk]], or to corrupt the filesystem by writing junk data. Network-borne worms such as the 2001 [[Code Red worm]] or the Ramen worm fall into the same category. Designed to vandalize web pages, these worms may seem like the online equivalent to graffiti [[tagging]], with the author's alias or affinity group appearing everywhere the worm goes.
| |
| − | | |
| − | However, since the rise of widespread [[broadband]] [[Internet]] access, more malicious software has been designed for a profit motive. For instance, since 2003, the majority of widespread viruses and worms have been designed to take control of users' computers for black-market exploitation. {{Fact|date=February 2007}} Infected "[[zombie computer]]s" are used to send [[email spam]], to host contraband data such as [[child pornography]][http://www.pcworld.com/article/id,116841-page,1/article.html], or to engage in [[distributed denial-of-service]] attacks as a form of [[extortion]].
| |
| − | | |
| − | Another strictly for-profit category of malware has emerged in [[spyware]] — programs designed to monitor users' web browsing, display unsolicited advertisements, or redirect [[affiliate marketing]] revenues to the spyware creator. Spyware programs do not spread like viruses; they are generally installed by exploiting security holes or are packaged with user-installed software.
| |
| − | | |
| − | ===Infectious malware: viruses and worms===
| |
| − | The best-known types of malware, ''viruses'' and ''worms'', are known for the manner in which they spread, rather than any other particular behavior. Originally, the term ''[[computer virus]]'' was used for a program which infected other executable software, while a ''[[computer worm|worm]]'' transmitted itself over a network to infect other computers. More recently, the words are often used interchangeably.
| |
| − | | |
| − | Today, some draw the distinction between viruses and worms by saying that a virus requires user intervention to spread, whereas a worm spreads automatically.{{Fact|date=February 2007}} Using this distinction, infections transmitted by [[email]] or [[Microsoft Word]] documents, which rely on the recipient opening a file to infect the system, would be classified as viruses, not worms.
| |
| − | | |
| − | ===Capsule history of viruses and worms===
| |
| − | | |
| − | | |
| − | Before [[Internet]] access became widespread, viruses spread on personal computers by infecting programs or the executable [[boot sector]]s of floppy disks. By inserting a copy of itself into the [[machine code]] instructions in these executables, a virus causes itself to be run whenever the program is run or the disk is booted. Early computer viruses were written for the [[Apple II]] and [[Apple Macintosh|Macintosh]], but they became more widespread with the dominance of the [[IBM PC]] and [[MS-DOS]] system. Executable-infecting viruses are dependent on users exchanging software or boot floppies, so they spread heavily in computer hobbyist circles.
| |
| − | | |
| − | The first worms, network-borne infectious programs, originated not on personal computers, but on multitasking [[Unix]] systems. The first well-known worm was the [[Internet Worm]] of 1988, which infected [[SunOS]] and [[VAX]] [[BSD]] systems. Unlike a virus, this worm did not insert itself into other programs. Instead, it exploited security holes in network server programs and started itself running as a separate process. This same behavior is used by today's worms as well.
| |
| − | | |
| − | With the rise of the [[Microsoft Windows]] platform in the 1990s, and the flexible [[macro]] systems of its applications, it became possible to write infectious code in the macro language of [[Microsoft Office Word|Microsoft Word]] and similar programs. These ''[[macro virus (computing)|macro virus]]es'' infect documents and templates rather than applications, but rely on the fact that macros in a Word document are a form of executable code.
| |
| − | | |
| − | Today, worms are most commonly written for the Windows OS, although a small number are also written for [[Linux]] and [[Unix]] systems. Worms today work in the same basic way as 1988's Internet Worm: they scan the network for computers with vulnerable network services, break in to those computers, and copy themselves over. Worm outbreaks have become a cyclical plague for both home users and businesses, eclipsed recently in terms of damage by [[spyware]].{{Fact|date=February 2007}}
| |
| − | | |
| − | ===Concealment: Trojan horses, rootkits, and backdoors===
| |
| − | For a malicious program to accomplish its goals, it must be able to do so without being shut down, or deleted by the user or administrator of the computer it's running on. Concealment can also help get the malware installed in the first place. By disguising a malicious program as something innocuous or desirable, users may be tempted to install it without knowing what it does. This is the technique of the ''[[Trojan horse (computing)|Trojan horse]]'' or ''trojan''.
| |
| − | | |
| − | Often attempting to delete malicious software on a computer may activate the software, causing damage and the infection of other files in the computer. Some anti virus programs that fail to stop Malware and Trojans on the computer have a virus chest file. This is an isolated folder where infected files can be stored and protected from usage until they are removed.
| |
| − | | |
| − | Broadly speaking, a Trojan horse is any program that invites the user to run it, but conceals a harmful or malicious payload. The payload may take effect immediately and can lead to many undesirable effects, such as deleting all the user's files, or more commonly it may install further harmful software into the user's system to serve the creator's longer-term goals. Trojan horses known as [[dropper]]s are used to start off a worm outbreak, by injecting the worm into users' local networks.
| |
| − | | |
| − | One of the most common ways that spyware is distributed is as a Trojan horse, bundled with a piece of desirable software that the user downloads off the Web or a peer-to-peer file-trading network. When the user installs the software, the spyware is installed alongside. Spyware authors who attempt to act legally may include an [[end-user license agreement]] which states the behavior of the spyware in loose terms, but with the knowledge that users are unlikely to read or understand it.
| |
| − | | |
| − | Once a malicious program is installed on a system, it is often useful to the creator if it ''stays'' concealed. The same is true when a human attacker breaks into a computer directly. Techniques known as ''[[rootkit]]s'' allow this concealment, by modifying the host operating system so that the malware is hidden from the user. Rootkits can prevent a malicious [[process (computing)|process]] from being visible in the system's list of processes, or keep its files from being read. Originally, a rootkit was a set of tools installed by a human attacker on a Unix system where the attacker had gained administrator (root) access. Today, the term is used more generally for concealment routines in a malicious program.
| |
| − | | |
| − | A [[backdoor]] is a method of bypassing normal [[authentication]] procedures. Once a system has been compromised (by one of the above methods, or in some other way), one or more backdoors may be installed, in order to allow the attacker access in the future. The idea has often been floated that many computer manufacturers preinstall backdoors on their systems to provide technical support for customers, but this has never been reliably verified. [[Cracker (computing)|Crackers]] typically use backdoors to secure remote access to a computer, while attempting to remain hidden from casual inspection. To install backdoors crackers may use [[Trojan Horse (Computing)|Trojan horses]], [[Computer worm|worms]], or other methods.
| |
| − | | |
| − | ===Malware for profit: spyware, botnets, loggers, and dialers===
| |
| − | During the 1980s and 1990s, it was usually taken for granted that malicious programs were created as a form of [[vandalism]] or [[prank]]. More recently, the greater share of malware programs have been written with a financial or profit motive in mind. This can be taken as the malware authors' choice to monetize their control over infected systems: to turn that control into a source of revenue.
| |
| − | | |
| − | Since 2003 or so, the most costly form of malware in terms of time and money spent in recovery has been the broad category known as ''[[spyware]]''. {{Fact|date=February 2007}} Spyware programs are commercially produced for the purpose of gathering information about computer users, showing them [[pop-up ad]]s, or altering web-browser behavior for the financial benefit of the spyware creator. For instance, some spyware programs redirect [[search engine]] results to paid advertisements. Others often called "[[stealware]]" by the media overwrite [[affiliate marketing]] codes so that revenue goes to the spyware creator rather than the intended recipient.
| |
| − | | |
| − | Spyware programs are sometimes installed as Trojan horses of one sort or another. They differ in that their creators present themselves openly as businesses, for instance by selling advertising space on the pop-ups created by the malware. Most such programs present the user with an [[end-user license agreement]] which purportedly protects the creator from prosecution under computer contaminant laws. However, spyware EULAs have not yet been upheld in court.
| |
| − | | |
| − | Another way that financially-motivated malware creator can monetize their infections is to directly use the infected computers to do work for the creator. ''Spammer viruses'', such as the [[Sobig]] and [[Mydoom]] virus families, are commissioned by [[e-mail spam]] gangs. The infected computers are used as [[open proxy|proxies]] to send out spam messages. The advantage to spammers of using infected computers is that they are available in large supply (thanks to the virus) and they provide anonymity, protecting the spammer from prosecution. Spammers have also used infected PCs to target anti-spam organizations with [[distributed denial-of-service attack]]s.
| |
| − | | |
| − | In order to coordinate the activity of many infected computers, attackers have used coordinating systems known as ''[[botnet]]s''. In a botnet, the malware or [[malbot]] logs in to an [[Internet Relay Chat]] channel or other chat system. The attacker can then give instructions to all the infected systems simultaneously. Botnets can also be used to push upgraded malware to the infected systems, keeping them resistant to anti-virus software or other security measures.
| |
| − | | |
| − | Lastly, it is possible for a malware creator to profit by simply stealing from the person whose computer is infected. Some malware programs install a ''[[Keystroke logging|key logger]]'', which copies down the user's keystrokes when entering a password, credit card number, or other information that may be useful to the creator. This is then transmitted to the malware creator automatically, enabling [[credit card fraud]] and other theft. Similarly, malware may copy the [[CD key]] or password for online games, allowing the creator to steal accounts or virtual items.
| |
| − | | |
| − | Another way of stealing money from the infected PC owner is to take control of the [[modem]] and dial an expensive toll call. ''[[Dialer]]'' (or ''porn dialer'') software dials up a [[premium-rate telephone number]] such as a U.S. "900 number" and leave the line open, charging the toll to the infected user.
| |
| − | | |
| − | ===Vulnerability to malware===
| |
| − | In this context, as throughout, it should be borne in mind that the “system” under attack may be of various types, e.g. a single computer and operating system, a network or an application.
| |
| − | | |
| − | Various factors make a system more vulnerable to malware:
| |
| − | *'''Homogeneity''' – e.g. when all computers in a network run the same OS, if you can break that OS, you can break into any computer running it.
| |
| − | *'''Defects''' – most systems containing errors which may be exploited by malware.
| |
| − | *'''Unconfirmed code''' – code from a floppy disk, CD or [[USB]] device may be executed without the user’s agreement.
| |
| − | *'''Over-privileged users''' – some systems allow all users to modify their internal structures.
| |
| − | *'''Over-privileged code''' – most popular systems allow code executed by a user all rights of that user.
| |
| − | | |
| − | An oft-cited cause of vulnerability of networks is '''homogeneity''' or software monoculture. In particular, Microsoft Windows has such a large share of the market that concentrating on it will enable a cracker to subvert a large number of systems. Introducing inhomogeneity purely for the sake of robustness would however bring high costs in terms of training and maintenance.
| |
| − | | |
| − | Most systems contain '''bugs''' which may be exploited by malware. Typical examples are [[buffer overrun]]s,
| |
| − | in which an interface designed to store data in a small area of memory allows the caller to supply too much,
| |
| − | and then overwrites its internal structures. This may used by malware to force the system to execute its code.
| |
| − | | |
| − | Originally, PCs had to be booted from floppy disks, and until recently it was common for this to be the default boot device. This meant that a corrupt floppy disk could subvert the computer during booting, and the same applies to CDs. Although that is now less common, it is still possible to forget that one has changed the default, and rare that a [[BIOS]] makes one '''confirm''' a boot from removable media.
| |
| − | | |
| − | In some systems, non-administrator '''users are over-privileged''' by design, in the sense that they are allowed to modify internal structures of the system. In some environments, users are over-privileged because they have been inappropriately granted administrator or equivalent status. This is a primarily a configuration decision, but on Microsoft Windows systems the default configuration is to over-privilege the user. This situation exists due to decisions made by Microsoft to prioritize compatibility with older systems above security configuration in newer systems{{Fact|date=February 2007}} and because typical applications were developed without the under-privileged users in mind. As privilege escalation exploits have increased this priority is shifting for the release of Microsoft Windows Vista. As a result, many existing applications that require excess privilege (over-privileged code) may have compatibility problems with Vista. However, Vista's User Account Control feature attempts to remedy applications not designed for under-privileged users through virtualization, acting as a crutch to resolve the privileged access problem inherent in legacy applications.
| |
| − | | |
| − | Malware, running as over-privileged code, can use this privilege to subvert the system. Almost all currently popular operating systems, and also many scripting applications allow '''code too many privileges''', usually in the sense that when a user executes code, the system allows that code all rights of that user. This makes users vulnerable to malware in the form of [[e-mail attachment]]s, which may or may not be disguised.
| |
| − | | |
| − | | |
| − | Given this state of affairs, users are warned only to open attachments they trust, and to be wary of code received from untrusted sources. It also common for operating systems to be designed so that [[device driver]]s need escalated privileges, while they are supplied by more and more hardware manufacturers, some of whom may be unreliable.
| |
| − | | |
| − | ====Eliminating over-privileged code====
| |
| − | Over-privileged code dates from the time when most programs were either delivered with a computer or written in-house, and repairing it would at a stroke render most anti-virus software almost redundant. It would, however, have appreciable consequences for the user interface and system management.
| |
| − | | |
| − | The system would have to maintain privilege profiles, and know which to apply for each user and program.
| |
| − | In the case of newly installed software, an administrator would need to set up default profiles for the new code.
