|
|
| Line 3: |
Line 3: |
| | [[Category:Law]] | | [[Category:Law]] |
| | | | |
| − | | + | '''Cybercrime''' is a term used broadly to describe activity in which [[computers]] or [[computer network|networks]] are a tool, a target, or a place of criminal activity. These categories are not exclusive and many activities can be characterized as falling in one or more categories. Cybercrime takes a number of forms including identity theft, internet fraud, violation of copyright laws through file sharing, hacking, computer viruses, denial of service attacks, and spam. |
| − | '''Cybercrime''' is a term used broadly to describe activity in which [[computers]] or [[computer network|networks]] are a tool, a target, or a place of criminal activity. These categories are not exclusive and many activities can be characterized as falling in one or more categories. | |
| | | | |
| | ==Overview== | | ==Overview== |
| | Although the term cybercrime is usually restricted to describing criminal activity in which the computer or network is an essential part of the crime, this term is also used to include traditional crimes in which computers or networks are used to enable the illicit activity. | | Although the term cybercrime is usually restricted to describing criminal activity in which the computer or network is an essential part of the crime, this term is also used to include traditional crimes in which computers or networks are used to enable the illicit activity. |
| | | | |
| − | :Examples of cybercrime in which the computer or network is a tool of the criminal activity include [[spamming]] and certain [[intellectual property]] and criminal [[copyright]] crimes, particularly those facilitated through [[peer-to-peer]] networks.
| + | Examples of cybercrime in which the computer or network is a tool of the criminal activity include [[spamming]] and certain [[intellectual property]] and criminal [[copyright]] crimes, particularly those facilitated through [[peer-to-peer]] networks. |
| | | | |
| − | :Examples of cybercrime in which the computer or network is a target of criminal activity include unauthorized access (i.e, defeating [[access control]]s), [[malware|malicious code]], and [[denial-of-service]] attacks.
| + | Examples of cybercrime in which the computer or network is a target of criminal activity include unauthorized access (i.e, defeating [[access control]]s), [[malware|malicious code]], and [[denial-of-service]] attacks. |
| | | | |
| − | :Examples of cybercrime in which the computer or network is a place of criminal activity include theft of service (in particular, [[phreaking|telecom fraud]]) and certain financial frauds.
| + | Examples of cybercrime in which the computer or network is a place of criminal activity include theft of service (in particular, [[phreaking|telecom fraud]]) and certain financial frauds. |
| | | | |
| − | :Finally, examples of traditional crimes facilitated through the use of computers or networks include [[Advance fee fraud|Nigerian 419]] or other gullibility or [[social engineering]] frauds (e.g., "[[phishing]]"), [[identity theft]], [[child pornography]], [[online gambling]], [[securities fraud]], etc. [[Cyberstalking]] is an example of a traditional crime — harassment — that has taken a new form when facilitated through computer networks.
| + | Finally, examples of traditional crimes facilitated through the use of computers or networks include [[Advance fee fraud|Nigerian 419]] or other gullibility or [[social engineering]] frauds (e.g., "[[phishing]]"), [[identity theft]], [[child pornography]], [[online gambling]], [[securities fraud]], etc. [[Cyberstalking]] is an example of a traditional crime — harassment — that has taken a new form when facilitated through computer networks. |
| | | | |
| | Additionally, certain other information crimes, including [[trade secret]] theft and [[Industrial espionage|industrial]] or [[Economic Espionage Act of 1996|economic]] espionage, are sometimes considered cybercrimes when computers or networks are involved. | | Additionally, certain other information crimes, including [[trade secret]] theft and [[Industrial espionage|industrial]] or [[Economic Espionage Act of 1996|economic]] espionage, are sometimes considered cybercrimes when computers or networks are involved. |
| Line 23: |
Line 22: |
| | Another way to define cybercrime is simply as criminal activity involving the information technology infrastructure, including illegal access (unauthorized access), illegal interception (by technical means of non-public transmissions of computer data to, from or within a computer system), data interference (unauthorized damaging, deletion, deterioration, alteration or suppression of computer data), systems interference (interfering with the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering or suppressing computer data), misuse of devices, forgery (ID theft), and electronic fraud. | | Another way to define cybercrime is simply as criminal activity involving the information technology infrastructure, including illegal access (unauthorized access), illegal interception (by technical means of non-public transmissions of computer data to, from or within a computer system), data interference (unauthorized damaging, deletion, deterioration, alteration or suppression of computer data), systems interference (interfering with the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering or suppressing computer data), misuse of devices, forgery (ID theft), and electronic fraud. |
| | | | |
| | + | ==Types== |
| | + | ===Child Pornography=== |
| | + | The issue of child pornography has become more important due to its widespread distribution and availability on the internet. Child pornography is widely seen as a form of child abuse and its production, distribution, and possession is outlawed in most countries. Prohibition may include images or videos of children engaged in sexual acts or of nude children. Many American states have made efforts to pass legislation outlawing its transmission via the internet. |
| | | | |
| − | | + | ===Computer Viruses and other Malware=== |
| − | ==Identity theft== | |
| − | With the rising awareness of consumers to an international problem, in particular through a proliferation of web sites and the media, the term "identity theft" has morphed to encompass a broad range of identification-based crimes. The more traditional crimes range from dead beat dads avoiding their financial obligations, to providing the police with stolen or forged documents thereby avoiding detection, money laundering, trafficking in human beings, stock market manipulation and even to terrorism.
| |
| − | | |
| − | According to the non-profit [http://www.idtheftcenter.org/cresources.shtml Identity Theft Resource Center], identity theft is "sub-divided into four categories: Financial Identity Theft (using another's name and SSN to obtain goods and services), Criminal Identity Theft (posing as another when apprehended for a crime), Identity Cloning (using another's information to assume his or her identity in daily life) and Business/Commercial Identity Theft (using another's business name to obtain credit)." There are a number of methods used by identity thieves including stealing mail or rummaging through rubbish ([[dumpster diving]]), eavesdropping on public transactions to obtain personal data ([[Shoulder surfing (computer security)|shoulder surfing]]), stealing personal information in computer databases [Trojan horses, hacking], [[infiltration]] of organizations that store large amounts of personal information, impersonating a trusted organization in an electronic communication ([[phishing]]), the use of [[spam (electronic)]]: Some, if not all spam requires you to respond to alleged contests, enter into "Good Deals," etc., and using another arguably illegal reason to victimize individuals who display their personal information in [[good faith]], such as landlord-related fraud, where the [[Patriot Act]] is used to create suspicion on prospective tenants, and then using their personal information to commit fraud. This is a very common practice among [[landlord|slumlords]], who violate [[civil rights]] and use the right to request [[background checks]] to defend their legal policies, which are later used to commit crimes; the laws themselves create this conflict and is a type of identity theft created and enforced by [[federal law]].
| |
| − | | |
| − | The unlawful acquisition of legally attributed personal identifiers is made possible by serious breaches of [[privacy]]. For consumers it is usually due to personal naivete in who they provide their information to or carelessness in protecting their information from theft (e.g. vehicle break-ins and home invasions). Surveys in the USA from 2003 to 2006 showed a decrease in the total number of victims but an increase in the total value of identity fraud to US$56.6 billion in 2006. The average fraud per person rose from $5,249 in 2003 to $6,383 in 2006.<ref>[http://www.privacyrights.org/ar/idtheftsurveys.htm Recent Surveys and Studies], Privacy Clearing House, retrieved June 30,2006</ref> In the United Kingdom the Home Office reported that identity fraud costs the UK economy £1.7 billion<ref>[http://www.identitytheft.org.uk/ What is Identity theft?],[[Home Office]],retrieved June 30,2006</ref> although privacy groups object to the validity of these numbers, arguing that they are being used by the government to push for introduction of national ID cards. Confusion over exactly what constitutes identity theft has led to claims that statistics may be exaggerated.<ref> [http://www.schneier.com/blog/archives/2005/11/identity_theft.html Identity Theft Over-Reported],[[Bruce Schneier]], retrieved June 30,2006</ref>
| |
| − | | |
| − | ==Internet fraud==
| |
| − | The term "'''Internet fraud'''" generally refers to any type of fraud scheme that uses one or more online services - such as chat rooms, e-mail, message boards, or Web sites - to present fraudulent solicitations to prospective victims, to conduct fraudulent transactions, or to transmit the proceeds of fraud to financial institutions or to others connected with the scheme.
| |
| − | | |
| − | Internet fraud is committed in several ways. The [[FBI]] and police agencies worldwide have people assigned to combat this type of [[fraud]]; according to figures from the FBI, U.S. companies' losses due to Internet fraud in 2003 surpassed [[US dollar|US$]]500 million. In some cases, [[fictitious]] merchants advertise goods for very low prices and never deliver. However, that type of fraud is minuscule compared to [[Crime|criminal]]s using stolen [[credit card]] information to buy goods and services.
| |
| − | | |
| − | Some common types of internet fraud include identity theft, purchase scams, counterfeit money orders, 'phishing' for sensitive information, and clickfraud whereby false hits are generated for websites in order to generate advertising money.
| |
| − | | |
| − | ==File sharing==
| |
| − | '''File sharing''' is the practice of making [[computer file|file]]s available for other users to download over the [[Internet]] and smaller [[computer network|networks]]. Usually file sharing follows the [[peer-to-peer]] (P2P) model, where the files are stored on and served by personal computers of the users. Most people who engage in file sharing are also downloading files that other users share. Sometimes these two activities are linked together. P2P file sharing is distinct from file trading in that downloading files from a P2P network does not require uploading, although some networks either provide incentives for uploading such as credits or force the sharing of files being currently downloaded.
| |
| − | | |
| − | Under US law "the Betamax decision" ([[Sony Corp. of America v. Universal City Studios, Inc.]]), case holds that copying "technologies" are not ''inherently'' illegal, if substantial non-infringing use can be made of them. This decision, predating the widespread use of the [[Internet]] applies to most data networks, including peer-to-peer networks, since distribution of correctly licensed files can be performed. These non-infringing uses include sending open source software, public domain files and out of copyright works. Other jurisdictions tend to view the situation in somewhat similar ways.
| |
| − | | |
| − | In practice, many of the files shared on peer-to-peer networks are copies of copyrighted popular music and movies. Sharing of these copies among strangers is illegal in most jurisdictions. This has led many observers, including most media companies and some peer-to-peer critics, to conclude that the networks themselves pose grave threats to the established distribution model. The research that attempts to measure actual monetary loss has been somewhat equivocal. Whilst on paper the existence of these networks results in large losses, the actual income does not seem to have changed much since these networks started up. Whether the threat is real or not, both the [[Recording Industry Association of America|RIAA]] and the [[Motion Picture Association of America|MPAA]] now spend large amounts of money attempting to lobby lawmakers for the creation of new laws, and some copyright owners pay companies to help legally challenge users engaging in illegal sharing of their material.
| |
| − | | |
| − | ==Hacking==
| |
| − | A '''hacker''' is someone who who gains illegal access to computers. This action can be done maliciously or with the intent of pointing out possible security risks. Microsoft and the Department of Defense are among those large organizations that have been the target of hackers. Hacking poses a risk to society as hackers can gain access to sensitive financial, personal, or security information that can then be used for [[extortion]] or exploited for an attack.
| |
| − | | |
| − | The term is also often applied to [[computer software]] or [[computer hardware]] [[programmer]]s, designers and administrators, especially those who are perceived as experts or highly accomplished in this field. A hacker is also a term used for someone who modifies electronics such as ham radio transceivers, printers or even home sprinkler systems for better functionality or performance. The term usually bears strong connotations that may be favorable or pejorative depending on cultural context (see the [[hacker definition controversy]]).
| |
| − | | |
| − | ==Computer Viruses and other Malware== | |
| | '''Malware''' is software designed to infiltrate or damage a computer system without the owner's [[informed consent]]. It is a [[portmanteau]] of the words "[[Malice (legal term)|malicious]]" and "[[Computer software|software]]." The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code. Many normal computer users are however still unfamiliar with the term, and most never use it. Instead, "(computer) [[computer virus|virus]]" is used in common parlance and often in the general media to describe all kinds of malware. Another term that has been recently coined for malware is badware, perhaps due to the anti-malware initiative [[Stopbadware]] or corruption of the term "malware." Software is considered malware based on the perceived intent of the creator rather than any particular features. It includes computer viruses, [[Computer worm|worms]], [[Trojan horse (computing)|trojan horse]]s, [[spyware]], dishonest [[adware]], and other malicious and unwanted software. In [[law]], malware is sometimes known as a computer contaminant, for instance in the legal codes of [[California]], [[West Virginia]], and several other [[United States|U.S.]] states.<ref>[http://www.ncsl.org/programs/lis/cip/viruslaws.htm Virus/Contaminant/Destructive Transmission Statutes] National Conference of State Legislatures. Retrieved May 31, 2007.</ref> | | '''Malware''' is software designed to infiltrate or damage a computer system without the owner's [[informed consent]]. It is a [[portmanteau]] of the words "[[Malice (legal term)|malicious]]" and "[[Computer software|software]]." The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code. Many normal computer users are however still unfamiliar with the term, and most never use it. Instead, "(computer) [[computer virus|virus]]" is used in common parlance and often in the general media to describe all kinds of malware. Another term that has been recently coined for malware is badware, perhaps due to the anti-malware initiative [[Stopbadware]] or corruption of the term "malware." Software is considered malware based on the perceived intent of the creator rather than any particular features. It includes computer viruses, [[Computer worm|worms]], [[Trojan horse (computing)|trojan horse]]s, [[spyware]], dishonest [[adware]], and other malicious and unwanted software. In [[law]], malware is sometimes known as a computer contaminant, for instance in the legal codes of [[California]], [[West Virginia]], and several other [[United States|U.S.]] states.<ref>[http://www.ncsl.org/programs/lis/cip/viruslaws.htm Virus/Contaminant/Destructive Transmission Statutes] National Conference of State Legislatures. Retrieved May 31, 2007.</ref> |
| | | | |
| Line 58: |
Line 33: |
| | Another strictly for-profit category of malware has emerged in [[spyware]] — programs designed to monitor users' web browsing, display unsolicited advertisements, or redirect [[affiliate marketing]] revenues to the spyware creator. Spyware programs do not spread like viruses; they are generally installed by exploiting security holes or are packaged with user-installed software. | | Another strictly for-profit category of malware has emerged in [[spyware]] — programs designed to monitor users' web browsing, display unsolicited advertisements, or redirect [[affiliate marketing]] revenues to the spyware creator. Spyware programs do not spread like viruses; they are generally installed by exploiting security holes or are packaged with user-installed software. |
| | | | |
| − | ==Denial of service attacks== | + | ===Denial of service attacks=== |
| − | In [[computer security]] and [[computer crime|crime]], a '''denial-of-service attack''' ('''DoS attack''') is an attempt to make a computer resource unavailable to its intended users. Although the means to, motives for and targets of a DoS attack may vary, it generally comprises the concerted, malevolent efforts of a person or persons to prevent an [[Internet]] [[Website|site]] or [[Web service|service]] from functioning efficiently or at all, temporarily or indefinitely. | + | In [[computer security]] and [[computer crime|crime]], a '''denial-of-service attack''' ('''DoS attack''') is an attempt to make a computer resource unavailable to its intended users. Although the means to, motives for and targets of a DoS attack may vary, it generally comprises the concerted, malevolent efforts of a person or persons to prevent an [[Internet]] [[Website|site]] or [[Web service|service]] from functioning efficiently or at all, temporarily or indefinitely. Perpetrators of DoS attacks typically — but not exclusively — target sites or services hosted on high-profile web servers. |
| − | | |
| − | Perpetrators of DoS attacks typically — but not exclusively — target sites or services hosted on high-profile web servers; a pair of [[DNS Backbone DDoS Attacks]], on October 22, 2002 and February 6, 2007, targeted [[DNS root servers]], in an apparent attempt to disable the Internet itself. | |
| | | | |
| | One common method of attack involves saturating the target (victim) machine with external communications requests, such that it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable. In general terms, DoS attacks are implemented by: | | One common method of attack involves saturating the target (victim) machine with external communications requests, such that it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable. In general terms, DoS attacks are implemented by: |
| Line 67: |
Line 40: |
| | * obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately. | | * obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately. |
| | | | |
| − | Denial-of-service attacks are considered violations of the [[Internet Architecture Board|IAB]]'s [[Internet ethics|Internet proper use policy]]. They also commonly constitute violations of the [[Computer crime#Applicable laws|laws of individual nations]].