| |
| | | | |
| − | Eliminating vulnerability to rogue [[device drivers]] is probably harder than for arbitrary rogue executables. Two techniques, used in [[OpenVMS|VMS]], that can help are memory mapping only the registers of the device in question and a system interface associating the driver with interrupts from the device.
| + | Another way to define cybercrime is simply as criminal activity involving the information technology infrastructure, including illegal access (unauthorized access), illegal interception (by technical means of non-public transmissions of computer data to, from or within a computer system), data interference (unauthorized damaging, deletion, deterioration, alteration, or suppression of computer data), systems interference (interfering with the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering, or suppressing computer data), misuse of devices, [[forgery]] (identity theft), and electronic fraud. |
| | | | |
| − | Other approaches are:
| + | ==Types== |
| − | *Various forms of [[virtualization]], allowing the code unlimited access only to virtual resources
| + | Cybercrime ranges from the fundamental invasion of [[privacy]], both personal and private, to crimes where the perpetrator hides in the anonymity of the internet, to attacks on the internet or computer network itself. |
| − | *Various forms of [[sandbox (computer security)|sandbox]] or [[Jail (computer security)|jail]]
| |
| − | *The security functions of [[Java (programming language)|Java]], in <code>java.security</code>
| |
| | | | |
| − | Such approaches, however, if not fully integrated with the operating system, would reduplicate effort and not be universally applied, both of which would be detrimental to security.
| + | ===Child Pornography=== |
| | + | The issue of child [[pornography]] has become more important due to its widespread distribution and availability on the [[internet]]. Child pornography is widely seen as a form of [[child abuse]] and its production, distribution, and possession is outlawed in most countries. Prohibition may include images or videos of children engaged in [[human sexuality|sexual acts]] or of nude children. Many American states have made efforts to pass legislation outlawing its transmission via the internet. |
| | | | |
| − | ===Academic research on malware: a brief overview===
| + | Of the 184 members of The International Criminal Police Organization (Interpol), 95 do not have comprehensive laws covering child pornography.<ref>[http://www.icmec.org/missingkids/servlet/NewsEventServlet?LanguageCountry=en_X1&PageId=2338 "New Study Reveals Child Pornography not a Crime in Most Countries,"] ''International Centre for Missing and Exploited Children.'' Retrieved August 2, 2007.</ref> This can be seen as simply a lack of awareness in those countries or also as a reflection of the varying [[norm]]s of sexuality around the world, where in some countries child brides are still seen as ideal. The lack of laws against child pornography in such countries has led to the use of internet hosts there for such material, safe from prosecution. |
| − | The notion of a self-reproducing computer program can be traced back to 1949 when [[John von Neumann]] presented lectures that encompassed the theory and organization of complicated automata.<ref>John von Neumann, "Theory of Self-Reproducing Automata," Part 1: Transcripts of lectures given at the University of Illinois, Dec. 1949, Editor: A. W. Burks, University of Illinois, USA, 1966.</ref> Neumann showed that in theory a program could reproduce itself. This constituted a plausibility result in [[computability theory]]. Fred Cohen experimented with computer viruses and confirmed Neumann's postulate. He also investigated other properties of malware (detectability, self-obfuscating programs that used rudimentary encryption that he called "evolutionary," and so on). His doctoral dissertation was on the subject of computer viruses.<ref>Fred Cohen, "Computer Viruses," PhD Thesis, University of Southern California, ASP Press, 1988.</ref> Cohen's faculty advisor, Leonard Adleman (the A in [[RSA]]) presented a rigorous proof that, in the general case, algorithmically determining whether a virus is or is not present is Turing undecidable.<ref>L. M. Adleman, "An Abstract Theory of Computer Viruses," Advances in Cryptology---Crypto '88, LNCS 403, pages 354-374, 1988.</ref> This problem must not be mistaken for that of determining, within a broad class of programs, that a virus is not present; this problem differs in that it does not require the ability to recognize all viruses. Adleman's proof is perhaps the deepest result in malware computability theory to date and it relies on [[Cantor's diagonal argument]] as well as the [[halting problem]]. Ironically, it was later shown by Young and Yung that Adleman's work in [[cryptography]] is ideal in constructing a virus that is highly resistant to reverse-engineering by presenting the notion of a [[Cryptovirology|cryptovirus]].<ref>A. Young, M. Yung, "Cryptovirology: Extortion-Based Security Threats and Countermeasures," IEEE Symposium on Security & Privacy, pages 129-141, 1996.</ref> A cryptovirus is a virus that contains and uses a public key. In the cryptoviral extortion attack, the virus hybrid encrypts [[plaintext]] data on the victim's machine using the virus writer's [[public key]]. In theory the victim must negotiate with the virus writer to get the plaintext back (assuming there are no backups). Analysis of the virus reveals the public key, not the needed private decryption key. This result was the first to show that [[computational complexity theory]] can be used to devise malware that is robust against reverse-engineering.
| |
| | | | |
| − | Another growing area of computer virus research is to mathematically model the infection behavior of worms using models such as [[Lotka-Volterra equation]]s, which has been applied in the study of biological virus. Various virus propagation scenarios have been studied by researchers such as propagation of computer virus, fighting virus with virus like predator codes,<ref>H. Toyoizumi, A. Kara. Predators: Good Will Mobile Codes Combat against Computer Viruses. Proc. of the 2002 New Security Paradigms Workshop, 2002</ref><ref>Zakiya M. Tamimi, Javed I. Khan, [http://www.medianet.kent.edu/publications/ICCCE06DL-2virusabstract-TK.pdf Model-Based Analysis of Two Fighting Worms], IEEE/IIU Proc. of ICCCE '06, Kuala Lumpur, Malaysia, May 2006, Vol-I, Page 157-163</ref> effectiveness of patching etc.
| + | ===Computer Viruses and other Malware=== |
| | + | '''Malware''' is software designed to infiltrate or damage a computer system without the owner's [[informed consent]]. It is a [[portmanteau]] of the words "[[Malice (legal term)|malicious]]" and "[[Computer software|software]]." The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code. The more specific term "[[computer virus]]" is however used in common parlance, and often in the [[mass media|media]], to describe all kinds of malware. |
| | | | |
| − | ===Emerging vectors and pathways===
| + | Software is considered malware based on the perceived intent of the creator rather than any particular features. It includes computer viruses, [[Computer worm|worms]], [[Trojan horse (computing)|trojan horse]]s, [[spyware]], dishonest [[adware]], and other malicious and unwanted software. In [[law]], malware may also be referred to as a "computer contaminant."<ref>[http://www.ncsl.org/programs/lis/cip/viruslaws.htm Virus/Contaminant/Destructive Transmission Statutes,] National Conference of State Legislatures. Retrieved August 2, 2007.</ref> |
| − | ====Wikis and Blogs====
| |
| − | Innocuous wikis and blogs are not immune to hijacking. It has been reported that the German edition of Wikipedia has recently been used as an attempt to vector infection. Through a form of [[social engineering]], users with ill intent have added links to web pages that contain malicious software with the claim that the web page would provide detections and remedies, when in fact it was a lure to infect.<ref>[http://www.tech2.com/india/news/telecom/wikipedia-hijacked-to-spread-malware/2667/0 Wikipedia Hijacked to Spread Malware]</ref>
| |
| | | | |
| − | ====Targeted SMTP Threats====
| + | Many early infectious programs, including the [[internet worm]] and a number of [[MS-DOS]] viruses, were written as experiments or pranks generally intended to be harmless or merely annoying rather than to cause serious damage. Since the rise of widespread [[broadband]] [[internet]] access, more malicious software has been designed for a [[profit]] motive. For instance, since 2003, the majority of widespread viruses and worms have been designed to take control of users' computers for [[black market]] exploitation. Infected "[[zombie computer]]s" are used to send [[#Spam|e-mail spam]], to host contraband data such as [[#Child Pornography|child pornography]], or to engage in [[#Denial of service attacks|distributed denial-of-service]] attacks as a form of [[extortion]].<ref>Daniel Tynan, |
| − | Targeted [[Simple Mail Transfer Protocol|SMTP]] threats also represent an emerging attack vector through which malware is propagated. As users adapt to widespread [[Spam (electronic)|spam]] attacks, cybercriminals distribute [[crimeware]] to target one specific organization or industry, often for financial gain.<ref>[http://www.avinti.com/download/market_background/whitepaper_email_crimeware_protection.pdf "Protecting Corporate Assets from E-mail Crimeware," Avinti, Inc., p.1] </ref>
| + | “Zombie PCs: Silent, Growing Threat,” ''PC World'' (July 9, 2004).</ref> |
| | | | |
| | + | Another strictly for-profit category of malware has emerged in [[spyware]]—programs designed to monitor users' web browsing, display unsolicited [[advertising|advertisements]], or redirect [[affiliate marketing]] revenues to the spyware creator. Spyware programs do not spread like viruses; they are generally installed by exploiting security holes or are packaged with user-installed software. |
| | | | |
| − | ==Denial of service attacks== | + | ===Denial of service attacks=== |
| − | In [[computer security]] and [[computer crime|crime]], a '''denial-of-service attack''' ('''DoS attack''') is an attempt to make a computer resource unavailable to its intended users. Although the means to, motives for and targets of a DoS attack may vary, it generally comprises the concerted, malevolent efforts of a person or persons to prevent an [[Internet]] [[Website|site]] or [[Web service|service]] from functioning efficiently or at all, temporarily or indefinitely.
| + | A denial-of-service attack (DoS attack) is an attempt to make a computer resource unavailable to its intended users. Although the means to, motives for, and targets of a DoS attack may vary, it generally comprises the concerted, malevolent efforts of a person or persons to prevent an [[Internet]] [[Website|site]] or [[Web service|service]] from functioning efficiently or at all, temporarily or indefinitely. Perpetrators of DoS attacks typically—but not exclusively—target sites or services hosted on high-profile web servers. Denial of service attacks are one form of computer [[sabotage]] whereby people can effectively ruin their target's operations for what could be a lengthy period of time. |
| | | | |
| − | Perpetrators of DoS attacks typically — but not exclusively — target sites or services hosted on high-profile web servers; a pair of [[DNS Backbone DDoS Attacks]], on October 22, 2002 and February 6, 2007, targeted [[DNS root servers]], in an apparent attempt to disable the Internet itself.
| + | ===File sharing=== |
| | + | File sharing is the practice of making [[computer file|file]]s available for other users to download over the [[internet]] and smaller [[computer network|networks]]. The duplication of [[copyright]]ed material, such as [[music]] and [[movie]]s, is well understood as illegal. However, the status of sharing computer files containing such data has been less clear. The Recording Industry Association of America (RIAA) was able to force Napster to close its music file sharing operation based on the fact that the shared files were stored on a central Napster computer. Subsequently, Napster and others have set up subscription based legal file sharing for music files. |
| | | | |
| − | One common method of attack involves saturating the target (victim) machine with external communications requests, such that it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable. In general terms, DoS attacks are implemented by:
| + | More controversial file sharing follows the [[peer-to-peer]] (P2P) model, where the files are stored on and served by personal computers of the users. Most people who engage in file sharing are also downloading files that other users share. Sometimes these two activities are linked together. P2P file sharing is distinct from file trading in that downloading files from a P2P network does not require uploading, although some networks either provide incentives for uploading such as credits or force the sharing of files being currently downloaded. |
| − | * forcing the targeted computer(s) to reset, or consume its resources such that it can no longer provide its intended service; and/or,
| |
| − | * obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.
| |
| | | | |
| − | Denial-of-service attacks are considered violations of the [[Internet Architecture Board|IAB]]'s [[Internet ethics|Internet proper use policy]]. They also commonly constitute violations of the [[Computer crime#Applicable laws|laws of individual nations]].
| + | Under U.S. [[law]], "the Betamax decision" ''([[Sony Corp. of America v. Universal City Studios, Inc.]])'', case holds that copying "technologies" are not "inherently" illegal, if substantial non-infringing use can be made of them. This decision, predating the widespread use of the [[internet]] applies to most data networks, including peer-to-peer networks, since distribution of correctly licensed files can be performed. These non-infringing uses include sending open source software, public domain files, and out of [[copyright]] works. Other [[jurisdiction]]s tend to view the situation in somewhat similar ways. |
| | | | |
| − | === Manifestions ===
| + | In practice, many of the files shared on peer-to-peer networks are copies of copyrighted popular [[music]] and [[movie]]s. Sharing of these copies among strangers is illegal in most jurisdictions. This has led many observers, including most media companies and some peer-to-peer critics, to conclude that the networks themselves pose grave threats to the established distribution model. The research that attempts to measure actual monetary loss has been somewhat equivocal. Whilst on paper the existence of these networks results in large losses, the actual income does not seem to have changed much since these networks started up. Whether the threat is real or not, both the Recording Industry Association of America (RIAA) and the Motion Picture Association of America (MPAA) have spent large amounts of money attempting to [[lobbying|lobby]] lawmakers for the creation of new laws, and some copyright owners pay companies to help legally challenge users engaging in illegal sharing of their material. |
| | | | |
| − | The [[United States Computer Emergency Readiness Team]] defines symptoms of DoS attacks to include: | + | Countries outside of the United States have served as havens for the hosting of file sharing software as the U.S. copyright laws are often difficult to enforce in these countries.<ref>Thomas Mennecke, [http://www.slyck.com/news.php?story=838 “Supreme Court Rules Against P2P Companies,”] ''Slyck News.'' (2005). Retrieved August 2, 2007.</ref> For example, the program Kazaa is owned by the Australian company Sharman Holdings, incorporated in [[Vanuatu]], and developed by two Dutch software engineers. The online index of bit torrents The Pirate Bay is hosted in [[Sweden]] with backup servers in [[Russia]].<ref>Ann Harrison, [http://www.wired.com/science/discoveries/news/2006/03/70358 “The Pirate Bay: Here to Stay?”] ''Wired'' (March 13, 2006). Retrieved August 2, 2007.</ref> |
| | | | |
| − | * unusually slow network performance (opening files or accessing web sites)
| + | ===Hacking=== |
| − | * unavailability of a particular web site
| + | A "hacker" is someone who gains illegal access to computers. This action can be done maliciously or with the intent of pointing out possible security risks. Microsoft Corporation, the American [[multinational corporation|multi-national]] computer technology corporation, and the [[Department of Defense]] are among those large organizations that have been the target of hackers. Hacking poses a risk to society as hackers can gain access to sensitive financial, personal, or security information that can then be used for [[extortion]] or exploited for an attack. Hacking can be understood as the cyber-version of [[industrial espionage]]. |
| − | * inability to access any web site
| |
| − | * dramatic increase in the number of spam emails received[http://www.us-cert.gov/cas/tips/ST04-015.html]
| |
| | | | |
| − | Not all service outages, even those that result from malicious activity, are necessarily denial-of-service attacks. Other methods of attack may include a denial of service as one component of a larger offensive.
| + | ===Identity theft=== |
| | + | The term "[[identity theft]]" encompasses a broad range of identification-based crimes. It can be sub-divided into four categories: financial identity theft (using another's name and Social Security number to obtain goods and services), criminal identity theft (posing as another when apprehended for a crime), identity cloning (using another's information to assume his or her identity in daily life), and business/commercial identity theft (using another's [[business]] name to obtain credit).<ref>[http://www.idtheftcenter.org/ Identity Theft Resource Center.] Retrieved July 3, 2007.</ref> |
| | | | |
| − | DoS attacks can also lead to problems in the network 'branches' around the actual computer being attacked. For example, the bandwidth of a router between the Internet and a [[Local Area Network|LAN]] may be consumed by a DoS, compromising not only the intended computer, but also the entire network.
| + | There are a number of methods used by identity thieves including stealing [[mail]] or rummaging through trash, eavesdropping on public transactions to obtain personal data, stealing personal information in computer databases (Trojan horses, hacking), [[infiltration]] of organizations that store large amounts of personal information, impersonating a trusted organization in an electronic communication ("[[phishing]]"), and the use of [[#Spam|spam]]. |
| | | | |
| − | If the DoS is conducted on a sufficiently large scale, entire geographical swathes of Internet connectivity can also be compromised by incorrectly configured or flimsy network infrastructure equipment without the attacker's knowledge or intent.
| + | The unlawful acquisition of legally attributed personal identifiers is made possible by serious breaches of [[privacy]]. For consumers it is usually due to personal naiveté in who they provide their information to or carelessness in protecting their information from theft (such as vehicle break-ins and home invasions). Surveys in the United States from 2003 to 2006 showed a decrease in the total number of victims but an increase in the total value of identity fraud to US$56.6 billion in 2006. The average fraud per person rose from $5,249 in 2003 to $6,383 in 2006.<ref>[http://www.privacyrights.org/ar/idtheftsurveys.htm Recent Surveys and Studies,] Privacy Clearing House. Retrieved August 2, 2007.</ref> In the [[United Kingdom]], the Home Office Identity Fraud Steering Committee reported that identity fraud costs the UK economy £1.7 billion.<ref>[http://www.identitytheft.org.uk/ “What is Identity theft?”] Home Office Identity Fraud Steering Committee. Retrieved August 2, 2007.</ref> Confusion over exactly what constitutes identity theft has led to claims that statistics may be exaggerated.<ref>Bruce Schneier, [http://www.schneier.com/blog/archives/2005/11/identity_theft.html Identity Theft Over-Reported,] Schneier.com. Retrieved August 2, 2007.</ref> |
| | | | |
| − | === Methods of attack === | + | ===Internet fraud=== |
| − | A "denial-of-service" attack is characterized by an explicit attempt by attackers to prevent legitimate users of a service from using that service. Examples include:
| + | The term "internet fraud" generally refers to any type of [[fraud]] scheme that uses one or more online services—such as chat rooms, e-mail, message boards, or websites—to present fraudulent solicitations to prospective victims, to conduct fraudulent transactions, or to transmit the proceeds of fraud to financial institutions or to others connected with the scheme. The [[Federal Bureau of Investigation]] and [[police]] agencies worldwide have people assigned to combat this type of fraud; according to figures from the FBI, U.S. companies' losses due to internet fraud in 2003 surpassed US$500 million. |
| | | | |
| − | * flooding a network, thereby preventing legitimate network traffic;
| + | Internet fraud is committed in several ways. In some cases, fictitious merchants advertise goods for very low prices and never deliver. However, that type of fraud is minuscule compared to [[Crime|criminal]]s using stolen [[credit card]] information to buy goods and services. |
| − | * disrupting a server by sending more requests than it can possibly handle, thereby preventing access to a service;
| |
| − | * preventing a particular individual from accessing a service;
| |
| − | * disrupting service to a specific system or person.
| |
| | | | |
| − | Attacks can be directed at any network device, including attacks on [[routing]] devices and [[World Wide Web|Web]], [[electronic mail]], or [[Domain Name System]] [[Server (computing)|server]]s.
| + | Some common types of internet fraud include identity theft, purchase scams, [[counterfeit]] money orders, "phishing" for sensitive information, and "clickfraud" whereby false hits are generated for websites in order to generate [[advertising]] money. |
| | | | |
| − | A DoS attack can be perpetrated in a number of ways. There are three basic types of attack:
| + | One famous category of internet fraud consists of those offenses classified as "419 scams," named as such for the section of the [[Nigeria]]n penal code under which they fall. In these schemes, would be thieves e-mail people claiming to have a large sum of money they need to wire out of the country for some reason (large [[tax]] burden, political persecution, [[civil war]], and so forth). They request for their victims to send them the fees for transferring this fortune to the victim's account in exchange for a portion of the wealth. The victim, of course, never receives the money transfer and loses the fee money they have already sent.<ref>[http://www.419eater.com/html/419faq.htm What is the '419' Scam?] 419 Eater. Retrieved August 2, 2007.</ref> This type of scam originated with schemes in the early 1980s in Nigeria, hence the alternate name of Nigerian Money Transfer Fraud. |
| − | # consumption of computational resources, such as bandwidth, disk space, or [[Central processing unit|CPU]] time;
| |
| − | # disruption of configuration information, such as [[routing]] information;
| |
| − | # disruption of physical network components.
| |
| − | | |
| − | A DoS attack may include execution of [[malware]] intended to:
| |
| − | * max out the [[CPU]]'s usage, preventing any work from occurring;
| |
| − | * trigger errors in the microcode of the machine;
| |
| − | * trigger errors in the sequencing of instructions, so as to force the computer into an unstable state or lock-up;
| |
| − | * exploits errors in the operating system to cause [[resource starvation]] and/or [[thrash (computer science)|thrashing]], i.e. to use up all available facilities so no real work can be accomplished;
| |
| − | * crash the operating system itself.
| |
| − | | |
| − | Malware commonly employed in such attacks includes [[Stacheldraht]]{{Fact|date=February 2007}}, [[Tribe Flood Network]]{{Fact|date=February 2007}} and [[Trinoo]]{{Fact|date=February 2007}}.
| |
| − | | |
| − | ====SYN floods====
| |
| − | | |
| − | A [[SYN flood]] sends a flood of [[SYN (TCP)|TCP/SYN]] packets, often with a spoofed sender address. Each of these packets are handled like a connection request, causing the server to spawn a [[half-open connection]], by sending back a TCP/SYN-ACK packet, and waiting for a [[ACK (TCP)|TCP/ACK]] packet in response from the sender address. However, because the sender address is forged, the response never comes. These half-open connections consume resources on the server and limit the number of connections the server is able to make, reducing the server's ability to respond to legitimate requests until after the attack ends.
| |
| − | | |
| − | When a computer wants to make a TCP/IP connection (the most common internet connection) to another computer, usually a server, an exchange of TCP/SYN and TCP/ACK packets of information occur. The computer requesting the connection, usually the client's or user's computer, sends a TCP/SYN packet which asks the server if it can connect. If the server will allow connections, it sends a TCP/SYN-ACK packet back to the client to say "Yes, you may connect." and reserves a space for the connection, waiting for the client to respond with a TCP/ACK packet detailing the specifics of its connection.
| |
| − | | |
| − | In a SYN flood the address of the client is often forged so that when the server sends the go-ahead back to the client, the message is never received because the client either doesn't exist or wasn't expecting the packet and subsequently ignores it. This leaves the server with a dead connection, reserved for a client that will never respond. Usually this is done to one server many times in order to reserve all the connections for unresolved clients, which keeps legitimate clients from making connections.
| |
| − | | |
| − | The classic "bad" example is that of a party. Only 50 people can be invited to a party, and invitations are available on a first-come first-serve basis. Fifty letters are sent to request invitations, but the letters all have false return addresses. The invitations are mailed to the return addresses of the request letters. Unfortunately, all of the return addresses provided were fake, so nobody, or at least nobody of interest, receives the invitations. Now, when someone actually wants to come to the party (view the website), there are no invitations left because all the invitations (connections) have been reserved for 50 supposed people who will never actually show up.
| |
| − | | |
| − | The classic SYN flood was most notably introduced in 1993 by members of the IRC community as a method of removing combatants from IRC channels or networks. The first UNIX programs to utilize these programs were synflood.c by osek (circa 1993) and nuke.c Satanic Mechanic (circa 1992/1993)
| |
| − | | |
| − | ====LAND attack====
| |
| − | | |
| − | A [[LAND|LAND attack]] involves sending a [[Spoofing attack|spoof]]ed [[SYN (TCP)|TCP/SYN]] packet (connection initiation) with the target host's [[IP address]] with an open port as both source and destination. The attack causes the targeted machine to reply to itself continuously and eventually crash.
| |
| − | | |
| − | ====ICMP floods====
| |
| − | {{see also|smurf attack|ping flood|ping of death}}
| |
| − | A [[smurf attack]] is one particular variant of a flooding DoS attack on the public Internet. It relies on mis-configured network devices that allow packets to be sent to all computer hosts on a particular network via the [[broadcast address]] of the network, rather than a specific machine. The network then serves as a [[smurf amplifier]]. In such an attack, the perpetrators will send large numbers of [[Internet Protocol|IP]] packets with the source address faked to appear to be the address of the victim. To combat Denial of Service attacks on the Internet, services like the [[Smurf Amplifier Registry]] have given [[network service provider]]s the ability to identify misconfigured networks and to take appropriate action such as [[Network layer firewall|filtering]].
| |
| − | | |
| − | [[Ping flood]] is based on sending the victim an overwhelming number of [[ping]] packets, usually using the "ping -f" command. It is very simple to launch, the primary requirement being access to greater [[bandwidth]] than the victim.
| |
| − | | |
| − | ====UDP floods====
| |
| − | UDP floods include "[[Fraggle attack]]s." In a '''fraggle attack''' an attacker sends a large amount of [[User Datagram Protocol|UDP]] echo traffic to IP [[broadcast address]]es, all of it having a fake source address. It is a simple rewrite of the [[smurf attack]] code.
| |
| − | | |
| − | ====Teardrop attack====
| |
| − | The '''Teardrop attack''' involves sending [[Internet Protocol|IP]] fragments with overlapping oversized payloads to the target machine. A bug in the [[TCP/IP]] [[IPv4#Fragmentation and reassembly|fragmentation re-assembly]] code caused the fragments to be improperly handled, crashing the operating system as a result of this.[http://www.cert.org/advisories/CA-1997-28.html]
| |
| − | [[Windows 3.1x]], [[Windows 95]] and [[Windows NT]] operating systems, as well as versions of [[Linux]] prior to 2.0.32 and 2.1.63 are vulnerable to this attack.
| |
| − | | |
| − | ====Peer-to-peer attacks====
| |
| − | | |
| − | Attackers have found a way to exploit a number of bugs in peer-to-peer servers to initiate DDoS attacks. The most aggressive of these peer-to-peer-DDoS attacks exploits [[DC++]]. Peer-to-peer attacks are different from regular botnet based attacks. With peer-to-peer there is no botnet and the attacker doesn’t have to communicate with the clients it subverts. Instead, the attacker acts as a ‘puppet master,’ instructing clients of large peer-to-peer file sharing hubs to disconnect from their peer-to-peer network and to connect to the victim’s website instead. As a result, several thousand computers may aggressively try to connect to a target website. While a typical web server can handle a few hundred connections/sec before performance begins to degrade, most web servers fail almost instantly under five or six thousand connections/sec. With a moderately big peer-to-peer attack a site could potentially be hit with up to 750,000 connections in a short order. The targetted web server will be plugged up and confused by the incoming connections. While peer-to-peer attacks are easy to identify with signatures, the large number of IP addresses that need to be blocked (often over 250,000 during the course of a big attack) means that this type of attack can overwhelm mitigation defenses. Even if a mitigation device can keep blocking IP addresses, there are other problems to consider. For instance, there is a brief moment where the connection is opened on the server side before the signature itself comes through. Only once the connection is opened to the server can the identifying signature be sent and detected, and the connection torn down. Even tearing down connections rapidly takes server resources and can harm the server <ref>{{cite web|url=http://www.prolexic.com/news/20070514-alert.php|title=P2P Distributed Denial of Service Attack Alert|author=Sop, Paul|year=2007}}</ref>.