| + | The easiest way to survive an attack is to have planned for the attack. Having a separate emergency block of IP addresses for critical servers with a separate route can be invaluable. A separate route (perhaps a DSL) is not that extravagant, and it can be used for load balancing or sharing under normal circumstances and switched to emergency mode in the event of an attack. Other preventative measures include firewalls, SYN cookies, switches, and routers. |
| | | | |
| − | === Manifestions ===
| + | Denial of service attacks are one form of computer [[sabotage]] whereby people can effectively ruin their target's operations for what could be a lengthy period of time. |
| | | | |
| − | The [[United States Computer Emergency Readiness Team]] defines symptoms of DoS attacks to include:
| + | ===File sharing=== |
| | + | '''File sharing''' is the practice of making [[computer file|file]]s available for other users to download over the [[Internet]] and smaller [[computer network|networks]]. Usually file sharing follows the [[peer-to-peer]] (P2P) model, where the files are stored on and served by personal computers of the users. Most people who engage in file sharing are also downloading files that other users share. Sometimes these two activities are linked together. P2P file sharing is distinct from file trading in that downloading files from a P2P network does not require uploading, although some networks either provide incentives for uploading such as credits or force the sharing of files being currently downloaded. |
| | | | |
| − | * unusually slow network performance (opening files or accessing web sites)
| + | Under US law "the Betamax decision" ([[Sony Corp. of America v. Universal City Studios, Inc.]]), case holds that copying "technologies" are not ''inherently'' illegal, if substantial non-infringing use can be made of them. This decision, predating the widespread use of the [[Internet]] applies to most data networks, including peer-to-peer networks, since distribution of correctly licensed files can be performed. These non-infringing uses include sending open source software, public domain files and out of copyright works. Other jurisdictions tend to view the situation in somewhat similar ways. |
| − | * unavailability of a particular web site
| |
| − | * inability to access any web site
| |
| − | * dramatic increase in the number of spam emails received[http://www.us-cert.gov/cas/tips/ST04-015.html]
| |
| | | | |
| − | Not all service outages, even those that result from malicious activity, are necessarily denial-of-service attacks. Other methods of attack may include a denial of service as one component of a larger offensive.
| + | In practice, many of the files shared on peer-to-peer networks are copies of copyrighted popular music and movies. Sharing of these copies among strangers is illegal in most jurisdictions. This has led many observers, including most media companies and some peer-to-peer critics, to conclude that the networks themselves pose grave threats to the established distribution model. The research that attempts to measure actual monetary loss has been somewhat equivocal. Whilst on paper the existence of these networks results in large losses, the actual income does not seem to have changed much since these networks started up. Whether the threat is real or not, both the [[Recording Industry Association of America|RIAA]] and the [[Motion Picture Association of America|MPAA]] now spend large amounts of money attempting to lobby lawmakers for the creation of new laws, and some copyright owners pay companies to help legally challenge users engaging in illegal sharing of their material. |
| | | | |
| − | DoS attacks can also lead to problems in the network 'branches' around the actual computer being attacked. For example, the bandwidth of a router between the Internet and a [[Local Area Network|LAN]] may be consumed by a DoS, compromising not only the intended computer, but also the entire network.
| + | ===Hacking=== |
| | + | A '''hacker''' is someone who who gains illegal access to computers. This action can be done maliciously or with the intent of pointing out possible security risks. Microsoft and the Department of Defense are among those large organizations that have been the target of hackers. Hacking poses a risk to society as hackers can gain access to sensitive financial, personal, or security information that can then be used for [[extortion]] or exploited for an attack. |
| | | | |
| − | If the DoS is conducted on a sufficiently large scale, entire geographical swathes of Internet connectivity can also be compromised by incorrectly configured or flimsy network infrastructure equipment without the attacker's knowledge or intent.
| + | The term is also often applied to [[computer software]] or [[computer hardware]] [[programmer]]s, designers and administrators, especially those who are perceived as experts or highly accomplished in this field. A hacker is also a term used for someone who modifies electronics such as ham radio transceivers, printers or even home sprinkler systems for better functionality or performance. The term usually bears strong connotations that may be favorable or pejorative depending on cultural context (see the [[hacker definition controversy]]). |
| | | | |
| − | === Methods of attack === | + | ===Identity theft=== |
| − | A "denial-of-service" attack is characterized by an explicit attempt by attackers to prevent legitimate users of a service from using that service. Examples include:
| + | With the rising awareness of consumers to an international problem, in particular through a proliferation of web sites and the media, the term "identity theft" has morphed to encompass a broad range of identification-based crimes. The more traditional crimes range from dead beat dads avoiding their financial obligations, to providing the police with stolen or forged documents thereby avoiding detection, money laundering, trafficking in human beings, stock market manipulation and even to terrorism. |
| | | | |
| − | * flooding a network, thereby preventing legitimate network traffic;
| + | According to the non-profit [http://www.idtheftcenter.org/cresources.shtml Identity Theft Resource Center], identity theft is "sub-divided into four categories: Financial Identity Theft (using another's name and SSN to obtain goods and services), Criminal Identity Theft (posing as another when apprehended for a crime), Identity Cloning (using another's information to assume his or her identity in daily life) and Business/Commercial Identity Theft (using another's business name to obtain credit)." There are a number of methods used by identity thieves including stealing mail or rummaging through rubbish ([[dumpster diving]]), eavesdropping on public transactions to obtain personal data ([[Shoulder surfing (computer security)|shoulder surfing]]), stealing personal information in computer databases [Trojan horses, hacking], [[infiltration]] of organizations that store large amounts of personal information, impersonating a trusted organization in an electronic communication ([[phishing]]), the use of [[spam (electronic)]]: Some, if not all spam requires you to respond to alleged contests, enter into "Good Deals," etc., and using another arguably illegal reason to victimize individuals who display their personal information in [[good faith]], such as landlord-related fraud, where the [[Patriot Act]] is used to create suspicion on prospective tenants, and then using their personal information to commit fraud. This is a very common practice among [[landlord|slumlords]], who violate [[civil rights]] and use the right to request [[background checks]] to defend their legal policies, which are later used to commit crimes; the laws themselves create this conflict and is a type of identity theft created and enforced by [[federal law]]. |
| − | * disrupting a server by sending more requests than it can possibly handle, thereby preventing access to a service;
| |
| − | * preventing a particular individual from accessing a service;
| |
| − | * disrupting service to a specific system or person.
| |
| | | | |
| − | Attacks can be directed at any network device, including attacks on [[routing]] devices and [[World Wide Web|Web]], [[electronic mail]], or [[Domain Name System]] [[Server (computing)|server]]s.
| + | The unlawful acquisition of legally attributed personal identifiers is made possible by serious breaches of [[privacy]]. For consumers it is usually due to personal naivete in who they provide their information to or carelessness in protecting their information from theft (e.g. vehicle break-ins and home invasions). Surveys in the USA from 2003 to 2006 showed a decrease in the total number of victims but an increase in the total value of identity fraud to US$56.6 billion in 2006. The average fraud per person rose from $5,249 in 2003 to $6,383 in 2006.<ref>[http://www.privacyrights.org/ar/idtheftsurveys.htm Recent Surveys and Studies], Privacy Clearing House, retrieved June 30,2006</ref> In the United Kingdom the Home Office reported that identity fraud costs the UK economy £1.7 billion<ref>[http://www.identitytheft.org.uk/ What is Identity theft?],[[Home Office]],retrieved June 30,2006</ref> although privacy groups object to the validity of these numbers, arguing that they are being used by the government to push for introduction of national ID cards. Confusion over exactly what constitutes identity theft has led to claims that statistics may be exaggerated.<ref> [http://www.schneier.com/blog/archives/2005/11/identity_theft.html Identity Theft Over-Reported],[[Bruce Schneier]], retrieved June 30,2006</ref> |
| | | | |
| − | A DoS attack can be perpetrated in a number of ways. There are three basic types of attack:
| + | ===Internet fraud=== |
| − | # consumption of computational resources, such as bandwidth, disk space, or [[Central processing unit|CPU]] time;
| + | The term "'''Internet fraud'''" generally refers to any type of fraud scheme that uses one or more online services - such as chat rooms, e-mail, message boards, or Web sites - to present fraudulent solicitations to prospective victims, to conduct fraudulent transactions, or to transmit the proceeds of fraud to financial institutions or to others connected with the scheme. |
| − | # disruption of configuration information, such as [[routing]] information;
| |
| − | # disruption of physical network components.
| |
| | | | |
| − | A DoS attack may include execution of [[malware]] intended to:
| + | Internet fraud is committed in several ways. The [[FBI]] and police agencies worldwide have people assigned to combat this type of [[fraud]]; according to figures from the FBI, U.S. companies' losses due to Internet fraud in 2003 surpassed [[US dollar|US$]]500 million. In some cases, [[fictitious]] merchants advertise goods for very low prices and never deliver. However, that type of fraud is minuscule compared to [[Crime|criminal]]s using stolen [[credit card]] information to buy goods and services. |
| − | * max out the [[CPU]]'s usage, preventing any work from occurring;
| |
| − | * trigger errors in the microcode of the machine;
| |
| − | * trigger errors in the sequencing of instructions, so as to force the computer into an unstable state or lock-up;
| |
| − | * exploits errors in the operating system to cause [[resource starvation]] and/or [[thrash (computer science)|thrashing]], i.e. to use up all available facilities so no real work can be accomplished;
| |
| − | * crash the operating system itself.
| |
| − | | |
| − | Malware commonly employed in such attacks includes [[Stacheldraht]]{{Fact|date=February 2007}}, [[Tribe Flood Network]]{{Fact|date=February 2007}} and [[Trinoo]]{{Fact|date=February 2007}}.
| |
| − | | |
| − | ====SYN floods====
| |
| | | | |
| − | A [[SYN flood]] sends a flood of [[SYN (TCP)|TCP/SYN]] packets, often with a spoofed sender address. Each of these packets are handled like a connection request, causing the server to spawn a [[half-open connection]], by sending back a TCP/SYN-ACK packet, and waiting for a [[ACK (TCP)|TCP/ACK]] packet in response from the sender address. However, because the sender address is forged, the response never comes. These half-open connections consume resources on the server and limit the number of connections the server is able to make, reducing the server's ability to respond to legitimate requests until after the attack ends.
| + | Some common types of internet fraud include identity theft, purchase scams, counterfeit money orders, 'phishing' for sensitive information, and clickfraud whereby false hits are generated for websites in order to generate advertising money. Some fraudsters approach merchants asking them for large quotes. After they quickly accept the merchant's quote, they ask for wire transfer information to send payment. Immediately, they use online check issuing systems as Qchex that require nothing but a working email, to produce checks that they use to pay other merchants or simply send associates to cash them. |
| | | | |
| − | When a computer wants to make a TCP/IP connection (the most common internet connection) to another computer, usually a server, an exchange of TCP/SYN and TCP/ACK packets of information occur. The computer requesting the connection, usually the client's or user's computer, sends a TCP/SYN packet which asks the server if it can connect. If the server will allow connections, it sends a TCP/SYN-ACK packet back to the client to say "Yes, you may connect." and reserves a space for the connection, waiting for the client to respond with a TCP/ACK packet detailing the specifics of its connection.
| + | ===Spam=== |
| − | | |
| − | In a SYN flood the address of the client is often forged so that when the server sends the go-ahead back to the client, the message is never received because the client either doesn't exist or wasn't expecting the packet and subsequently ignores it. This leaves the server with a dead connection, reserved for a client that will never respond. Usually this is done to one server many times in order to reserve all the connections for unresolved clients, which keeps legitimate clients from making connections.
| |
| − | | |
| − | The classic "bad" example is that of a party. Only 50 people can be invited to a party, and invitations are available on a first-come first-serve basis. Fifty letters are sent to request invitations, but the letters all have false return addresses. The invitations are mailed to the return addresses of the request letters. Unfortunately, all of the return addresses provided were fake, so nobody, or at least nobody of interest, receives the invitations. Now, when someone actually wants to come to the party (view the website), there are no invitations left because all the invitations (connections) have been reserved for 50 supposed people who will never actually show up.