| |
| − | | |
| − | ====Application level floods====
| |
| − | On [[Internet Relay Chat|IRC]], [[IRC floods]] are a common electronic warfare weapon.
| |
| − | | |
| − | Various DoS-causing [[Exploit (computer security)|exploits]] such as '''[[buffer overflow]]''' can cause server-running software to get confused and fill the disk space or consume all available memory or CPU time.
| |
| − | | |
| − | Other kinds of DoS rely primarily on brute force, flooding the target with an overwhelming flux of packets, oversaturating its connection bandwidth or depleting the target's system resources. Bandwidth-saturating floods rely on the attacker having higher bandwidth available than the victim; a common way of achieving this today is via '''Distributed Denial of Service''', employing a [[botnet]]. Other floods may use specific packet types or connection requests to saturate finite resources by, for example, occupying the maximum number of open connections or filling the victim's disk space with logs.
| |
| − | | |
| − | A "banana attack" is another particular type of DoS. It involves redirecting outgoing messages from the client back onto the client, preventing outside access, as well as flooding the client with the sent packets.
| |
| − | | |
| − | An attacker with access to a victim's computer may slow it until it is unusable or crash it by using a [[fork bomb]].
| |
| − | | |
| − | A 'Pulsing zombie' is a term referring to a special denial-of-service attack. A [[Computer networking|network]] is subjected to hostile [[ping]]ing by different attacker computers over an extended amount of time. This results in a degraded quality of service and increased workload for the network's resources. This type of attack is more difficult to detect than traditional denial-of-service attacks due to their surreptitious nature.
| |
| − | | |
| − | ====Nukes====
| |
| − | Nukes are malformed or specially crafted packets.
| |
| − | | |
| − | [[WinNuke]] is a type of nuke, exploiting the vulnerability in the [[NetBIOS]] handler in [[Windows 95]]. A string of out-of-band data is sent to [[Transmission Control Protocol|TCP]] port 139 of the victim machine, causing it to lock up and display a [[Blue Screen of Death]].
| |
| − | | |
| − | ==== Distributed attack ====
| |
| − | | |
| − | A '''distributed denial of service attack''' ('''DDoS''') occurs when multiple compromised systems flood the bandwidth or resources of a targeted system, usually one or more web servers. These systems are compromised by attackers using a variety of methods.
| |
| − | | |
| − | Malware can carry DDoS attack mechanisms; one of the more well known examples of this was [[MyDoom]]. Its DoS mechanism was triggered on a specific date and time. This type of DDoS involved hardcoding the target IP address prior to release of the malware and no further interaction was necessary to launch the attack.
| |
| − | | |
| − | A system may also be compromised with a trojan, allowing the attacker to download a zombie agent (or the trojan may contain one). Attackers can also break into systems using automated tools that exploit flaws in programs that listen for connections from remote hosts. This scenario primarily concerns systems acting as servers on the web.
| |
| − | | |
| − | [[Stacheldraht]] is a classic example of a DDoS tool. It utilizes a layered structure where the attacker uses a client program to connect to handlers, which are compromised systems that issue commands to the [[Zombie computer|zombie agents]], which in turn facilitate the DDoS attack. Agents are compromised via the handlers by the attacker, using automated routines to exploit vulnerabilities in programs that accept remote connections running on the targeted remote hosts. Each handler can control up to a thousand agents.<ref>[http://staff.washington.edu/dittrich/misc/stacheldraht.analysis.txt The "stacheldraht" distributed denial of service attack tool]</ref>
| |
| − | | |
| − | These collections of compromised systems are known as botnets. DDoS tools like stacheldraht still use classic DoS attack methods centered around [[IP spoofing]] and amplification like [[smurf attack]]s and fraggle attacks (these are also known as bandwidth consumption attacks). SYN floods (also known as resource starvation attacks) may also be used. Newer tools can use DNS servers for DoS purposes. (see next section)
| |
| − | | |
| − | Unlike MyDoom's DDoS mechanism, botnets can be turned against any IP address. [[Script kiddies]] use them to deny the availability of well known websites to legitimate users.<ref>[http://www.sans.org/resources/idfaq/trinoo.php Intrusion Detection FAQ: Distributed Denial of Service Attack Tools: trinoo and wintrinoo]</ref> More sophisticated attackers use DDoS tools for the purposes of [[extortion]] — even against their business rivals.<ref>[http://www.theregister.co.uk/2004/09/23/authorize_ddos_attack/ US credit card firm fights DDoS attack]</ref>
| |
| − | | |
| − | It is important to note the difference between a DDoS and DoS attack. If an attacker mounts a smurf attack from a single host it would be classified as a DoS attack. In fact, any attack against availability would be classed as a Denial of Service attack (e.g. using [[High-energy radio-frequency weapons]] to render computer equipment inoperable, would be a DoS attack, albeit an exotic one.)<ref>[http://news.zdnet.com/2100-9595_22-515644.html?legacy=zdnn Zap! ... and your PC's dead]</ref>. On the other hand, if an attacker uses a thousand zombie systems to simultaneously launch smurf attacks against a remote host, this would be classified as a DDoS attack.
| |
| − | | |
| − | The major advantages to an attacker of using a distributed denial-of-service attack are that multiple machines can generate more attack traffic than one machine, multiple attack machines are harder to turn off than one attack machine, and that the behavior of each attack machine can be stealthier, making it harder to track down and shut down. These attacker advantages cause challenges for defense mechanisms. For example, merely purchasing more incoming bandwidth than the current volume of the attack might not help, because the attacker might be able to simply add more attack machines.
| |
| − | | |
| − | ==== Reflected attack ====
| |
| − | A '''distributed reflected denial of service attack''' ('''DRDoS''') involves sending forged requests of some type to a very large number of computers that will reply to the requests. Using [[Internet protocol spoofing]], the source address is set to that of the targeted victim, which means all the replies will go to (and flood) the target.
| |
| − | | |
| − | ICMP Echo Request attacks (described above) can be considered one form of reflected attack, as the flooding host(s) send Echo Requests to the broadcast addresses of mis-configured networks, thereby enticing a large number of hosts to send Echo Reply packets to the victim. Some early DDoS programs implemented a distributed form of this attack.
| |
| − | | |
| − | Many services can be exploited to act as reflectors, some harder to block than others.<ref>Paxson, Vern (2001), ''[http://www.icir.org/vern/papers/reflectors.CCR.01/reflectors.html An Analysis of Using Reflectors for Distributed Denial-of-Service Attacks]''</ref> DNS amplification attacks involve a new mechanism that increased the amplification effect, using a much larger list of DNS servers than seen earlier.<ref>Vaughn, Randal and Evron, Gadi (2006), ''[http://www.isotf.org/news/DNS-Amplification-Attacks.pdf DNS Amplification Attacks]''</ref>
| |
| − | | |
| − | ==== Unintentional attack ====
| |
| − | This describes a situation where a website ends up denied, not due to a deliberate attack by a single individual or group of individuals, but simply due to a sudden enormous spike in popularity. This can happen when an extremely popular website posts a prominent link to a second, less well-prepared site, for example, as part of a news story. The result is that a significant proportion of the primary site's regular users — potentially hundreds of thousands of people — click that link in the space of a few hours, having the same effect on the target website as a DDoS attack.
| |
| − | | |
| − | News sites and link sites — sites whose primary function is to provide links to interesting content elsewhere on the Internet — are most likely to cause this phenomenon. The canonical example is the [[Slashdot effect]]. Sites such as [[Digg]], [[Fark]], [[Something Awful]] and the webcomic [[Penny Arcade (webcomic)|Penny Arcade]] have their own corresponding "effects," known as "the Digg effect," "farking," "[[goon]]rushing" and "wanging"; respectively.
| |
| − | | |
| − | Routers have also been known to create unintentional DoS attacks, as both [[D-Link]] and [[Netgear]] routers have created [[NTP vandalism]] by flooding NTP servers without respecting the restrictions of client types or geographical limitations.
| |
| − | | |
| − | Similar unintentional attacks can also occur via other media, e.g. when a URL is mentioned on television. If a server is being indexed by [[Google]] or another search engine during peak periods of activity, or does not have a lot of available bandwidth while being indexed, it can also experience the effects of a DoS attack.
| |
| − | | |
| − | ====Incidents====
| |
| − | The first major attack involving DNS servers as reflectors occurred in January 2001. The attack was directed at the site Register.com.<ref>[http://staff.washington.edu/dittrich/misc/ddos/register.com-unisog.txt January 2001 thread on the UNISOG mailing list]</ref> This attack, which forged requests for the MX records of AOL.com (to amplify the attack) lasted about a week before it could be traced back to all attacking hosts and shut off. It used a list of tens of thousands of DNS servers that were at least a year old (at the time of the attack.)
| |
| − | | |
| − | In July 2002, the Honeynet Project Reverse Challenge was issued.<ref>[http://www.honeynet.org/reverse Honeynet Project Reverse Challenge]</ref> The binary that was analyzed turned out to be yet another DDoS agent, which implemented several DNS related attacks, including an optimized form of a reflection attack.
| |
| − | | |
| − | On two occasions to date, attackers have performed [[DNS Backbone DDoS Attacks]] on the DNS root servers. Since these machines are intended to provide service to all Internet users, these two denial of service attacks might be classified as attempts to take down the entire Internet, though it is unclear what the attackers' true motivations were. The first occurred in October 2002, and disrupted service at 9 of the 13 root servers. The second occurred in February 2007, and caused disruptions at two of the root servers.
| |
| − | | |
| − | === Prevention and response ===
| |
| − | ==== Surviving attacks ====
| |
| − | | |
| − | The investigative process should begin immediately after the DoS attack begins. There will be multiple phone calls, call backs, emails, pages and faxes between the victim organization, one's provider and others involved. It is a time consuming process, so the process should begin immediately. It has taken some very large networks with plenty of resources several hours to halt a DDoS.
| |
| − | | |
| − | The easiest way to survive an attack is to have planned for the attack. Having a separate emergency block of IP addresses for critical servers with a separate route can be invaluable. A separate route (perhaps a DSL) is not that extravagant, and it can be used for load balancing or sharing under normal circumstances and switched to emergency mode in the event of an attack.
| |
| − | | |
| − | Filtering is often ineffective, as the route to the filter will normally be swamped so only a trickle of traffic will survive. However, by using an extremely resilient stateful packet filter that will inexpensively<ref>ie. without consuming much processing power</ref> drop any unwanted packets, surviving a DDoS attack becomes much easier. When such a high performance packet filtering server is attached to an ultra high bandwidth connection (preferably an Internet backbone), communication with the outside world will be unimpaired so long as not all of the available bandwidth is saturated, and performance behind the packet filter will remain normal as long as the packet filter drops all DDoS packets.<ref>[[OpenBSD]]'s [[PF (firewall)|pf]] is a packet filter some providers use for exactly this purpose. [https://gold.rayservers.com/ddos-protection]</ref> It should be noted however, that in this case the victim of the DDoS attack still would need to pay for the excessive bandwidth. The price of service unavailability thus needs to be weighed against the price of truly exorbitant bandwidth/traffic.
| |
| − | | |
| − | ==== SYN Cookies ====
| |
| − | [[SYN cookies]] modify the TCP protocol handling of the server by delaying allocation of resources until the client address has been verified. This seems to be the most powerful defense against SyN attacks. There are [[Solaris Operating System|Solaris]] and [[Linux]] implementations. The Linux implementation can be turned on during runtime of the Linux kernel.
| |
| − | | |
| − | ==== Firewalls ====
| |
| − | [[Firewall (networking)|Firewall]]s have simple rules such as to allow or deny protocols, ports or IP addresses. Some DoS attacks are too complex for today's firewalls, e.g. if there is an attack on port 80 (web service), firewalls cannot prevent that attack because they cannot distinguish good traffic from DoS attack traffic. Additionally, firewalls are too deep in the network hierarchy. Your router may be affected even before the firewall gets the traffic. Nonetheless, firewalls can effectively prevent users from launching simple flooding type attacks from machines behind the firewall.[http://unixclan.no-ip.org/blog/?p=7]
| |
| − | | |
| − | Modern [[stateful firewall]]s like [[Check Point]] FW1 NGX & [[Cisco PIX]] have a built-in capability to differentiate good traffic from DoS attack traffic. This capability is known as a "Defender," as it confirms TCP connections are valid before proxying TCP packets to service networks (including border routers). A similar ability is present in OpenBSD's pF, which is available for other BSDs as well. In that context, it is called "synproxy."
| |
| − | | |
| − | ==== Switches ====
| |
| − | Most switches have some rate-limiting and [[Access control list|ACL]] capability. Some switches provide automatic and or system-wide rate limiting, traffic shaping, [[delayed binding]] ([[TCP splicing]]), [[deep packet inspection]] and [[Bogon filtering]] (bogus IP filtering) to detect and remediate denial of service attacks through automatic rate filtering and WAN Link failover and balancing.