| |
| − | | |
| − | The classic SYN flood was most notably introduced in 1993 by members of the IRC community as a method of removing combatants from IRC channels or networks. The first UNIX programs to utilize these programs were synflood.c by osek (circa 1993) and nuke.c Satanic Mechanic (circa 1992/1993)
| |
| − | | |
| − | ====LAND attack==== | |
| − | | |
| − | A [[LAND|LAND attack]] involves sending a [[Spoofing attack|spoof]]ed [[SYN (TCP)|TCP/SYN]] packet (connection initiation) with the target host's [[IP address]] with an open port as both source and destination. The attack causes the targeted machine to reply to itself continuously and eventually crash.
| |
| − | | |
| − | ====ICMP floods====
| |
| − | {{see also|smurf attack|ping flood|ping of death}}
| |
| − | A [[smurf attack]] is one particular variant of a flooding DoS attack on the public Internet. It relies on mis-configured network devices that allow packets to be sent to all computer hosts on a particular network via the [[broadcast address]] of the network, rather than a specific machine. The network then serves as a [[smurf amplifier]]. In such an attack, the perpetrators will send large numbers of [[Internet Protocol|IP]] packets with the source address faked to appear to be the address of the victim. To combat Denial of Service attacks on the Internet, services like the [[Smurf Amplifier Registry]] have given [[network service provider]]s the ability to identify misconfigured networks and to take appropriate action such as [[Network layer firewall|filtering]].
| |
| − | | |
| − | [[Ping flood]] is based on sending the victim an overwhelming number of [[ping]] packets, usually using the "ping -f" command. It is very simple to launch, the primary requirement being access to greater [[bandwidth]] than the victim.
| |
| − | | |
| − | ====UDP floods====
| |
| − | UDP floods include "[[Fraggle attack]]s." In a '''fraggle attack''' an attacker sends a large amount of [[User Datagram Protocol|UDP]] echo traffic to IP [[broadcast address]]es, all of it having a fake source address. It is a simple rewrite of the [[smurf attack]] code.
| |
| − | | |
| − | ====Teardrop attack====
| |
| − | The '''Teardrop attack''' involves sending [[Internet Protocol|IP]] fragments with overlapping oversized payloads to the target machine. A bug in the [[TCP/IP]] [[IPv4#Fragmentation and reassembly|fragmentation re-assembly]] code caused the fragments to be improperly handled, crashing the operating system as a result of this.[http://www.cert.org/advisories/CA-1997-28.html]
| |
| − | [[Windows 3.1x]], [[Windows 95]] and [[Windows NT]] operating systems, as well as versions of [[Linux]] prior to 2.0.32 and 2.1.63 are vulnerable to this attack.
| |
| − | | |
| − | ====Peer-to-peer attacks====
| |
| − | | |
| − | Attackers have found a way to exploit a number of bugs in peer-to-peer servers to initiate DDoS attacks. The most aggressive of these peer-to-peer-DDoS attacks exploits [[DC++]]. Peer-to-peer attacks are different from regular botnet based attacks. With peer-to-peer there is no botnet and the attacker doesn’t have to communicate with the clients it subverts. Instead, the attacker acts as a ‘puppet master,’ instructing clients of large peer-to-peer file sharing hubs to disconnect from their peer-to-peer network and to connect to the victim’s website instead. As a result, several thousand computers may aggressively try to connect to a target website. While a typical web server can handle a few hundred connections/sec before performance begins to degrade, most web servers fail almost instantly under five or six thousand connections/sec. With a moderately big peer-to-peer attack a site could potentially be hit with up to 750,000 connections in a short order. The targetted web server will be plugged up and confused by the incoming connections. While peer-to-peer attacks are easy to identify with signatures, the large number of IP addresses that need to be blocked (often over 250,000 during the course of a big attack) means that this type of attack can overwhelm mitigation defenses. Even if a mitigation device can keep blocking IP addresses, there are other problems to consider. For instance, there is a brief moment where the connection is opened on the server side before the signature itself comes through. Only once the connection is opened to the server can the identifying signature be sent and detected, and the connection torn down. Even tearing down connections rapidly takes server resources and can harm the server <ref>{{cite web|url=http://www.prolexic.com/news/20070514-alert.php|title=P2P Distributed Denial of Service Attack Alert|author=Sop, Paul|year=2007}}</ref>.
| |
| − | | |
| − | ====Application level floods====
| |
| − | On [[Internet Relay Chat|IRC]], [[IRC floods]] are a common electronic warfare weapon.
| |
| − | | |
| − | Various DoS-causing [[Exploit (computer security)|exploits]] such as '''[[buffer overflow]]''' can cause server-running software to get confused and fill the disk space or consume all available memory or CPU time.
| |
| − | | |
| − | Other kinds of DoS rely primarily on brute force, flooding the target with an overwhelming flux of packets, oversaturating its connection bandwidth or depleting the target's system resources. Bandwidth-saturating floods rely on the attacker having higher bandwidth available than the victim; a common way of achieving this today is via '''Distributed Denial of Service''', employing a [[botnet]]. Other floods may use specific packet types or connection requests to saturate finite resources by, for example, occupying the maximum number of open connections or filling the victim's disk space with logs.
| |
| − | | |
| − | A "banana attack" is another particular type of DoS. It involves redirecting outgoing messages from the client back onto the client, preventing outside access, as well as flooding the client with the sent packets.
| |
| − | | |
| − | An attacker with access to a victim's computer may slow it until it is unusable or crash it by using a [[fork bomb]].
| |
| − | | |
| − | A 'Pulsing zombie' is a term referring to a special denial-of-service attack. A [[Computer networking|network]] is subjected to hostile [[ping]]ing by different attacker computers over an extended amount of time. This results in a degraded quality of service and increased workload for the network's resources. This type of attack is more difficult to detect than traditional denial-of-service attacks due to their surreptitious nature.
| |
| − | | |
| − | ====Nukes====
| |
| − | Nukes are malformed or specially crafted packets.
| |
| − | | |
| − | [[WinNuke]] is a type of nuke, exploiting the vulnerability in the [[NetBIOS]] handler in [[Windows 95]]. A string of out-of-band data is sent to [[Transmission Control Protocol|TCP]] port 139 of the victim machine, causing it to lock up and display a [[Blue Screen of Death]].
| |
| − | | |
| − | ==== Distributed attack ====
| |
| − | | |
| − | A '''distributed denial of service attack''' ('''DDoS''') occurs when multiple compromised systems flood the bandwidth or resources of a targeted system, usually one or more web servers. These systems are compromised by attackers using a variety of methods.
| |
| − | | |
| − | Malware can carry DDoS attack mechanisms; one of the more well known examples of this was [[MyDoom]]. Its DoS mechanism was triggered on a specific date and time. This type of DDoS involved hardcoding the target IP address prior to release of the malware and no further interaction was necessary to launch the attack.
| |
| − | | |
| − | A system may also be compromised with a trojan, allowing the attacker to download a zombie agent (or the trojan may contain one). Attackers can also break into systems using automated tools that exploit flaws in programs that listen for connections from remote hosts. This scenario primarily concerns systems acting as servers on the web.
| |
| − | | |
| − | [[Stacheldraht]] is a classic example of a DDoS tool. It utilizes a layered structure where the attacker uses a client program to connect to handlers, which are compromised systems that issue commands to the [[Zombie computer|zombie agents]], which in turn facilitate the DDoS attack. Agents are compromised via the handlers by the attacker, using automated routines to exploit vulnerabilities in programs that accept remote connections running on the targeted remote hosts. Each handler can control up to a thousand agents.<ref>[http://staff.washington.edu/dittrich/misc/stacheldraht.analysis.txt The "stacheldraht" distributed denial of service attack tool]</ref>
| |
| − | | |
| − | These collections of compromised systems are known as botnets. DDoS tools like stacheldraht still use classic DoS attack methods centered around [[IP spoofing]] and amplification like [[smurf attack]]s and fraggle attacks (these are also known as bandwidth consumption attacks). SYN floods (also known as resource starvation attacks) may also be used. Newer tools can use DNS servers for DoS purposes. (see next section)
| |
| − | | |
| − | Unlike MyDoom's DDoS mechanism, botnets can be turned against any IP address. [[Script kiddies]] use them to deny the availability of well known websites to legitimate users.<ref>[http://www.sans.org/resources/idfaq/trinoo.php Intrusion Detection FAQ: Distributed Denial of Service Attack Tools: trinoo and wintrinoo]</ref> More sophisticated attackers use DDoS tools for the purposes of [[extortion]] — even against their business rivals.<ref>[http://www.theregister.co.uk/2004/09/23/authorize_ddos_attack/ US credit card firm fights DDoS attack]</ref>
| |
| − | | |
| − | It is important to note the difference between a DDoS and DoS attack. If an attacker mounts a smurf attack from a single host it would be classified as a DoS attack. In fact, any attack against availability would be classed as a Denial of Service attack (e.g. using [[High-energy radio-frequency weapons]] to render computer equipment inoperable, would be a DoS attack, albeit an exotic one.)<ref>[http://news.zdnet.com/2100-9595_22-515644.html?legacy=zdnn Zap! ... and your PC's dead]</ref>. On the other hand, if an attacker uses a thousand zombie systems to simultaneously launch smurf attacks against a remote host, this would be classified as a DDoS attack.
| |
| − | | |
| − | The major advantages to an attacker of using a distributed denial-of-service attack are that multiple machines can generate more attack traffic than one machine, multiple attack machines are harder to turn off than one attack machine, and that the behavior of each attack machine can be stealthier, making it harder to track down and shut down. These attacker advantages cause challenges for defense mechanisms. For example, merely purchasing more incoming bandwidth than the current volume of the attack might not help, because the attacker might be able to simply add more attack machines.
| |
| − | | |
| − | ==== Reflected attack ====
| |
| − | A '''distributed reflected denial of service attack''' ('''DRDoS''') involves sending forged requests of some type to a very large number of computers that will reply to the requests. Using [[Internet protocol spoofing]], the source address is set to that of the targeted victim, which means all the replies will go to (and flood) the target.
| |
| − | | |
| − | ICMP Echo Request attacks (described above) can be considered one form of reflected attack, as the flooding host(s) send Echo Requests to the broadcast addresses of mis-configured networks, thereby enticing a large number of hosts to send Echo Reply packets to the victim. Some early DDoS programs implemented a distributed form of this attack.
| |
| − | | |
| − | Many services can be exploited to act as reflectors, some harder to block than others.<ref>Paxson, Vern (2001), ''[http://www.icir.org/vern/papers/reflectors.CCR.01/reflectors.html An Analysis of Using Reflectors for Distributed Denial-of-Service Attacks]''</ref> DNS amplification attacks involve a new mechanism that increased the amplification effect, using a much larger list of DNS servers than seen earlier.<ref>Vaughn, Randal and Evron, Gadi (2006), ''[http://www.isotf.org/news/DNS-Amplification-Attacks.pdf DNS Amplification Attacks]''</ref>
| |
| − | | |
| − | ==== Unintentional attack ====
| |
| − | This describes a situation where a website ends up denied, not due to a deliberate attack by a single individual or group of individuals, but simply due to a sudden enormous spike in popularity. This can happen when an extremely popular website posts a prominent link to a second, less well-prepared site, for example, as part of a news story. The result is that a significant proportion of the primary site's regular users — potentially hundreds of thousands of people — click that link in the space of a few hours, having the same effect on the target website as a DDoS attack.
| |
| − | | |
| − | News sites and link sites — sites whose primary function is to provide links to interesting content elsewhere on the Internet — are most likely to cause this phenomenon. The canonical example is the [[Slashdot effect]]. Sites such as [[Digg]], [[Fark]], [[Something Awful]] and the webcomic [[Penny Arcade (webcomic)|Penny Arcade]] have their own corresponding "effects," known as "the Digg effect," "farking," "[[goon]]rushing" and "wanging"; respectively.
| |
| − | | |
| − | Routers have also been known to create unintentional DoS attacks, as both [[D-Link]] and [[Netgear]] routers have created [[NTP vandalism]] by flooding NTP servers without respecting the restrictions of client types or geographical limitations.
| |
| − | | |
| − | Similar unintentional attacks can also occur via other media, e.g. when a URL is mentioned on television. If a server is being indexed by [[Google]] or another search engine during peak periods of activity, or does not have a lot of available bandwidth while being indexed, it can also experience the effects of a DoS attack.
| |
| − | | |
| − | ====Incidents====
| |
| − | The first major attack involving DNS servers as reflectors occurred in January 2001. The attack was directed at the site Register.com.<ref>[http://staff.washington.edu/dittrich/misc/ddos/register.com-unisog.txt January 2001 thread on the UNISOG mailing list]</ref> This attack, which forged requests for the MX records of AOL.com (to amplify the attack) lasted about a week before it could be traced back to all attacking hosts and shut off. It used a list of tens of thousands of DNS servers that were at least a year old (at the time of the attack.)
| |
| − | | |
| − | In July 2002, the Honeynet Project Reverse Challenge was issued.<ref>[http://www.honeynet.org/reverse Honeynet Project Reverse Challenge]</ref> The binary that was analyzed turned out to be yet another DDoS agent, which implemented several DNS related attacks, including an optimized form of a reflection attack.
| |
| − | | |
| − | On two occasions to date, attackers have performed [[DNS Backbone DDoS Attacks]] on the DNS root servers. Since these machines are intended to provide service to all Internet users, these two denial of service attacks might be classified as attempts to take down the entire Internet, though it is unclear what the attackers' true motivations were. The first occurred in October 2002, and disrupted service at 9 of the 13 root servers. The second occurred in February 2007, and caused disruptions at two of the root servers.
| |
| − | | |
| − | === Prevention and response ===
| |
| − | ==== Surviving attacks ====
| |
| − | | |
| − | The investigative process should begin immediately after the DoS attack begins. There will be multiple phone calls, call backs, emails, pages and faxes between the victim organization, one's provider and others involved. It is a time consuming process, so the process should begin immediately. It has taken some very large networks with plenty of resources several hours to halt a DDoS.