| |
| − | | |
| − | These schemes will work as long as the DoS attacks are something that can be prevented using them. For example SYN flood can be prevented using delayed binding or TCP splicing. Similarly content based DoS can be prevented using deep packet inspection. Attacks originating from dark addresses or going to dark addresses can be prevented using Bogon filtering. Automatic rate filtering can work as long as you have set rate-thresholds correctly and granularly. Wan-link failover will work as long as both links have DoS/DDoS prevention mechanism.
| |
| − | | |
| − | ==== Routers ====
| |
| − | Similar to switches, routers have some rate-limiting and [[Access control list|ACL]] capability. They, too, are manually set. Most routers can be easily overwhelmed under DoS attack. If you add rules to take flow statistics out of the router during the DoS attacks, they further slow down and complicate the matter. [[Cisco IOS]] has features that prevents flooding, i.e. example settings [http://www.geocities.com/nonlinearphysics/cisco_ios_qos.html].
| |
| − | | |
| − | ====Application front end hardware====
| |
| − | Application front end hardware is intelligent hardware placed on the network before traffic reaches the servers. It can be used on networks in conjunction with routers and switches. Application front end hardware analyzes data packets as they enter the system, and then identifies them as priority, regular, or dangerous. There are more than 25 bandwidth management vendors. Hardware acceleration is key to bandwidth management. Look for granularity of bandwidth management, hardware acceleration, and automation while selecting an appliance.
| |
| − | | |
| − | ==== IPS based prevention ====
| |
| − | [[Intrusion-prevention system]]s are effective if the attacks have signatures associated with them. However, the trend among the attacks is to have '''legitimate content but bad intent'''. IPS systems which work on content recognition cannot block behavior based DoS attacks.
| |
| − | | |
| − | An ASIC based IPS can detect and block denial of service attacks because they have the processing power and the granularity to analyze the attacks and act like a circuit breaker in an automated way.
| |
| − | | |
| − | A rate-based IPS (RBIPS) must analyze traffic granularly and continuously monitor the traffic pattern and determine if there is traffic anomaly. It must let the legitimate traffic flow while blocking the DoS attack traffic.
| |
| − | | |
| − | | |
| − | ==Spam==
| |
| − | {{Unreferenced|date=July 2006}}
| |
| − | [[Image:spammed-mail-folder.png|thumb|300px|A [[KMail]] folder of spam messages.]]
| |
| − | '''Spamming''' is the abuse of electronic messaging systems to send unsolicited bulk messages, which are generally undesired. While the most widely recognized form of spam is [[email spam]], the term is applied to similar abuses in other media: [[Messaging spam|instant messaging spam]], [[Newsgroup spam|Usenet newsgroup spam]], [[spamdexing|Web search engine spam]], [[spam in blogs]], [[mobile phone spam|mobile phone messaging spam]], [[internet forum]] spam and [[Junk fax|junk fax transmissions]].
| |
| − | Spam is also called junk mail. Some email clients or servers have spam filters, which try to delete or move the spam messages.
| |
| − | | |
| − | Spamming is economically viable because advertisers have no operating costs beyond the management of their mailing lists, and it is difficult to hold senders accountable for their mass mailings. Because the [[barrier to entry]] is so low, spammers are numerous, and the volume of unsolicited mail has become very high. The costs, such as lost productivity and fraud, are borne by the public and by [[Internet service provider]]s, which have been forced to add extra capacity to cope with the deluge. Spamming is widely reviled, and has been the subject of legislation in many jurisdictions.
| |
| − | | |
| − | === Spamming in different media ===
| |
| − | ==== Instant Messaging and Chat Room spam ====
| |
| − | | |
| − | | |
| − | Instant Messaging spam, sometimes termed ''spim'' (a [[portmanteau]] of spam and IM, short for instant messenger), makes use of [[instant messaging]] systems, such as [[AOL Instant Messenger]] or [[ICQ]]. Many IM systems offer a user directory, including demographic information that allows an advertiser to gather the information, sign on to the system, and send unsolicited messages. To send instant messages to millions of users requires scriptable software and the recipients' IM usernames. Spammers have similarly targeted [[Internet Relay Chat]] channels, using [[IRC bot]]s that join channels and bombard them with advertising.
| |
| − | | |
| − | Messenger service spam has lent itself to spammer use in a particularly circular scheme. In many cases, messenger spammers send messages to vulnerable machines consisting of text like ''"Annoyed by these messages? Visit this site."'' The link leads to a Web site where, for a fee, users are told how to disable the Windows messenger service. Though the messenger service is easily disabled for free, the scam works because it creates a perceived need and offers a solution. Often the only "annoying messages" the user receives through Messenger are ads to disable Messenger itself. It is often using a false ID to get money or credit card numbers.
| |
| − | | |
| − | ==== Chat spam ====
| |
| − | Chat spam can occur in any live chat environment like [[IRC]] and in-game multiplayer chat of online games. It consists of repeating the same word or sentence many times to get attention or to interfere with normal operations. It is generally considered very rude and may lead to swift exclusion of the user from the used chat service by the owners or moderators.
| |
| − | | |
| − | The application of the name "Spam" to unwanted communication originates in Chat-room spam. Specifically, it was developed in the chat-rooms of People-Link in the early 1980s as a technique for getting rid of unwelcome newcomers. When someone would enter a chat-room full of friends who were in mid-conversation, and when the newcomer tried to turn the conversation in an unwelcome direction, two veteran members of the room would begin typing in the Monty Python “Spam” routine at high speed. They would fill the screen with “Spam Spam Spam eggs Spam Spam and Spam” etc, and make all other communication impossible. The other members of the room would just wait quietly until the newcomer got disgusted and moved on to a different room.
| |
| − | | |
| − | ==== Newsgroup spam and forum spam ====
| |
| − | {{main|Newsgroup spam}}
| |
| − | {{main|Forum spam}}
| |
| − | | |
| − | ==== Mobile phone spam ====
| |
| − | | |
| − | | |
| − | Mobile phone spam is directed at the [[text messaging]] service of a [[mobile phone]]. This can be especially irritating to customers not only for the inconvenience but also because of the fee that they are charged per text message.
| |
| − | The term "SpaSMS" was coined at the adnews website Adland in 2000 to describe spam SMS.
| |
| − | | |
| − | ==== Online game messaging spam ====
| |
| − | Many online games allow players to contact each other via player-to-player messaging, chatrooms, or public discussion areas. What qualifies as spam varies from game to game, but usually this term applies to all forms of message flooding, violating the terms of service contract for the website.
| |
| − | | |
| − | ==== Spam targeting search engines (spamdexing) ====
| |
| − | | |
| − | | |
| − | '''Spamdexing''' (a [[portmanteau]] of ''spamming'' and ''indexing'') refers to the practice on the [[World Wide Web]] of modifying [[HTML]] pages to increase the chances of them being placed high on [[search engine]] relevancy lists. These sites use "black hat [[search engine optimization]] techniques" to unfairly increase their rank in search engines. Many modern search engines modified their search algorithms to try to exclude web pages utilizing spamdexing tactics.
| |
| − | | |
| − | ==== Blog, wiki, and guestbook spam ====
| |
| − | | |
| − | [[Blog spam]], or "blam" for short, is spamming on [[weblog]]s. In 2003, this type of spam took advantage of the open nature of comments in the blogging software [[Movable Type]] by repeatedly placing comments to various blog posts that provided nothing more than a link to the spammer's commercial web site.<ref>[http://www.wired.com/wired/archive/12.03/google.html?pg=7 The (Evil) Genius of Comment Spammers] - ''Wired Magazine'', March 2004</ref>
| |
| − | Similar attacks are often performed against [[wiki]]s and [[guestbook]]s, both of which accept user contributions.
| |
| − | | |
| − | === Noncommercial spam ===
| |
| − | E-mail and other forms of spamming have been used for purposes other than advertisements. Many early Usenet spams were religious or political. [[Serdar Argic]], for instance, spammed Usenet with historical revisionist screeds. A number of [[evangelism|evangelists]] have spammed [[Usenet]] and e-mail media with preaching messages. A growing number of criminals are also using spam to perpetrate various sorts of fraud,<ref>See: [[Advance fee fraud]]</ref> and in some cases have used it to lure people to locations where they have been kidnapped, held for ransom, and even murdered.<ref>[http://www.news24.com/News24/South_Africa/News/0,,2-7-1442_1641875,00.html SA cops, Interpol probe murder] - ''News24.com'', 2004-[[12-31]]</ref>
| |
| − | | |
| − | ==== Hobbit spam ====
| |
| − | In early July 2006 there has been an enormous increase in unsolicited messages from a spoofed address with approximately half a dozen random letter subjects, containing nothing but three lines from JRR [[Tolkien]]'s ''[[The Hobbit]]''. This follows fairly closely another similar form dubbed "[[Discordianism|discordian]] poetry" that appeared to used a random word generator of the same. The messages had no attempt to sell anything; it was theorised that this was a [[script kiddie]] ineptly running a spam suite. This was confirmed when shortly afterward the same format messages began appearing with image files overlaying the text (a common spam technique). It is suspected to be a variation from the same source and image overlays will begin appearing.<ref>[http://publications.mediapost.com/index.cfm?fuseaction=Articles.showArticleHomePage&art_aid=45537 Just An Online Minute... Hobbit Spam] - ''MediaPost Publications'', 2006-[[07-13]]</ref>
| |
| − | | |
| − | ==== Spam as denial of service ====
| |
| − | Spamming has also been used as a [[denial of service]] ("DoS") tactic, particularly on Usenet. By overwhelming the readers of a newsgroup with an inordinate number of nonsense messages, legitimate messages and computing resources can be lost in the deluge. Since these messages are usually forged (that is, sent falsely under regular posters' names) this tactic has come to be known as [[sporgery]] (from ''spam'' + ''forgery''). This tactic has for instance been used by members of the [[Church of Scientology]] against the [[alt.religion.scientology]] newsgroup (see [[Scientology versus the Internet]]) and by spammers against [[news.admin.net-abuse.email]], a forum for mail administrators to discuss spam problems. Applied to e-mail, this is termed [[E-mail bomb|mailbombing]]. The Usenet [[Meow Wars]] (around 1996) were DoS attacks on various newsgroups aimed at specific posters that disrupted the newsgroups where they were active. The DoS attacks launched by [[Hipcrime (Usenet)|Hipcrime]], which continue today, are more crafted as DoS attacks on entire newsgroups. The [[alt.sex]] newsgroups were rendered uninhabitable by commercial porn site spammers, partially for advertising purposes and partially to destroy a perceived free competitor. (This spawned the creation of the moderated, unspammable [[soc.sexuality]] newsgroups.)
| |
| − | | |
| − | Forged e-mail spam has been used as a tool of [[harassment]]. The spammer collects a list of addresses, then sends a spam to them signed with the name of the person he or she wishes to harass. Some recipients, angry they received spam and seeing an obvious "source," will respond angrily or pursue revenge against the apparent spammer, the forgery victim. A widely known victim of this sort of harassment was Joe's CyberPost,<ref>[http://www.joes.com/spammed.html Spam Attack!] - ''Joe's CyberPost''</ref> which has lent its name to the offense: it is known as a ''[[joe job]]''. "Joe jobs" have been used against antispammers: in recent examples, [[Steve Linford]] of [[Spamhaus Project]] and [[Timothy Walton]], a California attorney, have been targeted. Sometimes victims (such as [[ROKSO]]-listed spammers) are subscribed to lists that don't practice verified opt-in, such as magazine subscriptions and e-mail newsletters, a practise known as [[subscriptionbombing]].
| |
| − | | |
| − | Spammers have abused resources set up for the purposes of anonymous speech online, such as [[anonymous remailer]]s. Many of these resources have been shut down, denying their services to legitimate users.
| |
| − | | |
| − | E-mail [[computer virus|worms or viruses]] may be spammed to set up an initial pool of infected machines, which resend the virus to other machines in a spam-like manner. The infected machines can often be used as remote-controlled [[zombie computers]], for more spamming or [[DDoS]] attacks. [[Trojan horse (computing)|trojan]]s are spammed to [[phishing|phish]] for bank account details, or to set up a pool of zombies without using a virus.
| |
| − | | |
| − | ==== In gaming ====
| |
| − | | |
| − | | |
| − | In gaming, spamming is often used to describe repetitive and disruptive behavior.
| |
| − | | |
| − | In first person shooter type games, spamming refers to tactics where a player repeatedly and randomly fires into an area in the hope of scoring chance hits. Many games attempt to limit this by providing scenarios such as [[Capture the Flag]].
| |
| − | | |
| − | Spamming also describes players who repeatedly use a particular move to gain benefits over other players. This is often seen in [[Player versus Player|PvP]] combat as well as [[MMORPG]] games.
| |
| − | | |
| − | The term also refers to the flooding of the in-game [[chat]] with frequent messaging, this is similar to [[messaging spam]] mentioned above.