| |
| − | | |
| − | The easiest way to survive an attack is to have planned for the attack. Having a separate emergency block of IP addresses for critical servers with a separate route can be invaluable. A separate route (perhaps a DSL) is not that extravagant, and it can be used for load balancing or sharing under normal circumstances and switched to emergency mode in the event of an attack.
| |
| − | | |
| − | Filtering is often ineffective, as the route to the filter will normally be swamped so only a trickle of traffic will survive. However, by using an extremely resilient stateful packet filter that will inexpensively<ref>ie. without consuming much processing power</ref> drop any unwanted packets, surviving a DDoS attack becomes much easier. When such a high performance packet filtering server is attached to an ultra high bandwidth connection (preferably an Internet backbone), communication with the outside world will be unimpaired so long as not all of the available bandwidth is saturated, and performance behind the packet filter will remain normal as long as the packet filter drops all DDoS packets.<ref>[[OpenBSD]]'s [[PF (firewall)|pf]] is a packet filter some providers use for exactly this purpose. [https://gold.rayservers.com/ddos-protection]</ref> It should be noted however, that in this case the victim of the DDoS attack still would need to pay for the excessive bandwidth. The price of service unavailability thus needs to be weighed against the price of truly exorbitant bandwidth/traffic.
| |
| − | | |
| − | ==== SYN Cookies ====
| |
| − | [[SYN cookies]] modify the TCP protocol handling of the server by delaying allocation of resources until the client address has been verified. This seems to be the most powerful defense against SyN attacks. There are [[Solaris Operating System|Solaris]] and [[Linux]] implementations. The Linux implementation can be turned on during runtime of the Linux kernel.
| |
| − | | |
| − | ==== Firewalls ====
| |
| − | [[Firewall (networking)|Firewall]]s have simple rules such as to allow or deny protocols, ports or IP addresses. Some DoS attacks are too complex for today's firewalls, e.g. if there is an attack on port 80 (web service), firewalls cannot prevent that attack because they cannot distinguish good traffic from DoS attack traffic. Additionally, firewalls are too deep in the network hierarchy. Your router may be affected even before the firewall gets the traffic. Nonetheless, firewalls can effectively prevent users from launching simple flooding type attacks from machines behind the firewall.[http://unixclan.no-ip.org/blog/?p=7]
| |
| − | | |
| − | Modern [[stateful firewall]]s like [[Check Point]] FW1 NGX & [[Cisco PIX]] have a built-in capability to differentiate good traffic from DoS attack traffic. This capability is known as a "Defender," as it confirms TCP connections are valid before proxying TCP packets to service networks (including border routers). A similar ability is present in OpenBSD's pF, which is available for other BSDs as well. In that context, it is called "synproxy."
| |
| − | | |
| − | ==== Switches ====
| |
| − | Most switches have some rate-limiting and [[Access control list|ACL]] capability. Some switches provide automatic and or system-wide rate limiting, traffic shaping, [[delayed binding]] ([[TCP splicing]]), [[deep packet inspection]] and [[Bogon filtering]] (bogus IP filtering) to detect and remediate denial of service attacks through automatic rate filtering and WAN Link failover and balancing.
| |
| − | | |
| − | These schemes will work as long as the DoS attacks are something that can be prevented using them. For example SYN flood can be prevented using delayed binding or TCP splicing. Similarly content based DoS can be prevented using deep packet inspection. Attacks originating from dark addresses or going to dark addresses can be prevented using Bogon filtering. Automatic rate filtering can work as long as you have set rate-thresholds correctly and granularly. Wan-link failover will work as long as both links have DoS/DDoS prevention mechanism.
| |
| − | | |
| − | ==== Routers ====
| |
| − | Similar to switches, routers have some rate-limiting and [[Access control list|ACL]] capability. They, too, are manually set. Most routers can be easily overwhelmed under DoS attack. If you add rules to take flow statistics out of the router during the DoS attacks, they further slow down and complicate the matter. [[Cisco IOS]] has features that prevents flooding, i.e. example settings [http://www.geocities.com/nonlinearphysics/cisco_ios_qos.html].
| |
| − | | |
| − | ====Application front end hardware====
| |
| − | Application front end hardware is intelligent hardware placed on the network before traffic reaches the servers. It can be used on networks in conjunction with routers and switches. Application front end hardware analyzes data packets as they enter the system, and then identifies them as priority, regular, or dangerous. There are more than 25 bandwidth management vendors. Hardware acceleration is key to bandwidth management. Look for granularity of bandwidth management, hardware acceleration, and automation while selecting an appliance.
| |
| − | | |
| − | ==== IPS based prevention ====
| |
| − | [[Intrusion-prevention system]]s are effective if the attacks have signatures associated with them. However, the trend among the attacks is to have '''legitimate content but bad intent'''. IPS systems which work on content recognition cannot block behavior based DoS attacks.
| |
| − | | |
| − | An ASIC based IPS can detect and block denial of service attacks because they have the processing power and the granularity to analyze the attacks and act like a circuit breaker in an automated way.
| |
| − | | |
| − | A rate-based IPS (RBIPS) must analyze traffic granularly and continuously monitor the traffic pattern and determine if there is traffic anomaly. It must let the legitimate traffic flow while blocking the DoS attack traffic.
| |
| − | | |
| − | | |
| − | ==Spam== | |
| − | {{Unreferenced|date=July 2006}}
| |
| | [[Image:spammed-mail-folder.png|thumb|300px|A [[KMail]] folder of spam messages.]] | | [[Image:spammed-mail-folder.png|thumb|300px|A [[KMail]] folder of spam messages.]] |
| − | '''Spamming''' is the abuse of electronic messaging systems to send unsolicited bulk messages, which are generally undesired. While the most widely recognized form of spam is [[email spam]], the term is applied to similar abuses in other media: [[Messaging spam|instant messaging spam]], [[Newsgroup spam|Usenet newsgroup spam]], [[spamdexing|Web search engine spam]], [[spam in blogs]], [[mobile phone spam|mobile phone messaging spam]], [[internet forum]] spam and [[Junk fax|junk fax transmissions]]. | + | '''Spamming''' is the abuse of electronic messaging systems to send unsolicited bulk messages, which are generally undesired. While the most widely recognized form of spam is [[email spam]], the term is applied to similar abuses in other media: [[Messaging spam|instant messaging spam]], [[Newsgroup spam|Usenet newsgroup spam]], [[spamdexing|Web search engine spam]], [[spam in blogs]], [[mobile phone spam|mobile phone messaging spam]], [[internet forum]] spam and [[Junk fax|junk fax transmissions]]. Spam is also called junk mail. Some email clients or servers have spam filters, which try to delete or move the spam messages. |
| − | Spam is also called junk mail. Some email clients or servers have spam filters, which try to delete or move the spam messages. | |
| | | | |
| | Spamming is economically viable because advertisers have no operating costs beyond the management of their mailing lists, and it is difficult to hold senders accountable for their mass mailings. Because the [[barrier to entry]] is so low, spammers are numerous, and the volume of unsolicited mail has become very high. The costs, such as lost productivity and fraud, are borne by the public and by [[Internet service provider]]s, which have been forced to add extra capacity to cope with the deluge. Spamming is widely reviled, and has been the subject of legislation in many jurisdictions. | | Spamming is economically viable because advertisers have no operating costs beyond the management of their mailing lists, and it is difficult to hold senders accountable for their mass mailings. Because the [[barrier to entry]] is so low, spammers are numerous, and the volume of unsolicited mail has become very high. The costs, such as lost productivity and fraud, are borne by the public and by [[Internet service provider]]s, which have been forced to add extra capacity to cope with the deluge. Spamming is widely reviled, and has been the subject of legislation in many jurisdictions. |
| | | | |
| − | === Spamming in different media ===
| |
| − | ==== Instant Messaging and Chat Room spam ====
| |
| − |
| |
| − |
| |
| − | Instant Messaging spam, sometimes termed ''spim'' (a [[portmanteau]] of spam and IM, short for instant messenger), makes use of [[instant messaging]] systems, such as [[AOL Instant Messenger]] or [[ICQ]]. Many IM systems offer a user directory, including demographic information that allows an advertiser to gather the information, sign on to the system, and send unsolicited messages. To send instant messages to millions of users requires scriptable software and the recipients' IM usernames. Spammers have similarly targeted [[Internet Relay Chat]] channels, using [[IRC bot]]s that join channels and bombard them with advertising.
| |
| − |
| |
| − | Messenger service spam has lent itself to spammer use in a particularly circular scheme. In many cases, messenger spammers send messages to vulnerable machines consisting of text like ''"Annoyed by these messages? Visit this site."'' The link leads to a Web site where, for a fee, users are told how to disable the Windows messenger service. Though the messenger service is easily disabled for free, the scam works because it creates a perceived need and offers a solution. Often the only "annoying messages" the user receives through Messenger are ads to disable Messenger itself. It is often using a false ID to get money or credit card numbers.
| |
| − |
| |
| − | ==== Chat spam ====
| |
| − | Chat spam can occur in any live chat environment like [[IRC]] and in-game multiplayer chat of online games. It consists of repeating the same word or sentence many times to get attention or to interfere with normal operations. It is generally considered very rude and may lead to swift exclusion of the user from the used chat service by the owners or moderators.
| |
| − |
| |
| − | The application of the name "Spam" to unwanted communication originates in Chat-room spam. Specifically, it was developed in the chat-rooms of People-Link in the early 1980s as a technique for getting rid of unwelcome newcomers. When someone would enter a chat-room full of friends who were in mid-conversation, and when the newcomer tried to turn the conversation in an unwelcome direction, two veteran members of the room would begin typing in the Monty Python “Spam” routine at high speed. They would fill the screen with “Spam Spam Spam eggs Spam Spam and Spam” etc, and make all other communication impossible. The other members of the room would just wait quietly until the newcomer got disgusted and moved on to a different room.
| |
| − |
| |
| − | ==== Newsgroup spam and forum spam ====
| |
| − | {{main|Newsgroup spam}}
| |
| − | {{main|Forum spam}}
| |
| − |
| |
| − | ==== Mobile phone spam ====
| |
| − |
| |
| − |
| |
| − | Mobile phone spam is directed at the [[text messaging]] service of a [[mobile phone]]. This can be especially irritating to customers not only for the inconvenience but also because of the fee that they are charged per text message.
| |
| − | The term "SpaSMS" was coined at the adnews website Adland in 2000 to describe spam SMS.
| |
| − |
| |
| − | ==== Online game messaging spam ====
| |
| − | Many online games allow players to contact each other via player-to-player messaging, chatrooms, or public discussion areas. What qualifies as spam varies from game to game, but usually this term applies to all forms of message flooding, violating the terms of service contract for the website.
| |
| − |
| |
| − | ==== Spam targeting search engines (spamdexing) ====
| |
| − |
| |
| − |
| |
| − | '''Spamdexing''' (a [[portmanteau]] of ''spamming'' and ''indexing'') refers to the practice on the [[World Wide Web]] of modifying [[HTML]] pages to increase the chances of them being placed high on [[search engine]] relevancy lists. These sites use "black hat [[search engine optimization]] techniques" to unfairly increase their rank in search engines. Many modern search engines modified their search algorithms to try to exclude web pages utilizing spamdexing tactics.
| |
| − |
| |
| − | ==== Blog, wiki, and guestbook spam ====
| |
| − |
| |
| − | [[Blog spam]], or "blam" for short, is spamming on [[weblog]]s. In 2003, this type of spam took advantage of the open nature of comments in the blogging software [[Movable Type]] by repeatedly placing comments to various blog posts that provided nothing more than a link to the spammer's commercial web site.<ref>[http://www.wired.com/wired/archive/12.03/google.html?pg=7 The (Evil) Genius of Comment Spammers] - ''Wired Magazine'', March 2004</ref>
| |
| − | Similar attacks are often performed against [[wiki]]s and [[guestbook]]s, both of which accept user contributions.
| |
| − |
| |
| − | === Noncommercial spam ===
| |
| | E-mail and other forms of spamming have been used for purposes other than advertisements. Many early Usenet spams were religious or political. [[Serdar Argic]], for instance, spammed Usenet with historical revisionist screeds. A number of [[evangelism|evangelists]] have spammed [[Usenet]] and e-mail media with preaching messages. A growing number of criminals are also using spam to perpetrate various sorts of fraud,<ref>See: [[Advance fee fraud]]</ref> and in some cases have used it to lure people to locations where they have been kidnapped, held for ransom, and even murdered.<ref>[http://www.news24.com/News24/South_Africa/News/0,,2-7-1442_1641875,00.html SA cops, Interpol probe murder] - ''News24.com'', 2004-[[12-31]]</ref> | | E-mail and other forms of spamming have been used for purposes other than advertisements. Many early Usenet spams were religious or political. [[Serdar Argic]], for instance, spammed Usenet with historical revisionist screeds. A number of [[evangelism|evangelists]] have spammed [[Usenet]] and e-mail media with preaching messages. A growing number of criminals are also using spam to perpetrate various sorts of fraud,<ref>See: [[Advance fee fraud]]</ref> and in some cases have used it to lure people to locations where they have been kidnapped, held for ransom, and even murdered.<ref>[http://www.news24.com/News24/South_Africa/News/0,,2-7-1442_1641875,00.html SA cops, Interpol probe murder] - ''News24.com'', 2004-[[12-31]]</ref> |
| − |
| |
| − | ==== Hobbit spam ====
| |
| − | In early July 2006 there has been an enormous increase in unsolicited messages from a spoofed address with approximately half a dozen random letter subjects, containing nothing but three lines from JRR [[Tolkien]]'s ''[[The Hobbit]]''. This follows fairly closely another similar form dubbed "[[Discordianism|discordian]] poetry" that appeared to used a random word generator of the same. The messages had no attempt to sell anything; it was theorised that this was a [[script kiddie]] ineptly running a spam suite. This was confirmed when shortly afterward the same format messages began appearing with image files overlaying the text (a common spam technique). It is suspected to be a variation from the same source and image overlays will begin appearing.<ref>[http://publications.mediapost.com/index.cfm?fuseaction=Articles.showArticleHomePage&art_aid=45537 Just An Online Minute... Hobbit Spam] - ''MediaPost Publications'', 2006-[[07-13]]</ref>
| |
| − |
| |
| − | ==== Spam as denial of service ====
| |
| − | Spamming has also been used as a [[denial of service]] ("DoS") tactic, particularly on Usenet. By overwhelming the readers of a newsgroup with an inordinate number of nonsense messages, legitimate messages and computing resources can be lost in the deluge. Since these messages are usually forged (that is, sent falsely under regular posters' names) this tactic has come to be known as [[sporgery]] (from ''spam'' + ''forgery''). This tactic has for instance been used by members of the [[Church of Scientology]] against the [[alt.religion.scientology]] newsgroup (see [[Scientology versus the Internet]]) and by spammers against [[news.admin.net-abuse.email]], a forum for mail administrators to discuss spam problems. Applied to e-mail, this is termed [[E-mail bomb|mailbombing]]. The Usenet [[Meow Wars]] (around 1996) were DoS attacks on various newsgroups aimed at specific posters that disrupted the newsgroups where they were active. The DoS attacks launched by [[Hipcrime (Usenet)|Hipcrime]], which continue today, are more crafted as DoS attacks on entire newsgroups. The [[alt.sex]] newsgroups were rendered uninhabitable by commercial porn site spammers, partially for advertising purposes and partially to destroy a perceived free competitor. (This spawned the creation of the moderated, unspammable [[soc.sexuality]] newsgroups.)
| |
| − |
| |
| − | Forged e-mail spam has been used as a tool of [[harassment]]. The spammer collects a list of addresses, then sends a spam to them signed with the name of the person he or she wishes to harass. Some recipients, angry they received spam and seeing an obvious "source," will respond angrily or pursue revenge against the apparent spammer, the forgery victim. A widely known victim of this sort of harassment was Joe's CyberPost,<ref>[http://www.joes.com/spammed.html Spam Attack!] - ''Joe's CyberPost''</ref> which has lent its name to the offense: it is known as a ''[[joe job]]''. "Joe jobs" have been used against antispammers: in recent examples, [[Steve Linford]] of [[Spamhaus Project]] and [[Timothy Walton]], a California attorney, have been targeted. Sometimes victims (such as [[ROKSO]]-listed spammers) are subscribed to lists that don't practice verified opt-in, such as magazine subscriptions and e-mail newsletters, a practise known as [[subscriptionbombing]].
| |
| − |
| |
| − | Spammers have abused resources set up for the purposes of anonymous speech online, such as [[anonymous remailer]]s. Many of these resources have been shut down, denying their services to legitimate users.
| |
| | | | |
| | E-mail [[computer virus|worms or viruses]] may be spammed to set up an initial pool of infected machines, which resend the virus to other machines in a spam-like manner. The infected machines can often be used as remote-controlled [[zombie computers]], for more spamming or [[DDoS]] attacks. [[Trojan horse (computing)|trojan]]s are spammed to [[phishing|phish]] for bank account details, or to set up a pool of zombies without using a virus. | | E-mail [[computer virus|worms or viruses]] may be spammed to set up an initial pool of infected machines, which resend the virus to other machines in a spam-like manner. The infected machines can often be used as remote-controlled [[zombie computers]], for more spamming or [[DDoS]] attacks. [[Trojan horse (computing)|trojan]]s are spammed to [[phishing|phish]] for bank account details, or to set up a pool of zombies without using a virus. |
| | | | |
| − | ==== In gaming ====
| + | Spam's direct effects include the consumption of computer and network resources, and the cost in human time and attention of dismissing unwanted messages. In addition, spam has costs stemming from the ''kinds'' of spam messages sent, from the ''ways'' spammers send them, and from the ''[[arms race]]'' between spammers and those who try to stop or control spam. In addition, there are the opportunity cost of those who forgo the use of spam-afflicted systems. There are the direct costs, as well as the indirect costs borne by the victims - both those related to the spamming itself, and to other crimes that usually accompany it, such as financial theft, [[identity theft]], data and intellectual property theft, virus and other malware infection, child pornography, fraud, and deceptive marketing. The [[European Union]]'s Internal Market Commission estimated in 2001 that "junk e-mail" cost Internet users €10 billion per year worldwide. <ref>[http://europa.eu/rapid/pressReleasesAction.do?reference=IP/01/154&format=HTML&aged=0&language=EN&guiLanguage=en "Data protection: "Junk" e-mail costs internet users 10 billion a year worldwide - Commission study"]</ref> |
| − | | |
| − | | |
| − | In gaming, spamming is often used to describe repetitive and disruptive behavior.
| |
| − | | |
| − | In first person shooter type games, spamming refers to tactics where a player repeatedly and randomly fires into an area in the hope of scoring chance hits. Many games attempt to limit this by providing scenarios such as [[Capture the Flag]].
| |
| − | | |
| − | Spamming also describes players who repeatedly use a particular move to gain benefits over other players. This is often seen in [[Player versus Player|PvP]] combat as well as [[MMORPG]] games.
| |
| − | | |
| − | The term also refers to the flooding of the in-game [[chat]] with frequent messaging, this is similar to [[messaging spam]] mentioned above.
| |
| − | | |
| − | === History ===
| |
| − | | |
| − | | |
| − | The term ''spam'' is derived from the [[Monty Python]] '''[[Spam (Monty Python)|SPAM sketch]]''' (see video in External Links), set in a [[cafe]] where nearly every item on the menu includes [[Spam (food)|SPAM]] luncheon meat. As the server recites the SPAM-filled menu, a chorus of [[Viking]] patrons drowns out all conversations with a song repeating "SPAM, SPAM, SPAM, SPAM... lovely SPAM, wonderful SPAM," hence "SPAMming" the dialogue. The excessive amount of SPAM mentioned in the sketch is a reference to [[United Kingdom|British]] rationing during [[World War II]]. SPAM was one of the few foods that was widely available.
| |
| − | | |
| − | Although the first known instance of unsolicited commercial e-mail occurred in 1978<ref>[http://www.templetons.com/brad/spamreact.html Reaction to the DEC Spam of 1978]</ref> (unsolicited electronic messaging had already taken place over other media, with the first recorded instance being via telegram on September 13 1904{{Fact|date=January 2007}}), the term "spam" for this practice had not yet been applied. In the 1980s the term was adopted to describe certain abusive users who frequented [[Bulletin Board System|BBS]]s and [[MUD]]s, who would repeat "SPAM" a huge number of times to scroll other users' text off the screen.<ref>http://www.templetons.com/brad/spamterm.html</ref> In early Chat rooms services like PeopleLink and the early days of AOL, they actually flooded the screen with quotes from the Monty Python Spam sketch. This was used as a tactic by insiders of a group that wanted to drive newcomers out of the room so the usual conversation could continue. It was also used to prevent members of rival groups from chatting — for instance, Star Wars fans often invaded Star Trek chat rooms, filling the space with blocks of text until the Star Trek fans left.<ref>[http://www.myshelegoldberg.com/writings/essays/spam.htm The Origins of Spam in Star Trek chatrooms]</ref> This act, previously called ''flooding'' or ''trashing'', came to be known as ''spamming''.<ref>[http://groups.google.com/groups?threadm=MAT.90Sep25210959%40zeus.organpipe.cs.arizona.edu Spamming? (rec.games.mud)] - ''Google Groups USENET archive'', 1990-[[09-26]]</ref> The term was soon applied to a large amount of text broadcasted by many users.
| |
| − | | |
| − | It later came to be used on [[Usenet]] to mean ''excessive multiple posting''—the repeated posting of the same message. The unwanted message would appear in many if not all newsgroups, just as SPAM appeared in all the menu items in the Monty Python sketch. The first usage of this sense was by [[Joel Furr]] in the aftermath of the [[ARMM (Usenet)|ARMM]] incident of March 31 1993, in which a piece of experimental software released dozens of recursive messages onto the ''news.admin.policy'' newsgroup. This use had also become established—to spam Usenet was flooding newsgroups with junk messages. As a [[portmanteau]] of "spew" and "scam," the word was also attributed to the flood of "Make Money Fast" messages that clogged many newsgroups during the 1990s.
| |
| − | | |
| − | Commercial spamming started in force on March 5, 1994, when a pair of lawyers, [[Canter & Siegel|Laurence Canter and Martha Siegel]], began using bulk [[Usenet]] posting to advertise [[immigration]] law services. The incident was commonly termed the "[[Green Card spam]]," after the subject line of the postings. The two went on to widely promote spamming of both Usenet and e-mail as a new means of advertisement—over the objections of Internet users they labeled "anti-commerce radicals." Within a few years, the focus of spamming (and antispam efforts) moved chiefly to e-mail, where it remains today.<ref>[http://www.templetons.com/brad/spamterm.html Origin of the term "spam" to mean net abuse]</ref>
| |
| − | | |
| − | There are three popular [[false etymology|false etymologies]] of the word "spam." The first, promulgated by Canter & Siegel themselves, is that "spamming" is what happens when one dumps a can of SPAM luncheon meat into a fan blade. The second is the [[backronym]] "'''s'''hit '''p'''osing '''a'''s '''m'''ail." The third is similar, using "'''s'''tupid '''p'''ointless '''a'''nnoying '''m'''essages."
| |
| − | | |
| − | In 1998, the [[New Oxford Dictionary of English]], which had previously only defined "spam" in relation to the trademarked food product, added a second definition to its entry for "spam": "Irrelevant or inappropriate messages sent on the Internet to a large number of newsgroups or users."<Ref>[http://news.com.com/2100-1023-214535.html "Oxford dictionary adds Net terms" on News.com]</Ref>
| |
| − | | |
| − | [[Hormel Foods Corporation]], the makers of SPAM luncheon meat, do not object to the Internet use of the term "spamming." However, they did ask that the capitalized word "SPAM" be reserved to refer to their product and trademark.<ref>[http://www.spam.com/legal/spam/ SPAM and the Internet] - ''Official SPAM Website''</ref> By and large, this request is obeyed in forums which discuss spam. In Hormel Foods v SpamArrest, Hormel attempted to assert its trademark rights against SpamArrest, a software company, from using the mark "spam," since Hormel owns the trademark. In a dilution claim, Hormel argued that Spam Arrest's use of the term "spam" had endangered and damaged "substantial goodwill and good reputation" in connection with its trademarked lunch meat and related products. Hormel also asserts that Spam Arrest's name so closely resembles its luncheon meat that the public might become confused, or might think that Hormel endorses Spam Arrest's products. Hormel did not prevail. Attorney Derek Newman responded on behalf of Spam Arrest: "Spam has become ubiquitous throughout the world to describe unsolicited commercial e-mail. No company can claim trademark rights on a generic term." Hormel stated on its website: "Ultimately, we are trying to avoid the day when the consuming public asks, 'Why would Hormel Foods name its product after junk email?'"<ref>[http://img.spamarrest.com/HormelSummaryJudgment.pdf Hormel Foods v SpamArrest, Motion for Summary Judgement, Redacted Version (PDF)]</ref>
| |
| − | | |
| − | Hormel also made two attempts that were dismissed in 2005 to revoke the mark "SPAMBUSTER".<ref>[http://www.lawreports.co.uk/WLRD/2005/CHAN/chanjanf0.3.htm Hormel Foods Corpn v Antilles Landscape Investments NV (2005) EWHC 13 (Ch)]</ref>
| |
| − | | |
| − | Hormel's Corporate Attorney Melanie J. Neumann also sent [[SpamCop]]'s Julian Haight a letter on August 27, 1999 requesting that he delete an objectionable image (a can of Hormel's SPAM luncheon meat product in a trash can), change references to UCE spam to all lower case letters, and confirm his agreement to do so.<ref>[http://www.spamcop.net/images/hormel_letter.gif Letter from Hormel's Corporate Attorney Melanie J. Neumann to SpamCop's Julian Haight]</ref>
| |
| − | | |
| − | === Costs of spam ===
| |
| − | The [[European Union]]'s Internal Market Commission estimated in 2001 that "junk e-mail" cost Internet users €10 billion per year worldwide. <ref>[http://europa.eu/rapid/pressReleasesAction.do?reference=IP/01/154&format=HTML&aged=0&language=EN&guiLanguage=en "Data protection: "Junk" e-mail costs internet users 10 billion a year worldwide - Commission study"]</ref>
| |
| − | | |
| − | The California legislature found that spam cost United States organizations alone more than $10 billion in 2004, including lost productivity and the additional equipment, software, and manpower needed to combat the problem.{{Fact|date=March 2007}}
| |
| − | | |
| − | Spam's direct effects include the consumption of computer and network resources, and the cost in human time and attention of dismissing unwanted messages. In addition, spam has costs stemming from the ''kinds'' of spam messages sent, from the ''ways'' spammers send them, and from the ''[[arms race]]'' between spammers and those who try to stop or control spam. In addition, there are the opportunity cost of those who forgo the use of spam-afflicted systems. There are the direct costs, as well as the indirect costs borne by the victims - both those related to the spamming itself, and to other crimes that usually accompany it, such as financial theft, [[identity theft]], data and intellectual property theft, virus and other malware infection, child pornography, fraud, and deceptive marketing. | |
| − | | |
| − | The methods of spammers are likewise costly. Because spamming contravenes the vast majority of ISPs' acceptable-use policies, most spammers have for many years gone to some trouble to conceal the origins of their spam. E-mail, Usenet, and instant-message spam are often sent through insecure [[proxy server]]s belonging to unwilling third parties. Spammers frequently use false names, addresses, phone numbers, and other contact information to set up "disposable" accounts at various Internet service providers. In some cases, they have used falsified or stolen [[credit card]] numbers to pay for these accounts. This allows them to quickly move from one account to the next as each one is discovered and shut down by the host ISPs. | |
| − | | |
| − | The costs of spam also include the collateral costs of the struggle between spammers and the administrators and users of the media threatened by spamming. <!-- This is incomplete —><ref>[http://linxnet.com/misc/spam/thank_spammers.html Thank the Spammers] - ''William R. James''
| |
| − | 2003-[[03-10]]</ref>
| |
| − | | |
| − | Many users are bothered by spam because it impinges upon the amount of time they spend reading their e-mail. Many also find the content of spam frequently offensive, in that [[pornography]] is one of the most frequently advertised products. Spammers send their spam largely indiscriminately, so pornographic ads may show up in a work place e-mail inbox—or a child's, the latter of which is illegal in many jurisdictions. Recently, there has been a noticeable increase in spam advertising websites that contain [[child pornography]].