| |
| − | | |
| − | === History ===
| |
| − | | |
| − | | |
| − | The term ''spam'' is derived from the [[Monty Python]] '''[[Spam (Monty Python)|SPAM sketch]]''' (see video in External Links), set in a [[cafe]] where nearly every item on the menu includes [[Spam (food)|SPAM]] luncheon meat. As the server recites the SPAM-filled menu, a chorus of [[Viking]] patrons drowns out all conversations with a song repeating "SPAM, SPAM, SPAM, SPAM... lovely SPAM, wonderful SPAM," hence "SPAMming" the dialogue. The excessive amount of SPAM mentioned in the sketch is a reference to [[United Kingdom|British]] rationing during [[World War II]]. SPAM was one of the few foods that was widely available.
| |
| − | | |
| − | Although the first known instance of unsolicited commercial e-mail occurred in 1978<ref>[http://www.templetons.com/brad/spamreact.html Reaction to the DEC Spam of 1978]</ref> (unsolicited electronic messaging had already taken place over other media, with the first recorded instance being via telegram on September 13 1904{{Fact|date=January 2007}}), the term "spam" for this practice had not yet been applied. In the 1980s the term was adopted to describe certain abusive users who frequented [[Bulletin Board System|BBS]]s and [[MUD]]s, who would repeat "SPAM" a huge number of times to scroll other users' text off the screen.<ref>http://www.templetons.com/brad/spamterm.html</ref> In early Chat rooms services like PeopleLink and the early days of AOL, they actually flooded the screen with quotes from the Monty Python Spam sketch. This was used as a tactic by insiders of a group that wanted to drive newcomers out of the room so the usual conversation could continue. It was also used to prevent members of rival groups from chatting — for instance, Star Wars fans often invaded Star Trek chat rooms, filling the space with blocks of text until the Star Trek fans left.<ref>[http://www.myshelegoldberg.com/writings/essays/spam.htm The Origins of Spam in Star Trek chatrooms]</ref> This act, previously called ''flooding'' or ''trashing'', came to be known as ''spamming''.<ref>[http://groups.google.com/groups?threadm=MAT.90Sep25210959%40zeus.organpipe.cs.arizona.edu Spamming? (rec.games.mud)] - ''Google Groups USENET archive'', 1990-[[09-26]]</ref> The term was soon applied to a large amount of text broadcasted by many users.
| |
| − | | |
| − | It later came to be used on [[Usenet]] to mean ''excessive multiple posting''—the repeated posting of the same message. The unwanted message would appear in many if not all newsgroups, just as SPAM appeared in all the menu items in the Monty Python sketch. The first usage of this sense was by [[Joel Furr]] in the aftermath of the [[ARMM (Usenet)|ARMM]] incident of March 31 1993, in which a piece of experimental software released dozens of recursive messages onto the ''news.admin.policy'' newsgroup. This use had also become established—to spam Usenet was flooding newsgroups with junk messages. As a [[portmanteau]] of "spew" and "scam," the word was also attributed to the flood of "Make Money Fast" messages that clogged many newsgroups during the 1990s.
| |
| − | | |
| − | Commercial spamming started in force on March 5, 1994, when a pair of lawyers, [[Canter & Siegel|Laurence Canter and Martha Siegel]], began using bulk [[Usenet]] posting to advertise [[immigration]] law services. The incident was commonly termed the "[[Green Card spam]]," after the subject line of the postings. The two went on to widely promote spamming of both Usenet and e-mail as a new means of advertisement—over the objections of Internet users they labeled "anti-commerce radicals." Within a few years, the focus of spamming (and antispam efforts) moved chiefly to e-mail, where it remains today.<ref>[http://www.templetons.com/brad/spamterm.html Origin of the term "spam" to mean net abuse]</ref>
| |
| − | | |
| − | There are three popular [[false etymology|false etymologies]] of the word "spam." The first, promulgated by Canter & Siegel themselves, is that "spamming" is what happens when one dumps a can of SPAM luncheon meat into a fan blade. The second is the [[backronym]] "'''s'''hit '''p'''osing '''a'''s '''m'''ail." The third is similar, using "'''s'''tupid '''p'''ointless '''a'''nnoying '''m'''essages."
| |
| − | | |
| − | In 1998, the [[New Oxford Dictionary of English]], which had previously only defined "spam" in relation to the trademarked food product, added a second definition to its entry for "spam": "Irrelevant or inappropriate messages sent on the Internet to a large number of newsgroups or users."<Ref>[http://news.com.com/2100-1023-214535.html "Oxford dictionary adds Net terms" on News.com]</Ref>
| |
| − | | |
| − | [[Hormel Foods Corporation]], the makers of SPAM luncheon meat, do not object to the Internet use of the term "spamming." However, they did ask that the capitalized word "SPAM" be reserved to refer to their product and trademark.<ref>[http://www.spam.com/legal/spam/ SPAM and the Internet] - ''Official SPAM Website''</ref> By and large, this request is obeyed in forums which discuss spam. In Hormel Foods v SpamArrest, Hormel attempted to assert its trademark rights against SpamArrest, a software company, from using the mark "spam," since Hormel owns the trademark. In a dilution claim, Hormel argued that Spam Arrest's use of the term "spam" had endangered and damaged "substantial goodwill and good reputation" in connection with its trademarked lunch meat and related products. Hormel also asserts that Spam Arrest's name so closely resembles its luncheon meat that the public might become confused, or might think that Hormel endorses Spam Arrest's products. Hormel did not prevail. Attorney Derek Newman responded on behalf of Spam Arrest: "Spam has become ubiquitous throughout the world to describe unsolicited commercial e-mail. No company can claim trademark rights on a generic term." Hormel stated on its website: "Ultimately, we are trying to avoid the day when the consuming public asks, 'Why would Hormel Foods name its product after junk email?'"<ref>[http://img.spamarrest.com/HormelSummaryJudgment.pdf Hormel Foods v SpamArrest, Motion for Summary Judgement, Redacted Version (PDF)]</ref>
| |
| − | | |
| − | Hormel also made two attempts that were dismissed in 2005 to revoke the mark "SPAMBUSTER".<ref>[http://www.lawreports.co.uk/WLRD/2005/CHAN/chanjanf0.3.htm Hormel Foods Corpn v Antilles Landscape Investments NV (2005) EWHC 13 (Ch)]</ref>
| |
| − | | |
| − | Hormel's Corporate Attorney Melanie J. Neumann also sent [[SpamCop]]'s Julian Haight a letter on August 27, 1999 requesting that he delete an objectionable image (a can of Hormel's SPAM luncheon meat product in a trash can), change references to UCE spam to all lower case letters, and confirm his agreement to do so.<ref>[http://www.spamcop.net/images/hormel_letter.gif Letter from Hormel's Corporate Attorney Melanie J. Neumann to SpamCop's Julian Haight]</ref>
| |
| − | | |
| − | === Costs of spam ===
| |
| − | The [[European Union]]'s Internal Market Commission estimated in 2001 that "junk e-mail" cost Internet users €10 billion per year worldwide. <ref>[http://europa.eu/rapid/pressReleasesAction.do?reference=IP/01/154&format=HTML&aged=0&language=EN&guiLanguage=en "Data protection: "Junk" e-mail costs internet users 10 billion a year worldwide - Commission study"]</ref>
| |
| − | | |
| − | The California legislature found that spam cost United States organizations alone more than $10 billion in 2004, including lost productivity and the additional equipment, software, and manpower needed to combat the problem.{{Fact|date=March 2007}}
| |
| − | | |
| − | Spam's direct effects include the consumption of computer and network resources, and the cost in human time and attention of dismissing unwanted messages. In addition, spam has costs stemming from the ''kinds'' of spam messages sent, from the ''ways'' spammers send them, and from the ''[[arms race]]'' between spammers and those who try to stop or control spam. In addition, there are the opportunity cost of those who forgo the use of spam-afflicted systems. There are the direct costs, as well as the indirect costs borne by the victims - both those related to the spamming itself, and to other crimes that usually accompany it, such as financial theft, [[identity theft]], data and intellectual property theft, virus and other malware infection, child pornography, fraud, and deceptive marketing.
| |
| − | | |
| − | The methods of spammers are likewise costly. Because spamming contravenes the vast majority of ISPs' acceptable-use policies, most spammers have for many years gone to some trouble to conceal the origins of their spam. E-mail, Usenet, and instant-message spam are often sent through insecure [[proxy server]]s belonging to unwilling third parties. Spammers frequently use false names, addresses, phone numbers, and other contact information to set up "disposable" accounts at various Internet service providers. In some cases, they have used falsified or stolen [[credit card]] numbers to pay for these accounts. This allows them to quickly move from one account to the next as each one is discovered and shut down by the host ISPs.
| |
| − | | |
| − | The costs of spam also include the collateral costs of the struggle between spammers and the administrators and users of the media threatened by spamming. <!-- This is incomplete —><ref>[http://linxnet.com/misc/spam/thank_spammers.html Thank the Spammers] - ''William R. James''
| |
| − | 2003-[[03-10]]</ref>
| |
| − | | |
| − | Many users are bothered by spam because it impinges upon the amount of time they spend reading their e-mail. Many also find the content of spam frequently offensive, in that [[pornography]] is one of the most frequently advertised products. Spammers send their spam largely indiscriminately, so pornographic ads may show up in a work place e-mail inbox—or a child's, the latter of which is illegal in many jurisdictions. Recently, there has been a noticeable increase in spam advertising websites that contain [[child pornography]].
| |
| − | | |
| − | Some spammers argue that most of these costs could potentially be alleviated by having spammers reimburse ISPs and individuals for their material. There are two problems with this logic: first, the rate of reimbursement they could credibly budget is not nearly high enough to pay the direct costs; and second, the human cost (lost mail, lost time, and lost opportunities) is basically unrecoverable.
| |
| − | | |
| − | E-mail spam exemplifies a [[tragedy of the commons]]: spammers use resources (both physical and human), without bearing the entire cost of those resources. In fact, spammers commonly do not bear the cost at all. This raises the costs for everyone. In some ways spam is even a potential threat to the entire e-mail system, as operated in the past.
| |
| − | | |
| − | Since e-mail is so cheap to send, a tiny number of spammers can saturate the Internet with junk mail. Although only a tiny percentage of their targets are motivated to purchase their products (or fall victim to their scams), the low cost may provide a sufficient conversion rate to keep the spamming alive. Furthermore, even though spam appears not to be economically viable as a way for a reputable company to do business, it suffices for professional spammers to convince a tiny proportion of gullible advertisers that it is viable for those spammers to stay in business. Finally, new spammers go into business every day, and the low costs allow a single spammer to do a lot of harm before finally realizing that the business is not profitable.
| |
| − | | |
| − | Some companies and groups "rank" spammers; spammers who make the news are sometimes referred to by these rankings.<ref>Spamhaus' [http://www.spamhaus.org/statistics/networks.lasso "TOP 10 spam service ISPs"]</ref><ref>[http://www.spamhaus.org/statistics/spammers.lasso The 10 Worst ROKSO Spammers]</ref> The secretive nature of spamming operations makes it difficult to determine how proliferated an individual spammer is, thus making the spammer hard to track, block or avoid. Also, spammers may target different networks to different extents, depending on how successful they are at attacking the target. Thus considerable resources are employed to actually measure the amount of spam generated by a single person or group. For example, victims that use common antispam hardware, software or services provide opportunities for such tracking. Nevertheless, such rankings should be taken with a pinch of salt.
| |
| − | | |
| − | ==== General costs of spam ====
| |
| − | In all cases listed above, including both commercial and non-commercial, "spam happens" due to a positive [[Cost-benefit analysis]] result.
| |
| − | | |
| − | '''Cost''' is the combination of
| |
| − | *Overhead: The costs and overhead of electronic spamming include bandwidth, developing or acquiring an email/wiki/blog spam tool, taking over or acquiring a host/zombie, etc.
| |
| − | *[[Transaction cost]]: The incremental cost of contacting each additional recipient once a method of spamming is constructed, multiplied by the number of recipients. (see [[CAPTCHA]] as a method of increasing transaction costs)
| |
| − | *Risks: Chance and severity of legal and/or public reactions, including [[damages]] and [[punitive damages]]
| |
| − | *Damage: Impact on the community and/or communication channels being spammed (see [[Newsgroup spam]])
| |
| − | | |
| − | '''Benefit''' is the total expected profit from spam, which may include any combination of the commercial and non-commercial reasons listed above. It is normally linear, based on the incremental benefit of reaching each additional spam recipient, combined with the [[conversion rate]].
| |
| − | | |
| − | Spam is prevalent on the Internet because the transaction cost of electronic communications is radically less than any alternate form of communication, far outweighing the current potential losses, as seen by the amount of spam currently in existence. Spam continues to spread to new forms of electronic communication as the gain (number of potential recipients) increases to levels where the cost/benefit becomes positive. Spam has most recently evolved to include wikispam and blogspam as the levels of readership increase to levels where the overhead is no longer the dominating factor. According to the above analysis, spam levels will continue to increase until the cost/benefit analysis is balanced {{Fact|date=January 2007}}.
| |
| − | | |
| − | === In crime ===
| |
| − | {{sectstub}}
| |
| − | | |
| − | Spam can be used to spread [[computer virus]]es, [[Trojan horse (computing)|trojan horse]]s or other malicious software. The objective may be [[identity theft]], or worse (eg. [[advance fee fraud]]). Some spam attempts to capitalise on human greed whilst other attempts to use the victims inexperience with computers to trick them (eg. [[Phishing]]).