| |
| − | | |
| − | Some spammers argue that most of these costs could potentially be alleviated by having spammers reimburse ISPs and individuals for their material. There are two problems with this logic: first, the rate of reimbursement they could credibly budget is not nearly high enough to pay the direct costs; and second, the human cost (lost mail, lost time, and lost opportunities) is basically unrecoverable.
| |
| − | | |
| − | E-mail spam exemplifies a [[tragedy of the commons]]: spammers use resources (both physical and human), without bearing the entire cost of those resources. In fact, spammers commonly do not bear the cost at all. This raises the costs for everyone. In some ways spam is even a potential threat to the entire e-mail system, as operated in the past.
| |
| − | | |
| − | Since e-mail is so cheap to send, a tiny number of spammers can saturate the Internet with junk mail. Although only a tiny percentage of their targets are motivated to purchase their products (or fall victim to their scams), the low cost may provide a sufficient conversion rate to keep the spamming alive. Furthermore, even though spam appears not to be economically viable as a way for a reputable company to do business, it suffices for professional spammers to convince a tiny proportion of gullible advertisers that it is viable for those spammers to stay in business. Finally, new spammers go into business every day, and the low costs allow a single spammer to do a lot of harm before finally realizing that the business is not profitable.
| |
| − | | |
| − | Some companies and groups "rank" spammers; spammers who make the news are sometimes referred to by these rankings.<ref>Spamhaus' [http://www.spamhaus.org/statistics/networks.lasso "TOP 10 spam service ISPs"]</ref><ref>[http://www.spamhaus.org/statistics/spammers.lasso The 10 Worst ROKSO Spammers]</ref> The secretive nature of spamming operations makes it difficult to determine how proliferated an individual spammer is, thus making the spammer hard to track, block or avoid. Also, spammers may target different networks to different extents, depending on how successful they are at attacking the target. Thus considerable resources are employed to actually measure the amount of spam generated by a single person or group. For example, victims that use common antispam hardware, software or services provide opportunities for such tracking. Nevertheless, such rankings should be taken with a pinch of salt.
| |
| − | | |
| − | ==== General costs of spam ==== | |
| − | In all cases listed above, including both commercial and non-commercial, "spam happens" due to a positive [[Cost-benefit analysis]] result.
| |
| − | | |
| − | '''Cost''' is the combination of
| |
| − | *Overhead: The costs and overhead of electronic spamming include bandwidth, developing or acquiring an email/wiki/blog spam tool, taking over or acquiring a host/zombie, etc.
| |
| − | *[[Transaction cost]]: The incremental cost of contacting each additional recipient once a method of spamming is constructed, multiplied by the number of recipients. (see [[CAPTCHA]] as a method of increasing transaction costs)
| |
| − | *Risks: Chance and severity of legal and/or public reactions, including [[damages]] and [[punitive damages]]
| |
| − | *Damage: Impact on the community and/or communication channels being spammed (see [[Newsgroup spam]])
| |
| − | | |
| − | '''Benefit''' is the total expected profit from spam, which may include any combination of the commercial and non-commercial reasons listed above. It is normally linear, based on the incremental benefit of reaching each additional spam recipient, combined with the [[conversion rate]].
| |
| − | | |
| − | Spam is prevalent on the Internet because the transaction cost of electronic communications is radically less than any alternate form of communication, far outweighing the current potential losses, as seen by the amount of spam currently in existence. Spam continues to spread to new forms of electronic communication as the gain (number of potential recipients) increases to levels where the cost/benefit becomes positive. Spam has most recently evolved to include wikispam and blogspam as the levels of readership increase to levels where the overhead is no longer the dominating factor. According to the above analysis, spam levels will continue to increase until the cost/benefit analysis is balanced {{Fact|date=January 2007}}.
| |
| − | | |
| − | === In crime ===
| |
| − | {{sectstub}}
| |
| − | | |
| − | Spam can be used to spread [[computer virus]]es, [[Trojan horse (computing)|trojan horse]]s or other malicious software. The objective may be [[identity theft]], or worse (eg. [[advance fee fraud]]). Some spam attempts to capitalise on human greed whilst other attempts to use the victims inexperience with computers to trick them (eg. [[Phishing]]).
| |
| − | | |
| − | === Political issues ===
| |
| − | {{pov-section}}
| |
| − | Spamming remains a hot discussion topic. In 2004, the seized [[Porsche]] of an indicted spammer was advertised on the Internet;[http://www.timewarner.com/corp/newsroom/pr/0,20812,670327,00.html] this revealed the extent of the financial rewards available to those who are willing to commit duplicitous acts online. However, some of the possible means used to stop spamming may lead to other side effects, such as increased government control over the Internet, loss of privacy, barriers to free expression, and the commercialization of e-mail.
| |
| − | | |
| − | One of the chief values favored by many long-time Internet users and experts, as well as by many members of the public, is the free exchange of ideas. Many have valued the relative [[anarchy (word)|anarchy]] of the Internet, and bridle at the idea of restrictions placed upon it.{{Fact|date=February 2007}} A common refrain from spam-fighters is that spamming itself abridges the historical freedom of the Internet, by attempting to force users to carry the ''costs'' of material which they would not choose.
| |
| − | | |
| − | An ongoing concern expressed by parties such as the [[Electronic Frontier Foundation]] and the [[ACLU]] has to do with so-called "stealth blocking," a term for ISPs employing aggressive spam blocking without their users' knowledge. These groups' concern is that ISPs or technicians seeking to reduce spam-related costs may select tools which (either through error or design) also block non-spam e-mail from sites seen as "spam-friendly." [[Spam Prevention Early Warning System|SPEWS]] is a common target of these criticisms. Few object to the existence of these tools; it is their use in filtering the mail of users who are not informed of their use which draws fire.
| |
| − | | |
| − | Some see spam-blocking tools as a threat to free expression—and laws against spamming as an untoward precedent for regulation or taxation of e-mail and the Internet at large. Even though it is possible in some jurisdictions to treat some spam as unlawful merely by applying existing laws against [[trespass]] and [[conversion (law)|conversion]], some laws specifically targeting spam have been proposed. In 2004, United States passed the [[Can Spam Act of 2003]] which provided ISPs with tools to combat spam. This act allowed [[Yahoo!]] to successfully sue Eric Head, reportedly one of the biggest spammers in the world, who settled the lawsuit for several thousand U.S. dollars in June 2004. But the law is criticized by many for not being effective enough. Indeed, the law was supported by some spammers and organizations which support spamming, and opposed by many in the antispam community. Examples of effective anti-abuse laws that respect free speech rights include those in the U.S. against unsolicited faxes and phone calls, and those in Australia and a few U.S. states against spam.
| |
| − | | |
| − | In November 2004, [[Lycos Europe]] released a screensaver called [[make LOVE not SPAM]] which made [[Distributed Denial of Service]] attacks on the spammers themselves. It met with a large amount of controversy and the initiative ended in December 2004.
| |
| − | | |
| − | === Court cases ===
| |
| − | ==== United States ====
| |
| − | Attorney [[Laurence Canter]] was disbarred by the [[Supreme Court of Tennessee]] in 1997 for sending prodigious amounts of spam advertising his [[immigration law]] practice.
| |
| − | | |
| − | Robert Soloway lost a case in a federal court against the operator of a small Oklahoma-based Internet service provider who accused him of spamming. U.S. Judge Ralph G. Thompson granted a motion by plaintiff Robert Braver for a [[default judgment]] and permanent [[injunction]] against him. The judgment includes a statutory damages award of $10,075,000 under Oklahoma law.<ref>[http://www.mortgagespam.com/soloway Braver v. Newport Internet Marketing Corporation et al] - ''U.S. District Court - Western District of Oklahoma (Oklahoma City)'', 2005-[[02-22]]</ref>
| |
| − | | |
| − | In 2005, [[Jason Smathers]], a former [[America Online]] employee, pled guilty to charges of violating the CAN-SPAM ACT. In 2003, he sold a list of approximately 93 million AOL subscriber e-mail addresses to Sean Dunaway who, in turn, sold the list to spammers.<ref>U.S. v Jason Smathers and Sean Dunaway, amended complaint, US District Court for the Southern District of New York (2003). Retrieved 07 March, 2007, from http://www.thesmokinggun.com/archive/0623042aol1.html</ref><ref>Ex-AOL employee pleads guilty in spam case. (2005, February 4). CNN. Retrieved 07 March, 2007, from http://www.cnn.com/2005/TECH/internet/02/04/aol.spam.plea/</ref>
| |
| − | | |
| − | ==== United Kingdom ====
| |
| − | In the first successful case of its kind, Mr. Nigel Roberts from the [[Channel Islands]] won £270 against [[Media Logistics UK]] who sent junk e-mails to his personal account.<ref>[http://news.bbc.co.uk/1/hi/world/europe/jersey/4562726.stm Businessman wins e-mail spam case] - ''BBC News'', 2005-[[12-27]]</ref>
| |
| − | | |
| − | January 2007, the Sheriff Court in Scotland awarded Mr. Gordon Dick a £1368.66 against Transcom Internet Services Ltd.<ref>[http://www.scotchspam.co.uk/transcom.html Gordon Dick v Transcom Internet Service Ltd.]</ref> who allegedly breached anti-spam laws.<ref>[http://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=CELEX:32002L0058:EN:HTML Article 13-Unsolicited communications]</ref> It is the largest amount awarded in compensation in the United Kingdom since the Nigel Roberts case in 2005 above.
| |
| − | | |
| − | | |
| − | | |
| − | | |
| − | | |
| − | | |
| | | | |
| | + | ==Relevance of Cybercrime== |
| | + | Cybercrime is becoming a particularly relevant problem to police around the world and to society at large. The growing presence of the internet and computers in homes around the world means that more people are exposed to cybercrime each year. The rise in popularity of broadband internet access also means a greater risk. In an era where all data is being digitized and stored on computers, protecting computers is going to be integral to personal and national security. |
| | | | |
| | ==Notes== | | ==Notes== |
| Line 403: |
Line 89: |
| | | | |
| | == References == | | == References == |
| − |
| |
| − | <div class="references-small">
| |
| | * {{cite book | authorlink = Steven Levy | last = Levy | first = Steven | title = [[Hackers: Heroes of the Computer Revolution]] | year = 1984 | id = ISBN 0-385-19195-2 | publisher = Doubleday }} | | * {{cite book | authorlink = Steven Levy | last = Levy | first = Steven | title = [[Hackers: Heroes of the Computer Revolution]] | year = 1984 | id = ISBN 0-385-19195-2 | publisher = Doubleday }} |
| | *[[Sherry Turkle|Turkle, Sherry]] (1984),''The Second Self: Computers and the Human Spirit'' , New Edition: MIT Press 2005, ISBN 0262701111 | | *[[Sherry Turkle|Turkle, Sherry]] (1984),''The Second Self: Computers and the Human Spirit'' , New Edition: MIT Press 2005, ISBN 0262701111 |
| Line 412: |
Line 96: |
| | * {{cite book | last = Verton | first = Dan | title = The Hacker Diaries : Confessions of Teenage Hackers | year = 2002 | id = ISBN 0-07-222364-2 | publisher = McGraw-Hill Osborne Media }} | | * {{cite book | last = Verton | first = Dan | title = The Hacker Diaries : Confessions of Teenage Hackers | year = 2002 | id = ISBN 0-07-222364-2 | publisher = McGraw-Hill Osborne Media }} |
| | * {{cite book | autherlink = Paul Graham | last = Graham | first = Paul | title = [[Hackers and Painters]] | year = 2004 | id = ISBN 0-59-600662-4 }} | | * {{cite book | autherlink = Paul Graham | last = Graham | first = Paul | title = [[Hackers and Painters]] | year = 2004 | id = ISBN 0-59-600662-4 }} |
| − | </div>
| |
| − |
| |
| − |
| |
| − |
| |
| − |
| |
| − |
| |
| − |
| |
| − |
| |
| | | | |
| | ==External Links== | | ==External Links== |
| − | ==Academic resources==
| |
| − |
| |
| | *[http://cybercrimes.net/ Cybercrimes.net] and [http://steeplemedia.com/blogs/cyb3r_crim3/ Cyb3rCrim3.org] Susan W. Brenner | | *[http://cybercrimes.net/ Cybercrimes.net] and [http://steeplemedia.com/blogs/cyb3r_crim3/ Cyb3rCrim3.org] Susan W. Brenner |
| − | *[http://www.jisclegal.ac.uk/cybercrime/cybercrime.htm Cybercrime - High Tech crime] JISC Legal Information Service
| |
| − | *[http://www.lib.msu.edu/harris23/crimjust/cybercri.htm Criminal Justice Resources - Cybercrime]
| |
| − | *[http://information-retrieval.info/cybercrime/ Cybercrime NYLS]
| |
| | *[http://www.cybercrimelaw.org/ Cybercrime Law] | | *[http://www.cybercrimelaw.org/ Cybercrime Law] |
| − |
| |
| − | ==Government resources==
| |
| − |
| |
| | *[http://www.cybercrime.gov/ Cybercrime.gov] US Department of Justice CCIPS | | *[http://www.cybercrime.gov/ Cybercrime.gov] US Department of Justice CCIPS |
| − | *[http://www.us-cert.gov/ US CERT] United States Computer Emergency Readiness Team (US-CERT)
| |
| | *[http://www.fbi.gov/cyberinvest/cyberhome.htm FBI Cyber Investigations Home Page] | | *[http://www.fbi.gov/cyberinvest/cyberhome.htm FBI Cyber Investigations Home Page] |
| | *[http://www.ustreas.gov/usss/financial_crimes.shtml#Computer US Secret Service Computer Fraud] | | *[http://www.ustreas.gov/usss/financial_crimes.shtml#Computer US Secret Service Computer Fraud] |
| | *[http://onguardonline.gov/index.html On Guard] OnGuardOnline.gov provides practical tips from the federal government and the technology industry to help you be on guard against Internet fraud, secure your computer, and protect your personal information. | | *[http://onguardonline.gov/index.html On Guard] OnGuardOnline.gov provides practical tips from the federal government and the technology industry to help you be on guard against Internet fraud, secure your computer, and protect your personal information. |
| | *[http://www.consumer.gov/idtheft/ ID Theft] one-stop national resource to learn about the crime of identity theft | | *[http://www.consumer.gov/idtheft/ ID Theft] one-stop national resource to learn about the crime of identity theft |
| − | *[http://www.findlaw.com/01topics/10cyberspace/computercrimes/index.html FindLaw Computer Crime]
| |
| − | *[http://www.rcmp-grc.gc.ca/scams/ccprev_e.htm RCMP Computer Crime Prevention] Royal Canadian Mounted Police
| |
| − |
| |
| − | ==Commercial resources==
| |
| − |
| |
| | *[http://www.e-crimecongress.org Annual e-Crime Conference] : International Conference for Public & Private Security Specialists | | *[http://www.e-crimecongress.org Annual e-Crime Conference] : International Conference for Public & Private Security Specialists |
| − |
| |
| − | ==Further reading==
| |
| − |
| |
| − | * [http://www.criminallawyergroup.com/criminal-defense/the-evolution-of-cybercrime-from-past-to-the-present.php The evolution of cybercrime from past to the present]
| |
| − | * [http://news.com.com/Cybercrime+and+punishment/2009-7348-6150800.html?part=dht&tag=nl.e433 CNET - Cybercrime and Punishment]
| |
| − |
| |
| − |
| |
| − | ==External links==
| |
| − |
| |
| − | * [http://www.idfraud.org.uk All Party Parliamentary Group on Identity Fraud Website] - initiative of British parlimenatrians
| |
| − | * [http://www.privacyrights.org/identity.htm Privacy Rights Clearinghouse webpages] a non profit consumer information and advocacy organisation
| |
| − | * [http://www.ftc.gov/bcp/edu/microsites/idtheft/ U.S. (FTC.gov) website devoted to ID theft]
| |
| − | * [http://www.identitytheftinsider.com/identity-theft-risks/reduce-your-identity-theft-risk/ Identity Theft Insider] - Identity Theft from a previous victim's perspective
| |
| − | * [http://www.identitylockblog.info IdentityLockBlog.Info] - Blog tracking identity theft developments with daily news updates
| |
| − | * [http://www.identitytheftsecrets.com/videos/paypalemail3.html IdentityTheftSecrets.com] - Very clever anatomy of a phishing scheme in action
| |
| − | * [http://alabamaconsumerlawblog.com AlabamaConsumerLawBlog.com] - Blog tracking consumer law and identity theft issues
| |
| − | * [http://www.identitytheft.org.uk/ United Kingdom Home Office Identity Theft Website]
| |
| − | * [http://www.usdoj.gov/criminal/fraud/idtheft.html Identity Theft and Fraud] from the US Dept. of Justice
| |
| − | * [http://www.usdoj.gov/criminal/fraud/Internet.htm Internet Fraud] from the US Dept. of Justice
| |
| − | * [http://www.mysecurecyberspace.org/encyclopedia/index/identity-theft.html#msc.encyclopedia.identitytheft Identity Theft] — Carnegie Mellon CyLab's MySecureCyberspace, a portal on cybersecurity for home users
| |
| − | *[http://www.epic.org/privacy/consumer/states.html Privacy Laws by State]
| |
| − | * [http://www.idtheftcenter.org/index.shtml] The Identity Theft Resource Center, a nonprofit, nationally respected program dedicated exclusively to identity theft.
| |
| − | * {{cite news | first= | last= | coauthors= | title=Transcript of Attorney General Alberto R. Gonzales and FTC Chairman Deborah Platt Majoras Announcing the Release of the President's Identity Theft Task Force | date=April 23, 2007 | publisher= | url =http://www.usdoj.gov/ag/speeches/2007/ag_speech_0704231.html | work =US Department of Justice | pages = | accessdate = 2007-04-24 | language = }}
| |
| − | * [http://www.creditlock.com/identitythefttaskforce.html Identity Theft Crackdown: Strengths, Weaknesses and Red Flags For Identity Theft Task Force Strategic Plan] GammaWealth Strategy & Research, LLC
| |
| − | * [http://ezinearticles.com/?Identity-Theft---The-Time-Bomb-On-Your-Desktop&id=386274 Identity Theft - The Time Bomb On Your Desktop] Richard Odell - Computer security article
| |
| − | * [http://www.crediteria.com/CreditChat/2007/03/resources_for_protection_from.htm Worksheet to follow if you suspect you are a victim of identity theft] - Steps and resources to contact for victims of identity theft
| |
| − |
| |
| − |
| |
| − |
| |
| − | * [http://www.usdoj.gov/criminal/fraud/Internet.htm Article about Internet Fraud from the U.S. Department of Justice]
| |
| − | * [http://www.fraud.org/internet/intinfo.htm National Consumer's League Internet Fraud Page]
| |
| − | * [http://travel.state.gov/travel/tips/brochures/brochures_1216.html Advanced Fee Business Scams] U.S. Department of State Article
| |
| − | * [http://www.sec.gov/investor/pubs/cyberfraud.htm Internet Fraud: How to Avoid Internet Investment Scams] from the US Securities and Exchange Commission
| |
| − | * [http://www.fbi.gov/majcases/fraud/internetschemes.htm FBI Overview of Internet Fraud]
| |
| − |
| |
| − |
| |
| − |
| |
| − | * Stephanos Androutsellis-Theotokis and Diomidis Spinellis. [http://www.spinellis.gr/pubs/jrnl/2004-ACMCS-p2p/html/AS04.html A survey of peer-to-peer content distribution technologies]. ACM Computing Surveys, 36(4):335–371, December 2004. [http://dx.doi.org/10.1145/1041680.1041681 doi:10.1145/1041680.1041681].
| |
| − | * Stefan Saroiu, P. Krishna Gummadi, and Steven D. Gribble. [http://www.cs.ucsb.edu/~almeroth/classes/F02.276/papers/p2p-measure.pdf A Measurement Study of Peer-to-Peer File Sharing Systems]. Technical Report # UW-CSE-01-06-02. Department of Computer Science & Engineering. University of Washington. Seattle, WA, USA.
| |
| − | * Ralf Steinmetz, Klaus Wehrle (Eds). [http://www.peer-to-peer.info/ Peer-to-Peer Systems and Applications]. ISBN 3-540-29192-X, Lecture Notes in Computer Science, Volume 3485, Sep 2005
| |
| − | * [[Shuman Ghosemajumder|Ghosemajumder, Shuman]]. ''[http://shumans.com/p2p-business-models.pdf Advanced Peer-Based Technology Business Models]''. [[MIT Sloan School of Management]], 2002.
| |
| − | * Silverthorne, Sean. ''[http://hbswk.hbs.edu/item.jhtml?id=4206&t=innovation Music Downloads: Pirates- or Customers?]''. [[Harvard Business School|Harvard Business School Working Knowledge]], 2004.
| |
| − | * [http://www.cs.huji.ac.il/labs/danss/p2p/resources.html Selected Papers] — A collection of academic papers
| |
| − |
| |
| − |
| |
| − | *The [http://www.catb.org/~esr/jargon Jargon File]
| |
| − | *The [http://wikihost.org/wikis/newjargonfile/ New Jargon File]: An effort to establish an open hacker culture document, in the tradition of the [[Jargon File]]
| |
| − | *[http://www.casoabierto.com/Actualidad/Reportajes/The-Ten-Biggest-Legends-of-the-Hacker-Universe.html The Ten Biggest Legends of the Hacker Universe]
| |
| − | *[http://www.catb.org/~esr/faqs/hacker-howto.html How To Become A Hacker] by [[Eric S. Raymond]]
| |
| − | *[http://stallman.org/articles/on-hacking.html On Hacking] by [[Richard Stallman|Richard M. Stallman]]
| |
| − | *The [http://hacks.mit.edu/ MIT Gallery of Hacks]
| |
| − |
| |
| − |
| |
| − |
| |
| − |
| |
| − | *[http://www.antiphishing.org/reports/APWG_CrimewareReport.pdf US Department of Homeland Security Identity Theft Technology Council report "The Crimeware Landscape: Malware, Phishing, Identity Theft and Beyond"]
| |
| − | * [http://www.microsoft.com/emea/itsshowtime/sessionh.aspx?videoid=359 Video: Mark Russinovich - Advanced Malware Cleaning]
| |
| − |
| |
| − |
| |
| − |
| |
| − | * RFC 4732 Internet Denial-of-Service Considerations
| |
| − | * [http://foro.elhacker.net/index.php/topic,137442.0.html Intentando detener un DDoS] (en español)
| |
| − | * [http://www.w3.org/Security/Faq/wwwsf6.html W3C The World Wide Web Security FAQ ]
| |
| − | * [http://www.cert.org/tech_tips/denial_of_service.html cert.org] CERT's Guide to DoS attacks.
| |
| − | * [http://staff.washington.edu/dittrich/misc/ddos/ washington.edu] Dave Dittrich's DDoS page.
| |
| − | * [http://www.surasoft.com/articles/ddosa.php surasoft.com] - DDoS case study, concepts, and protection.
| |
| − | * [http://www.tik.ee.ethz.ch/~ddosvax/ tik.ee.ethz.ch] DDoSVax Research Project at the [http://www.ethz.ch/ Swiss Federal Institute of Technology] in [[Zürich]].
| |
| − | * [http://www.prolexic.com/labs prolexic.com] - Prolexic Whitepaper on DDoS mitigation
| |
| − | * [http://www.honeypots.net/incidents/ddos-mitigation honeypots.net] Papers and presentations on DDoS mitigation techniques.
| |
| − | * [http://www.denialinfo.com/dos.html DoS attack resources]
| |
| − | * [http://newssocket.com/foonet/ newssocket.com] An article regarding a DDoS for hire incident.
| |
| − | * [http://www.grc.com/dos/drdos.htm grc.com] General information regarding DoS attacks.
| |
| − | * [http://www.isotf.org/news/DNS-Amplification-Attacks.pdf isotf.org] General information regarding DNS reflector and amplification DDoS attacks.
| |
| − | * [http://www.linuxsecurity.com/content/view/121960/49/ linuxsecurity.com] An article on preventing DDoS attacks.
| |
| − | * [http://www.intruguarddevices.com/resources_dosarticles.html intruguarddevices.com] News articles on DDoS attacks.
| |
| − | * [http://whatis.techtarget.com/definition/0,289893,sid9_gci213591,00.html whatis.com – Denial of Service]
| |
| − | * [http://www.cert.org/tech_tips/denial_of_service.html Denial of Service] (Carnegie Mellon) CC Denial of Service Attacks
| |
| − | * [http://www.us-cert.gov/cas/tips/ST04-015.html Understanding Denial of Service Attack. US-CERT]
| |
| − | * [http://www.geocities.com/nonlinearphysics/cisco_ios_qos.html Cisco IOS commands to prevent flooding.]
| |
| − | * [http://frankgerlach.blogspot.com A proposal for defeating SYN attacks by a protocol change]
| |
| − | * [http://matthewhutchinson.net/files/Final_Report.pdf (Queens University Belfast) Denial of Service Study]
| |
| − | * [http://www.ddosinfo.com DDoSInfo.com Blog About The Latest DDoS Incidents]
| |
| − |
| |
| − |
| |
| − | * [http://www.spamtrackers.eu/wiki Spamtrackers SpamWiki]: a peer-reviewed spam information and analysis resource.
| |
| − | * [http://www.ftc.gov/spam/ Federal Trade Commission page advising people to forward spam e-mail to them]
| |
| − | * [http://www.ftc.gov/bcp/conline/pubs/alerts/spamalrt.htm ''E-mail Address Harvesting: How Spammers Reap What You Sow''] by the Federal Trade Commission
| |
| − | * [http://www.uic.edu/depts/accc/newsletter/adn29/spam.html Slamming Spamming Resource on Spam]
| |
| − | * [http://www.cdt.org/speech/spam/030319spamreport.shtml Why am I getting all this spam? CDT]
| |
| − | * [http://www.cybertelecom.org/spam/ Cybertelecom :: Federal SPAM law and policy]
| |
| − |
| |
| − |
| |
| − |
| |
| − |
| |
| | | | |
| | {{Credits|Cybercrime|131362470|Identity_theft|133371583|Internet_fraud|133383415|File_sharing|134479220|Hacker|134774806|Malware|133592383|Denial-of-service_attack|133240660|Spam_(electronic)|134818290|}} | | {{Credits|Cybercrime|131362470|Identity_theft|133371583|Internet_fraud|133383415|File_sharing|134479220|Hacker|134774806|Malware|133592383|Denial-of-service_attack|133240660|Spam_(electronic)|134818290|}} |
Cybercrime is a term used broadly to describe activity in which computers or networks are a tool, a target, or a place of criminal activity. These categories are not exclusive and many activities can be characterized as falling in one or more categories. Cybercrime takes a number of forms including identity theft, internet fraud, violation of copyright laws through file sharing, hacking, computer viruses, denial of service attacks, and spam.
Overview
Although the term cybercrime is usually restricted to describing criminal activity in which the computer or network is an essential part of the crime, this term is also used to include traditional crimes in which computers or networks are used to enable the illicit activity.
Examples of cybercrime in which the computer or network is a tool of the criminal activity include spamming and certain intellectual property and criminal copyright crimes, particularly those facilitated through peer-to-peer networks.
Examples of cybercrime in which the computer or network is a target of criminal activity include unauthorized access (i.e, defeating access controls), malicious code, and denial-of-service attacks.
Examples of cybercrime in which the computer or network is a place of criminal activity include theft of service (in particular, telecom fraud) and certain financial frauds.
Finally, examples of traditional crimes facilitated through the use of computers or networks include Nigerian 419 or other gullibility or social engineering frauds (e.g., "phishing"), identity theft, child pornography, online gambling, securities fraud, etc. Cyberstalking is an example of a traditional crime — harassment — that has taken a new form when facilitated through computer networks.
Additionally, certain other information crimes, including trade secret theft and industrial or economic espionage, are sometimes considered cybercrimes when computers or networks are involved.