| |
| − | | |
| − | === Political issues ===
| |
| − | {{pov-section}}
| |
| − | Spamming remains a hot discussion topic. In 2004, the seized [[Porsche]] of an indicted spammer was advertised on the Internet;[http://www.timewarner.com/corp/newsroom/pr/0,20812,670327,00.html] this revealed the extent of the financial rewards available to those who are willing to commit duplicitous acts online. However, some of the possible means used to stop spamming may lead to other side effects, such as increased government control over the Internet, loss of privacy, barriers to free expression, and the commercialization of e-mail.
| |
| − | | |
| − | One of the chief values favored by many long-time Internet users and experts, as well as by many members of the public, is the free exchange of ideas. Many have valued the relative [[anarchy (word)|anarchy]] of the Internet, and bridle at the idea of restrictions placed upon it.{{Fact|date=February 2007}} A common refrain from spam-fighters is that spamming itself abridges the historical freedom of the Internet, by attempting to force users to carry the ''costs'' of material which they would not choose.
| |
| − | | |
| − | An ongoing concern expressed by parties such as the [[Electronic Frontier Foundation]] and the [[ACLU]] has to do with so-called "stealth blocking," a term for ISPs employing aggressive spam blocking without their users' knowledge. These groups' concern is that ISPs or technicians seeking to reduce spam-related costs may select tools which (either through error or design) also block non-spam e-mail from sites seen as "spam-friendly." [[Spam Prevention Early Warning System|SPEWS]] is a common target of these criticisms. Few object to the existence of these tools; it is their use in filtering the mail of users who are not informed of their use which draws fire.
| |
| − | | |
| − | Some see spam-blocking tools as a threat to free expression—and laws against spamming as an untoward precedent for regulation or taxation of e-mail and the Internet at large. Even though it is possible in some jurisdictions to treat some spam as unlawful merely by applying existing laws against [[trespass]] and [[conversion (law)|conversion]], some laws specifically targeting spam have been proposed. In 2004, United States passed the [[Can Spam Act of 2003]] which provided ISPs with tools to combat spam. This act allowed [[Yahoo!]] to successfully sue Eric Head, reportedly one of the biggest spammers in the world, who settled the lawsuit for several thousand U.S. dollars in June 2004. But the law is criticized by many for not being effective enough. Indeed, the law was supported by some spammers and organizations which support spamming, and opposed by many in the antispam community. Examples of effective anti-abuse laws that respect free speech rights include those in the U.S. against unsolicited faxes and phone calls, and those in Australia and a few U.S. states against spam.
| |
| − | | |
| − | In November 2004, [[Lycos Europe]] released a screensaver called [[make LOVE not SPAM]] which made [[Distributed Denial of Service]] attacks on the spammers themselves. It met with a large amount of controversy and the initiative ended in December 2004.
| |
| − | | |
| − | === Court cases ===
| |
| − | ==== United States ====
| |
| − | Attorney [[Laurence Canter]] was disbarred by the [[Supreme Court of Tennessee]] in 1997 for sending prodigious amounts of spam advertising his [[immigration law]] practice.
| |
| − | | |
| − | Robert Soloway lost a case in a federal court against the operator of a small Oklahoma-based Internet service provider who accused him of spamming. U.S. Judge Ralph G. Thompson granted a motion by plaintiff Robert Braver for a [[default judgment]] and permanent [[injunction]] against him. The judgment includes a statutory damages award of $10,075,000 under Oklahoma law.<ref>[http://www.mortgagespam.com/soloway Braver v. Newport Internet Marketing Corporation et al] - ''U.S. District Court - Western District of Oklahoma (Oklahoma City)'', 2005-[[02-22]]</ref>
| |
| − | | |
| − | In 2005, [[Jason Smathers]], a former [[America Online]] employee, pled guilty to charges of violating the CAN-SPAM ACT. In 2003, he sold a list of approximately 93 million AOL subscriber e-mail addresses to Sean Dunaway who, in turn, sold the list to spammers.<ref>U.S. v Jason Smathers and Sean Dunaway, amended complaint, US District Court for the Southern District of New York (2003). Retrieved 07 March, 2007, from http://www.thesmokinggun.com/archive/0623042aol1.html</ref><ref>Ex-AOL employee pleads guilty in spam case. (2005, February 4). CNN. Retrieved 07 March, 2007, from http://www.cnn.com/2005/TECH/internet/02/04/aol.spam.plea/</ref>
| |
| − | | |
| − | ==== United Kingdom ====
| |
| − | In the first successful case of its kind, Mr. Nigel Roberts from the [[Channel Islands]] won £270 against [[Media Logistics UK]] who sent junk e-mails to his personal account.<ref>[http://news.bbc.co.uk/1/hi/world/europe/jersey/4562726.stm Businessman wins e-mail spam case] - ''BBC News'', 2005-[[12-27]]</ref>
| |
| − | | |
| − | January 2007, the Sheriff Court in Scotland awarded Mr. Gordon Dick a £1368.66 against Transcom Internet Services Ltd.<ref>[http://www.scotchspam.co.uk/transcom.html Gordon Dick v Transcom Internet Service Ltd.]</ref> who allegedly breached anti-spam laws.<ref>[http://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=CELEX:32002L0058:EN:HTML Article 13-Unsolicited communications]</ref> It is the largest amount awarded in compensation in the United Kingdom since the Nigel Roberts case in 2005 above.
| |
| | | | |
| | + | ===Spam=== |
| | + | [[Image:spammed-mail-folder.png|thumb|300px|A KMail folder of "spam" messages]] |
| | + | "Spamming" is the abuse of electronic messaging systems to send unsolicited bulk messages, which are generally undesirable. While the most widely recognized form of spam is e-mail spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web [[search engine]] spam, spam in [[blog]]s, [[mobile phone]] messaging spam, internet forum spam, and junk [[fax machine|fax]] transmissions. Spam is also called junk mail. Some email clients or servers have spam filters, which try to delete or move the spam messages. |
| | | | |
| | + | Spamming is economically viable because [[advertising|advertisers]] have no operating costs beyond the management of their mailing lists, and it is difficult to hold senders accountable for their mass mailings. Because the [[barrier to entry]] is so low, spammers are numerous, and the volume of unsolicited mail has become very high. The costs, such as lost productivity and [[fraud]], are borne by the public and by [[Internet service provider]]s, which have been forced to add extra capacity to cope with the deluge. Spamming is widely reviled, and has been the subject of legislation in many jurisdictions. |
| | | | |
| | + | E-mail and other forms of spamming have been used for purposes other than advertisements. Many early Usenet spams were [[religion|religious]] or [[politics|political]]. A number of [[evangelism|evangelists]] have spammed Usenet and e-mail media with preaching messages. A growing number of criminals are also using spam to perpetrate various sorts of fraud (see "[[Cybercrime#Internet fraud|internet fraud]]" above) and in some cases have used it to lure people to locations where they have been [[kidnapping|kidnapped]], held for ransom, and even [[murder]]ed.<ref>Beeld Philip de Bruin, [http://www.news24.com/News24/South_Africa/News/0,,2-7-1442_1641875,00.html “SA cops, Interpol probe murder,”] News24.com (2004). Retrieved August 2, 2007.</ref> |
| | | | |
| | + | E-mail [[computer virus|worms or viruses]] may be spammed to set up an initial pool of infected machines, which resend the virus to other machines in a spam-like manner. The infected machines can often be used as remote-controlled [[zombie computers]], for more spamming, to [[phishing|phish]] for [[bank]] account details, or other attacks. |
| | | | |
| | + | Spam's direct effects include the consumption of computer and network resources, and the cost in human time and attention of dismissing unwanted messages. In addition, spam has costs stemming from the kinds of spam messages sent, from the ways spammers send them, and from the "arms race" between spammers and those who try to stop or control spam. The [[European Union]]'s Internal Market Commission estimated in 2001 that "junk e-mail" cost internet users €10 billion per year worldwide.<ref>[http://europa.eu/rapid/pressReleasesAction.do?reference=IP/01/154&format=HTML&aged=0&language=EN&guiLanguage=en "Data protection: "Junk" e-mail costs internet users 10 billion a year worldwide - Commission study."] European Commission (February 2, 2001). Retrieved July 17, 2007.</ref> In addition to direct costs are the indirect costs borne by the victims—both those related to the spamming itself, and to other crimes that usually accompany it, such as financial [[theft]], [[identity theft]], data and [[intellectual property]] theft, virus and other malware infection, child pornography, fraud, and deceptive marketing. |
| | | | |
| | + | ==Prevalence of cybercrime== |
| | + | Cybercrime has become a particularly relevant problem to [[police]] around the world and to [[society]] at large. The growing presence of the [[internet]] and [[computer]]s in homes around the world means that more people are exposed to cybercrime each year. The rise in popularity of broadband internet access also means a greater risk. In an era where all data is being digitized and stored on computers, protecting computers is integral to personal and national security. |
| | | | |
| | + | ==Preventing cybercrime== |
| | + | In order to combat cybercrime a number of precautions and preventative measures may be taken. These include the use of anti-virus software on computers, [[encryption]] of data used in online and [[credit card]] sales, and increasing public awareness of the types of scams and other attacks on computers and networks. |
| | | | |
| | ==Notes== | | ==Notes== |
| Line 909: |
Line 98: |
| | | | |
| | == References == | | == References == |
| − | | + | * Dreyfus, Suelette. ''Underground: Tales of Hacking, Madness and Obsession on the Electronic Frontier.'' Mandarin, 1997. ISBN 1863305955 |
| − | <div class="references-small">
| + | * Graham, Paul. ''Hackers and Painters.'' 2004. ISBN 0596006624 |
| − | * {{cite book | authorlink = Steven Levy | last = Levy | first = Steven | title = [[Hackers: Heroes of the Computer Revolution]] | year = 1984 | id = ISBN 0-385-19195-2 | publisher = Doubleday }} | + | * Levy, Steven. ''Hackers: Heroes of the Computer Revolution.'' Doubleday, 1984. ISBN 0385191952 |
| − | *[[Sherry Turkle|Turkle, Sherry]] (1984),''The Second Self: Computers and the Human Spirit'' , New Edition: MIT Press 2005, ISBN 0262701111 | + | * Slatalla, Michelle and Joshua Quittner. ''Masters of Deception: The Gang That Ruled Cyberspace.'' HarperCollins, 1995. ISBN 0060170301 |
| − | * {{cite book | authorlink = Bruce Sterling | last = Sterling | first = Bruce | url = http://www.mit.edu/hacker/hacker.html | title = The Hacker Crackdown | year = 1992 | id = ISBN 0-553-08058-X | publisher = Bantam }} | + | * Sterling, Bruce. [http://www.mit.edu/hacker/hacker.html ''The Hacker Crackdown.''] Bantam, 1992. ISBN 055308058X. Retrieved May 12, 2020. |
| − | * {{cite book | last = Slatalla | first = Michelle | coauthors = Joshua Quittner | title = [[Masters of Deception]]: The Gang That Ruled Cyberspace | year = 1995 | id = ISBN 0-06-017030-1 | publisher = HarperCollins }} | + | * Turkle, Sherry. ''The Second Self: Computers and the Human Spirit,'' new ed. Cambridge, MA: MIT Press, 1984. ISBN 0262701111 |
| − | * {{cite book | last = Dreyfus | first = Suelette | url = http://www.underground-book.com/ | title = Underground: Tales of Hacking, Madness and Obsession on the Electronic Frontier | year = 1997 | id = ISBN 1-86330-595-5 | publisher = Mandarin }}
| + | * Verton, Dan. ''The Hacker Diaries : Confessions of Teenage Hackers.'' McGraw-Hill Osborne Media, 2002. ISBN 0072223642 |
| − | * {{cite book | last = Verton | first = Dan | title = The Hacker Diaries : Confessions of Teenage Hackers | year = 2002 | id = ISBN 0-07-222364-2 | publisher = McGraw-Hill Osborne Media }} | |
| − | * {{cite book | autherlink = Paul Graham | last = Graham | first = Paul | title = [[Hackers and Painters]] | year = 2004 | id = ISBN 0-59-600662-4 }}
| |
| − | </div>
| |
| − | | |
| − | | |
| − | | |
| − | | |
| − | | |
| − | | |
| − | | |
| | | | |
| | ==External Links== | | ==External Links== |
| − | ==Academic resources==
| + | All links retrieved January 12, 2024. |
| − | | |
| − | *[http://cybercrimes.net/ Cybercrimes.net] and [http://steeplemedia.com/blogs/cyb3r_crim3/ Cyb3rCrim3.org] Susan W. Brenner
| |
| − | *[http://www.jisclegal.ac.uk/cybercrime/cybercrime.htm Cybercrime - High Tech crime] JISC Legal Information Service
| |
| − | *[http://www.lib.msu.edu/harris23/crimjust/cybercri.htm Criminal Justice Resources - Cybercrime]
| |
| − | *[http://information-retrieval.info/cybercrime/ Cybercrime NYLS]
| |
| − | *[http://www.cybercrimelaw.org/ Cybercrime Law]
| |
| − | | |
| − | ==Government resources==
| |
| − | | |
| − | *[http://www.cybercrime.gov/ Cybercrime.gov] US Department of Justice CCIPS
| |
| − | *[http://www.us-cert.gov/ US CERT] United States Computer Emergency Readiness Team (US-CERT)
| |
| − | *[http://www.fbi.gov/cyberinvest/cyberhome.htm FBI Cyber Investigations Home Page]
| |
| − | *[http://www.ustreas.gov/usss/financial_crimes.shtml#Computer US Secret Service Computer Fraud]
| |
| − | *[http://onguardonline.gov/index.html On Guard] OnGuardOnline.gov provides practical tips from the federal government and the technology industry to help you be on guard against Internet fraud, secure your computer, and protect your personal information.
| |
| − | *[http://www.consumer.gov/idtheft/ ID Theft] one-stop national resource to learn about the crime of identity theft
| |
| − | *[http://www.findlaw.com/01topics/10cyberspace/computercrimes/index.html FindLaw Computer Crime]
| |
| − | *[http://www.rcmp-grc.gc.ca/scams/ccprev_e.htm RCMP Computer Crime Prevention] Royal Canadian Mounted Police
| |
| − | | |
| − | ==Commercial resources==
| |
| − | | |
| − | *[http://www.e-crimecongress.org Annual e-Crime Conference] : International Conference for Public & Private Security Specialists
| |
| − | | |
| − | ==Further reading==
| |
| − | | |
| − | * [http://www.criminallawyergroup.com/criminal-defense/the-evolution-of-cybercrime-from-past-to-the-present.php The evolution of cybercrime from past to the present]
| |
| − | * [http://news.com.com/Cybercrime+and+punishment/2009-7348-6150800.html?part=dht&tag=nl.e433 CNET - Cybercrime and Punishment]
| |
| − | | |
| − | | |
| − | ==External links==
| |
| − | | |
| − | * [http://www.idfraud.org.uk All Party Parliamentary Group on Identity Fraud Website] - initiative of British parlimenatrians
| |
| − | * [http://www.privacyrights.org/identity.htm Privacy Rights Clearinghouse webpages] a non profit consumer information and advocacy organisation
| |
| − | * [http://www.ftc.gov/bcp/edu/microsites/idtheft/ U.S. (FTC.gov) website devoted to ID theft]
| |
| − | * [http://www.identitytheftinsider.com/identity-theft-risks/reduce-your-identity-theft-risk/ Identity Theft Insider] - Identity Theft from a previous victim's perspective
| |
| − | * [http://www.identitylockblog.info IdentityLockBlog.Info] - Blog tracking identity theft developments with daily news updates
| |
| − | * [http://www.identitytheftsecrets.com/videos/paypalemail3.html IdentityTheftSecrets.com] - Very clever anatomy of a phishing scheme in action
| |
| − | * [http://alabamaconsumerlawblog.com AlabamaConsumerLawBlog.com] - Blog tracking consumer law and identity theft issues
| |
| − | * [http://www.identitytheft.org.uk/ United Kingdom Home Office Identity Theft Website]
| |
| − | * [http://www.usdoj.gov/criminal/fraud/idtheft.html Identity Theft and Fraud] from the US Dept. of Justice
| |
| − | * [http://www.usdoj.gov/criminal/fraud/Internet.htm Internet Fraud] from the US Dept. of Justice
| |
| − | * [http://www.mysecurecyberspace.org/encyclopedia/index/identity-theft.html#msc.encyclopedia.identitytheft Identity Theft] — Carnegie Mellon CyLab's MySecureCyberspace, a portal on cybersecurity for home users
| |
| − | *[http://www.epic.org/privacy/consumer/states.html Privacy Laws by State]
| |
| − | * [http://www.idtheftcenter.org/index.shtml] The Identity Theft Resource Center, a nonprofit, nationally respected program dedicated exclusively to identity theft.
| |
| − | * {{cite news | first= | last= | coauthors= | title=Transcript of Attorney General Alberto R. Gonzales and FTC Chairman Deborah Platt Majoras Announcing the Release of the President's Identity Theft Task Force | date=April 23, 2007 | publisher= | url =http://www.usdoj.gov/ag/speeches/2007/ag_speech_0704231.html | work =US Department of Justice | pages = | accessdate = 2007-04-24 | language = }}
| |
| − | * [http://www.creditlock.com/identitythefttaskforce.html Identity Theft Crackdown: Strengths, Weaknesses and Red Flags For Identity Theft Task Force Strategic Plan] GammaWealth Strategy & Research, LLC
| |
| − | * [http://ezinearticles.com/?Identity-Theft---The-Time-Bomb-On-Your-Desktop&id=386274 Identity Theft - The Time Bomb On Your Desktop] Richard Odell - Computer security article
| |
| − | * [http://www.crediteria.com/CreditChat/2007/03/resources_for_protection_from.htm Worksheet to follow if you suspect you are a victim of identity theft] - Steps and resources to contact for victims of identity theft
| |
| − | | |
| − | | |
| − | | |
| − | * [http://www.usdoj.gov/criminal/fraud/Internet.htm Article about Internet Fraud from the U.S. Department of Justice]
| |
| − | * [http://www.fraud.org/internet/intinfo.htm National Consumer's League Internet Fraud Page]
| |
| − | * [http://travel.state.gov/travel/tips/brochures/brochures_1216.html Advanced Fee Business Scams] U.S. Department of State Article
| |
| − | * [http://www.sec.gov/investor/pubs/cyberfraud.htm Internet Fraud: How to Avoid Internet Investment Scams] from the US Securities and Exchange Commission
| |
| − | * [http://www.fbi.gov/majcases/fraud/internetschemes.htm FBI Overview of Internet Fraud]
| |
| − | | |
| − | | |
| − | | |
| − | * Stephanos Androutsellis-Theotokis and Diomidis Spinellis. [http://www.spinellis.gr/pubs/jrnl/2004-ACMCS-p2p/html/AS04.html A survey of peer-to-peer content distribution technologies]. ACM Computing Surveys, 36(4):335–371, December 2004. [http://dx.doi.org/10.1145/1041680.1041681 doi:10.1145/1041680.1041681].
| |
| − | * Stefan Saroiu, P. Krishna Gummadi, and Steven D. Gribble. [http://www.cs.ucsb.edu/~almeroth/classes/F02.276/papers/p2p-measure.pdf A Measurement Study of Peer-to-Peer File Sharing Systems]. Technical Report # UW-CSE-01-06-02. Department of Computer Science & Engineering. University of Washington. Seattle, WA, USA.
| |
| − | * Ralf Steinmetz, Klaus Wehrle (Eds). [http://www.peer-to-peer.info/ Peer-to-Peer Systems and Applications]. ISBN 3-540-29192-X, Lecture Notes in Computer Science, Volume 3485, Sep 2005
| |
| − | * [[Shuman Ghosemajumder|Ghosemajumder, Shuman]]. ''[http://shumans.com/p2p-business-models.pdf Advanced Peer-Based Technology Business Models]''. [[MIT Sloan School of Management]], 2002.
| |
| − | * Silverthorne, Sean. ''[http://hbswk.hbs.edu/item.jhtml?id=4206&t=innovation Music Downloads: Pirates- or Customers?]''. [[Harvard Business School|Harvard Business School Working Knowledge]], 2004.
| |
| − | * [http://www.cs.huji.ac.il/labs/danss/p2p/resources.html Selected Papers] — A collection of academic papers
| |
| − | | |
| − | | |
| − | *The [http://www.catb.org/~esr/jargon Jargon File]
| |
| − | *The [http://wikihost.org/wikis/newjargonfile/ New Jargon File]: An effort to establish an open hacker culture document, in the tradition of the [[Jargon File]]
| |
| − | *[http://www.casoabierto.com/Actualidad/Reportajes/The-Ten-Biggest-Legends-of-the-Hacker-Universe.html The Ten Biggest Legends of the Hacker Universe]
| |
| − | *[http://www.catb.org/~esr/faqs/hacker-howto.html How To Become A Hacker] by [[Eric S. Raymond]]
| |
| − | *[http://stallman.org/articles/on-hacking.html On Hacking] by [[Richard Stallman|Richard M. Stallman]]
| |
| − | *The [http://hacks.mit.edu/ MIT Gallery of Hacks]
| |
| − | | |
| − | | |
| − | | |
| − | | |
| − | *[http://www.antiphishing.org/reports/APWG_CrimewareReport.pdf US Department of Homeland Security Identity Theft Technology Council report "The Crimeware Landscape: Malware, Phishing, Identity Theft and Beyond"]
| |
| − | * [http://www.microsoft.com/emea/itsshowtime/sessionh.aspx?videoid=359 Video: Mark Russinovich - Advanced Malware Cleaning]
| |
| − | | |
| − | | |
| − | | |
| − | * RFC 4732 Internet Denial-of-Service Considerations
| |
| − | * [http://foro.elhacker.net/index.php/topic,137442.0.html Intentando detener un DDoS] (en español)
| |
| − | * [http://www.w3.org/Security/Faq/wwwsf6.html W3C The World Wide Web Security FAQ ]
| |
| − | * [http://www.cert.org/tech_tips/denial_of_service.html cert.org] CERT's Guide to DoS attacks.
| |
| − | * [http://staff.washington.edu/dittrich/misc/ddos/ washington.edu] Dave Dittrich's DDoS page.
| |
| − | * [http://www.surasoft.com/articles/ddosa.php surasoft.com] - DDoS case study, concepts, and protection.
| |
| − | * [http://www.tik.ee.ethz.ch/~ddosvax/ tik.ee.ethz.ch] DDoSVax Research Project at the [http://www.ethz.ch/ Swiss Federal Institute of Technology] in [[Zürich]].
| |
| − | * [http://www.prolexic.com/labs prolexic.com] - Prolexic Whitepaper on DDoS mitigation
| |
| − | * [http://www.honeypots.net/incidents/ddos-mitigation honeypots.net] Papers and presentations on DDoS mitigation techniques.
| |
| − | * [http://www.denialinfo.com/dos.html DoS attack resources]
| |
| − | * [http://newssocket.com/foonet/ newssocket.com] An article regarding a DDoS for hire incident.
| |
| − | * [http://www.grc.com/dos/drdos.htm grc.com] General information regarding DoS attacks.
| |
| − | * [http://www.isotf.org/news/DNS-Amplification-Attacks.pdf isotf.org] General information regarding DNS reflector and amplification DDoS attacks.
| |
| − | * [http://www.linuxsecurity.com/content/view/121960/49/ linuxsecurity.com] An article on preventing DDoS attacks.
| |
| − | * [http://www.intruguarddevices.com/resources_dosarticles.html intruguarddevices.com] News articles on DDoS attacks.
| |
| − | * [http://whatis.techtarget.com/definition/0,289893,sid9_gci213591,00.html whatis.com – Denial of Service]
| |
| − | * [http://www.cert.org/tech_tips/denial_of_service.html Denial of Service] (Carnegie Mellon) CC Denial of Service Attacks
| |
| − | * [http://www.us-cert.gov/cas/tips/ST04-015.html Understanding Denial of Service Attack. US-CERT]
| |
| − | * [http://www.geocities.com/nonlinearphysics/cisco_ios_qos.html Cisco IOS commands to prevent flooding.]
| |
| − | * [http://frankgerlach.blogspot.com A proposal for defeating SYN attacks by a protocol change]
| |
| − | * [http://matthewhutchinson.net/files/Final_Report.pdf (Queens University Belfast) Denial of Service Study]
| |
| − | * [http://www.ddosinfo.com DDoSInfo.com Blog About The Latest DDoS Incidents]
| |
| − | | |
| − | | |
| − | * [http://www.spamtrackers.eu/wiki Spamtrackers SpamWiki]: a peer-reviewed spam information and analysis resource.
| |
| − | * [http://www.ftc.gov/spam/ Federal Trade Commission page advising people to forward spam e-mail to them]
| |
| − | * [http://www.ftc.gov/bcp/conline/pubs/alerts/spamalrt.htm ''E-mail Address Harvesting: How Spammers Reap What You Sow''] by the Federal Trade Commission
| |
| − | * [http://www.uic.edu/depts/accc/newsletter/adn29/spam.html Slamming Spamming Resource on Spam]
| |
| − | * [http://www.cdt.org/speech/spam/030319spamreport.shtml Why am I getting all this spam? CDT]
| |
| − | * [http://www.cybertelecom.org/spam/ Cybertelecom :: Federal SPAM law and policy]
| |
| − | | |
| − | | |
| − | | |
| | | | |
| | + | * [https://www.justice.gov/criminal-ccips Computer Crime and Intellectual Property Section (CCIPS)] – U.S. Department of Justice |
| | + | * [http://www.ftc.gov/bcp/edu/microsites/idtheft/ Identity Theft] – Federal Trade Commission |
| | + | * [http://www.onguardonline.gov/ On Guard] – OnGuardOnline.gov provides practical tips from the federal government and the technology industry to help you be on guard against Internet fraud, secure your computer, and protect your personal information |
| | | | |
| | {{Credits|Cybercrime|131362470|Identity_theft|133371583|Internet_fraud|133383415|File_sharing|134479220|Hacker|134774806|Malware|133592383|Denial-of-service_attack|133240660|Spam_(electronic)|134818290|}} | | {{Credits|Cybercrime|131362470|Identity_theft|133371583|Internet_fraud|133383415|File_sharing|134479220|Hacker|134774806|Malware|133592383|Denial-of-service_attack|133240660|Spam_(electronic)|134818290|}} |