Cybercrime in the context of national security may involve hacktivism (online activity intended to influence policy), traditional espionage, or information warfare and related activities.
Another way to define cybercrime is simply as criminal activity involving the information technology infrastructure, including illegal access (unauthorized access), illegal interception (by technical means of non-public transmissions of computer data to, from or within a computer system), data interference (unauthorized damaging, deletion, deterioration, alteration or suppression of computer data), systems interference (interfering with the functioning of a computer system by inputting, transmitting, damaging, deleting, deteriorating, altering or suppressing computer data), misuse of devices, forgery (ID theft), and electronic fraud.
Types
Child Pornography
The issue of child pornography has become more important due to its widespread distribution and availability on the internet. Child pornography is widely seen as a form of child abuse and its production, distribution, and possession is outlawed in most countries. Prohibition may include images or videos of children engaged in sexual acts or of nude children. Many American states have made efforts to pass legislation outlawing its transmission via the internet.
Computer Viruses and other Malware
Malware is software designed to infiltrate or damage a computer system without the owner's informed consent. It is a portmanteau of the words "malicious" and "software." The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code. Many normal computer users are however still unfamiliar with the term, and most never use it. Instead, "(computer) virus" is used in common parlance and often in the general media to describe all kinds of malware. Another term that has been recently coined for malware is badware, perhaps due to the anti-malware initiative Stopbadware or corruption of the term "malware." Software is considered malware based on the perceived intent of the creator rather than any particular features. It includes computer viruses, worms, trojan horses, spyware, dishonest adware, and other malicious and unwanted software. In law, malware is sometimes known as a computer contaminant, for instance in the legal codes of California, West Virginia, and several other U.S. states.[1]
Many early infectious programs, including the Internet Worm and a number of MS-DOS viruses, were written as experiments or pranks generally intended to be harmless or merely annoying rather than to cause serious damage. Since the rise of widespread broadband Internet access, more malicious software has been designed for a profit motive. For instance, since 2003, the majority of widespread viruses and worms have been designed to take control of users' computers for black-market exploitation. Infected "zombie computers" are used to send email spam, to host contraband data such as child pornography, or to engage in distributed denial-of-service attacks as a form of extortion.[2]
Another strictly for-profit category of malware has emerged in spyware — programs designed to monitor users' web browsing, display unsolicited advertisements, or redirect affiliate marketing revenues to the spyware creator. Spyware programs do not spread like viruses; they are generally installed by exploiting security holes or are packaged with user-installed software.
Denial of service attacks
In computer security and crime, a denial-of-service attack (DoS attack) is an attempt to make a computer resource unavailable to its intended users. Although the means to, motives for and targets of a DoS attack may vary, it generally comprises the concerted, malevolent efforts of a person or persons to prevent an Internet site or service from functioning efficiently or at all, temporarily or indefinitely. Perpetrators of DoS attacks typically — but not exclusively — target sites or services hosted on high-profile web servers.
One common method of attack involves saturating the target (victim) machine with external communications requests, such that it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable. In general terms, DoS attacks are implemented by:
- forcing the targeted computer(s) to reset, or consume its resources such that it can no longer provide its intended service; and/or,
- obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.
The easiest way to survive an attack is to have planned for the attack. Having a separate emergency block of IP addresses for critical servers with a separate route can be invaluable. A separate route (perhaps a DSL) is not that extravagant, and it can be used for load balancing or sharing under normal circumstances and switched to emergency mode in the event of an attack. Other preventative measures include firewalls, SYN cookies, switches, and routers.
Denial of service attacks are one form of computer sabotage whereby people can effectively ruin their target's operations for what could be a lengthy period of time.
File sharing
File sharing is the practice of making files available for other users to download over the Internet and smaller networks. Usually file sharing follows the peer-to-peer (P2P) model, where the files are stored on and served by personal computers of the users. Most people who engage in file sharing are also downloading files that other users share. Sometimes these two activities are linked together. P2P file sharing is distinct from file trading in that downloading files from a P2P network does not require uploading, although some networks either provide incentives for uploading such as credits or force the sharing of files being currently downloaded.
Under US law "the Betamax decision" (Sony Corp. of America v. Universal City Studios, Inc.), case holds that copying "technologies" are not inherently illegal, if substantial non-infringing use can be made of them. This decision, predating the widespread use of the Internet applies to most data networks, including peer-to-peer networks, since distribution of correctly licensed files can be performed. These non-infringing uses include sending open source software, public domain files and out of copyright works. Other jurisdictions tend to view the situation in somewhat similar ways.
In practice, many of the files shared on peer-to-peer networks are copies of copyrighted popular music and movies. Sharing of these copies among strangers is illegal in most jurisdictions. This has led many observers, including most media companies and some peer-to-peer critics, to conclude that the networks themselves pose grave threats to the established distribution model. The research that attempts to measure actual monetary loss has been somewhat equivocal. Whilst on paper the existence of these networks results in large losses, the actual income does not seem to have changed much since these networks started up. Whether the threat is real or not, both the RIAA and the MPAA now spend large amounts of money attempting to lobby lawmakers for the creation of new laws, and some copyright owners pay companies to help legally challenge users engaging in illegal sharing of their material.
Hacking
A hacker is someone who who gains illegal access to computers. This action can be done maliciously or with the intent of pointing out possible security risks. Microsoft and the Department of Defense are among those large organizations that have been the target of hackers. Hacking poses a risk to society as hackers can gain access to sensitive financial, personal, or security information that can then be used for extortion or exploited for an attack.
The term is also often applied to computer software or computer hardware programmers, designers and administrators, especially those who are perceived as experts or highly accomplished in this field. A hacker is also a term used for someone who modifies electronics such as ham radio transceivers, printers or even home sprinkler systems for better functionality or performance. The term usually bears strong connotations that may be favorable or pejorative depending on cultural context (see the hacker definition controversy).
Identity theft
With the rising awareness of consumers to an international problem, in particular through a proliferation of web sites and the media, the term "identity theft" has morphed to encompass a broad range of identification-based crimes. The more traditional crimes range from dead beat dads avoiding their financial obligations, to providing the police with stolen or forged documents thereby avoiding detection, money laundering, trafficking in human beings, stock market manipulation and even to terrorism.
According to the non-profit Identity Theft Resource Center, identity theft is "sub-divided into four categories: Financial Identity Theft (using another's name and SSN to obtain goods and services), Criminal Identity Theft (posing as another when apprehended for a crime), Identity Cloning (using another's information to assume his or her identity in daily life) and Business/Commercial Identity Theft (using another's business name to obtain credit)." There are a number of methods used by identity thieves including stealing mail or rummaging through rubbish (dumpster diving), eavesdropping on public transactions to obtain personal data (shoulder surfing), stealing personal information in computer databases [Trojan horses, hacking], infiltration of organizations that store large amounts of personal information, impersonating a trusted organization in an electronic communication (phishing), the use of spam (electronic): Some, if not all spam requires you to respond to alleged contests, enter into "Good Deals," etc., and using another arguably illegal reason to victimize individuals who display their personal information in good faith, such as landlord-related fraud, where the Patriot Act is used to create suspicion on prospective tenants, and then using their personal information to commit fraud. This is a very common practice among slumlords, who violate civil rights and use the right to request background checks to defend their legal policies, which are later used to commit crimes; the laws themselves create this conflict and is a type of identity theft created and enforced by federal law.
The unlawful acquisition of legally attributed personal identifiers is made possible by serious breaches of privacy. For consumers it is usually due to personal naivete in who they provide their information to or carelessness in protecting their information from theft (e.g. vehicle break-ins and home invasions). Surveys in the USA from 2003 to 2006 showed a decrease in the total number of victims but an increase in the total value of identity fraud to US$56.6 billion in 2006. The average fraud per person rose from $5,249 in 2003 to $6,383 in 2006.[3] In the United Kingdom the Home Office reported that identity fraud costs the UK economy £1.7 billion[4] although privacy groups object to the validity of these numbers, arguing that they are being used by the government to push for introduction of national ID cards. Confusion over exactly what constitutes identity theft has led to claims that statistics may be exaggerated.[5]
Internet fraud
The term "Internet fraud" generally refers to any type of fraud scheme that uses one or more online services - such as chat rooms, e-mail, message boards, or Web sites - to present fraudulent solicitations to prospective victims, to conduct fraudulent transactions, or to transmit the proceeds of fraud to financial institutions or to others connected with the scheme.
Internet fraud is committed in several ways. The FBI and police agencies worldwide have people assigned to combat this type of fraud; according to figures from the FBI, U.S. companies' losses due to Internet fraud in 2003 surpassed US$500 million. In some cases, fictitious merchants advertise goods for very low prices and never deliver. However, that type of fraud is minuscule compared to criminals using stolen credit card information to buy goods and services.
Some common types of internet fraud include identity theft, purchase scams, counterfeit money orders, 'phishing' for sensitive information, and clickfraud whereby false hits are generated for websites in order to generate advertising money. Some fraudsters approach merchants asking them for large quotes. After they quickly accept the merchant's quote, they ask for wire transfer information to send payment. Immediately, they use online check issuing systems as Qchex that require nothing but a working email, to produce checks that they use to pay other merchants or simply send associates to cash them.
Spam
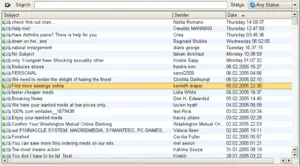
A KMail folder of spam messages.
Spamming is the abuse of electronic messaging systems to send unsolicited bulk messages, which are generally undesired. While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, mobile phone messaging spam, internet forum spam and junk fax transmissions. Spam is also called junk mail. Some email clients or servers have spam filters, which try to delete or move the spam messages.
Spamming is economically viable because advertisers have no operating costs beyond the management of their mailing lists, and it is difficult to hold senders accountable for their mass mailings. Because the barrier to entry is so low, spammers are numerous, and the volume of unsolicited mail has become very high. The costs, such as lost productivity and fraud, are borne by the public and by Internet service providers, which have been forced to add extra capacity to cope with the deluge. Spamming is widely reviled, and has been the subject of legislation in many jurisdictions.
E-mail and other forms of spamming have been used for purposes other than advertisements. Many early Usenet spams were religious or political. Serdar Argic, for instance, spammed Usenet with historical revisionist screeds. A number of evangelists have spammed Usenet and e-mail media with preaching messages. A growing number of criminals are also using spam to perpetrate various sorts of fraud,[6] and in some cases have used it to lure people to locations where they have been kidnapped, held for ransom, and even murdered.[7]
E-mail worms or viruses may be spammed to set up an initial pool of infected machines, which resend the virus to other machines in a spam-like manner. The infected machines can often be used as remote-controlled zombie computers, for more spamming or DDoS attacks. trojans are spammed to phish for bank account details, or to set up a pool of zombies without using a virus.
Spam's direct effects include the consumption of computer and network resources, and the cost in human time and attention of dismissing unwanted messages. In addition, spam has costs stemming from the kinds of spam messages sent, from the ways spammers send them, and from the arms race between spammers and those who try to stop or control spam. In addition, there are the opportunity cost of those who forgo the use of spam-afflicted systems. There are the direct costs, as well as the indirect costs borne by the victims - both those related to the spamming itself, and to other crimes that usually accompany it, such as financial theft, identity theft, data and intellectual property theft, virus and other malware infection, child pornography, fraud, and deceptive marketing. The European Union's Internal Market Commission estimated in 2001 that "junk e-mail" cost Internet users €10 billion per year worldwide. [8]
Relevance of Cybercrime
Cybercrime is becoming a particularly relevant problem to police around the world and to society at large. The growing presence of the internet and computers in homes around the world means that more people are exposed to cybercrime each year. The rise in popularity of broadband internet access also means a greater risk. In an era where all data is being digitized and stored on computers, protecting computers is going to be integral to personal and national security.
Notes
- ↑ Virus/Contaminant/Destructive Transmission Statutes National Conference of State Legislatures. Retrieved May 31, 2007.
- ↑ Zombie PCs: Silent, Growing Threat PC World. Retrieved May 31, 2007.
- ↑ Recent Surveys and Studies, Privacy Clearing House, retrieved June 30,2006
- ↑ What is Identity theft?,Home Office,retrieved June 30,2006
- ↑ Identity Theft Over-Reported,Bruce Schneier, retrieved June 30,2006
- ↑ See: Advance fee fraud
- ↑ SA cops, Interpol probe murder - News24.com, 2004-12-31
- ↑ "Data protection: "Junk" e-mail costs internet users 10 billion a year worldwide - Commission study"
References
ISBN links support NWE through referral fees
- Levy, Steven (1984). Hackers: Heroes of the Computer Revolution. Doubleday. ISBN 0-385-19195-2.
- Turkle, Sherry (1984),The Second Self: Computers and the Human Spirit , New Edition: MIT Press 2005, ISBN 0262701111
- Sterling, Bruce (1992). The Hacker Crackdown. Bantam. ISBN 0-553-08058-X.
- Slatalla, Michelle and Joshua Quittner (1995). Masters of Deception: The Gang That Ruled Cyberspace. HarperCollins. ISBN 0-06-017030-1.
- Dreyfus, Suelette (1997). Underground: Tales of Hacking, Madness and Obsession on the Electronic Frontier. Mandarin. ISBN 1-86330-595-5.
- Verton, Dan (2002). The Hacker Diaries : Confessions of Teenage Hackers. McGraw-Hill Osborne Media. ISBN 0-07-222364-2.
- Graham, Paul (2004). Hackers and Painters. ISBN 0-59-600662-4.
External Links
Credits
New World Encyclopedia writers and editors rewrote and completed the Wikipedia article
in accordance with New World Encyclopedia standards. This article abides by terms of the Creative Commons CC-by-sa 3.0 License (CC-by-sa), which may be used and disseminated with proper attribution. Credit is due under the terms of this license that can reference both the New World Encyclopedia contributors and the selfless volunteer contributors of the Wikimedia Foundation. To cite this article click here for a list of acceptable citing formats.The history of earlier contributions by wikipedians is accessible to researchers here:
The history of this article since it was imported to New World Encyclopedia:
Note: Some restrictions may apply to use of individual images which are separately licensed.
